Opinion
Evacuations from Israel and High-Risk Locations Call +44 (0)1202 308810 or Contact Us →
How the next generation of travel risk management is evolving to meet individual needs
The rise of personalised travel risk management
Cast your minds back to a time when business‑travel advice was little more than a colour‑coded map and a tidy list of “dos and don’ts.” Those days are gone.
The world is moving again – faster than before the pandemic – and today’s travellers are not anonymous employees headed to a pin on a map. They are individuals with intersecting identities, unique expectations, and very real vulnerabilities.
This shift demands that we change the fundamental question. Outside of extreme situations, no longer do we ask, “Is Mexico City safe to travel to?” Instead, we ask, “How will this traveller experience Mexico City, given their medical history, cultural background, or any number of personal factors?”
Adapting risk strategies to meet individual needs
By moving from place‑centric thinking to a people‑first mindset, risk assessments evolve into living profiles that adapt in real time based off the profile. Guidance becomes dynamic, arriving exactly when it matters, whilst privacy is elevated from a compliance tick‑box to a moral imperative.
Consider what happens when we enrich a traveller’s profile – voluntarily, and always under their control – with up-to-date profile attributes, from language fluency to mobility constraints. A powerful risk-intelligence engine can then align raw, real-time data with personal relevance, transforming generic alerts into guidance that feels timely, empathetic, and, above all, useful. Yet none of this works unless trust sits at the core.
A privacy‑first architecture minimises data collection, encrypts what is stored, and gives the traveller full authority over when and how their information is activated. Safeguarding identity traits must become as routine as safeguarding a passport number.
Meeting the expectations of modern travellers
What does this look like on the ground? Let’s think like the people we want to support. Opening an app and seeing a narrative that speaks to you as an individual, perhaps etiquette during Ramadan for a first-time traveller in the Gulf, or a heads‑up on local insulin availability for someone managing diabetes. Practical options could also appear, like the choice to attend a meeting remotely, an alternate routing through a lower‑threat transit hub, or the contact details of a vetted local guide who speaks your native language, or security-recommended restaurants post-meeting, whilst you wait during a delay? No one is forced to reveal private details, but those who opt in unlock an unprecedented layer of protection and confidence.
The influence of next-gen business travellers
As we look ahead, this shift towards personalised, real-time support doesn’t just reflect a technological evolution – it aligns with the rising expectations of the next generation of business travellers. Millennials and Gen Z have already shaped consumer experiences with their demand for relevance, autonomy, and digital convenience. But it’s the emerging cohort of professionals – those coming into leadership in the next five to ten years – who will redefine what good looks like in corporate travel.
They will expect services that anticipate their needs before they arise. For them, hyper-personalised travel risk management won’t be a premium feature; it will be an expected part of the value proposition. This generation won’t just value safety – they’ll expect it to be smart, contextual, and adaptive to their lifestyles, work styles, and identities. The leap from personalisation as a marketing tactic to personalisation as a duty of care will become the new benchmark for progressive employers and security providers alike.
The partnership between human insight and machine intelligence
Where is the frontier? It lies in the partnership between human and machine. Predictive analytics already correlate flight delays, social‑media sentiment, and healthcare capacity in near real time. Algorithms will not be replacing aspects of human judgment, but they can augment our insight, handing us the right information at precisely the right moment. Together, they form a co‑pilot (no pun intended) model in which machines crunch vast, fast‑moving data and humans deliver context, empathy, and final judgment.
A future built on empathy and equality in travel
Our future conversations around travel or crisis, especially when aiming to engage teams across our businesses in a meaningful way, need to be one that centres people, respects their privacy, and empowers everyone to explore the world on equal footing.
Nationwide Protests in Kenya
Intelligence cut off: 15:00 BST 25 JUNE 2025
Demonstrations and clashes with security forces broke out on 25 June in multiple cities in Kenya. The protests, which initially began in Nairobi, have now expanded to other cities including Mombasa, Kisumu, Nakuru and Nyahururu. According to Citizen TV, protests are also taking place in Eldoret, Kakamega, Narok, Busia, Makueni, Nyeri, Laikipia, Nyandarua, Machakos, Homa Bay, and Kirinyaga. Demonstrations are reportedly taking place in at least 20 of the country’s 47 counties. While precise numbers are unconfirmed, thousands of demonstrators have taken to the streets.
In Nairobi, large crowds have occupied parts of the Thika Road highway, and protesters have blocked streets in the Zimmerman area. Demonstrators are reportedly heading towards the city centre, highly likely aiming to reach the parliament. Security forces have deployed tear gas and water cannons to disperse the crowds, particularly in the central business district and outside the city hall. One protester in the capital city was reported to be injured after being struck on the head by a tear gas canister and at least eight people have been shot, according to local news.
Reports from Matuu in Machakos County and Molo in Nakuru County indicate that police have opened fire on protesters, resulting in at least two deaths and several injuries in both locations. Eyewitnesses in Matuu claim that the violence occurred when protesters attempted to enter a police station.
The unrest has led to significant disruptions. Kenya Railways announced the suspension of commuter trains in Nairobi due to the ongoing protests. Additionally, the Kenyan government has taken steps to control the flow of information, with the Communications Authority ordering TV and radio stations to cease live broadcasts of the demonstrations.
Local NTV and KTN stations report that security forces raided their transmission centres and turned off their signals. NetBlocks has reported disruptions to the Telegram messaging service across Kenya, following a government ban on media platforms covering the protests live. Multi-media organisation The Standard Group has declared that it will continue to broadcast despite the attempted ‘news blackout’.
Opposition leaders Kalonzo Musyoka and Eugene Wamalwa have joined demonstrators in Nairobi, laying wreaths outside parliament in honour of those killed during demonstrations last year which killed an assessed 60 people. Former Chief Justice David Maraga is also taking part in the protests. They have called on police to exercise restraint and have condemned police brutality.
SITUATION ANALYSIS
Kenya Protest Unrest Escalates Amid Police Brutality and Travel Risk Concerns
Sporadic protests have been ongoing in Kenya since 9 June, after blogger Albert Ojwang died in police custody the previous day after being arrested for the alleged defamation of the Deputy Inspector General of Police. As protests escalated, the Kenyan National Police also released a statement confirming that a woman miscarried whilst in police custody at Rwanyambo police station in Nyandarua County. On 12 June, the government announced a new finance bill, the trigger for the 2024 protests, although the 2025 iteration was far more conservative.
Protests will likely continue to escalate. On 17 June, the most violent day of unrest before today, a large group of unidentified individuals on motorcycles arrived in the Central Business District in Nairobi armed with makeshift weapons, including whips and clubs, and Kenyan police forces shot a bystander who had been selling face masks with an anti-riot shotgun at point-blank range in the head. There is a realistic possibility that the allegedly pro-government individuals could once again target protesters, which would almost certainly inflame tensions.
These protests constitute the most significant demonstrations since the June-August 2024 protests triggered by the government finance bill. The 2024 protests saw a harsh response from security forces, who were accused of abducting, torturing, and killing civilians believed to be leaders of anti-government protests. At least 60 protesters were killed in total.
The continued perceived harsh repression of demonstrations by security forces, as well as the harming of civilians in custody, has significantly exacerbated tensions, and further footage of security forces using excessive force will almost certainly contribute to demonstrations spreading further.
Today’s date, 25 June, marks the first anniversary of the 2024 storming of parliament. Protesters will likely target the parliament again due to its symbolic value, although there is a heavy security presence around the building, and it has been barricaded with razor wire to prevent protesters from entering.
Despite the introduction of a new finance bill being the trigger for the 2024 protests, it is likely the least contributing factor in this wave of demonstrations. The 2024 finance bill aimed to raise 346 billion Kenyan shillings to pay off the country’s high debt by massively increasing taxes on consumers, such as value-added tax (VAT). Amidst a rising cost of living and inflation, this would have added significant economic pressure on ordinary Kenyans, triggering widespread youth-led protests.
The current wave of unrest, on the other hand, is largely directed towards police brutality, with protesters demanding justice and the resignation of a senior officer they blame for the death of Ojwang, likely suggesting that sustained police brutality and a lack of accountability will continue to sustain violent unrest.
The presence of prominent opposition figures will almost certainly add pressure on President William Ruto, who has seen multiple bouts of unrest since attaining power in 2022. There is a realistic possibility that protests will continue to escalate until Ruto steps down.
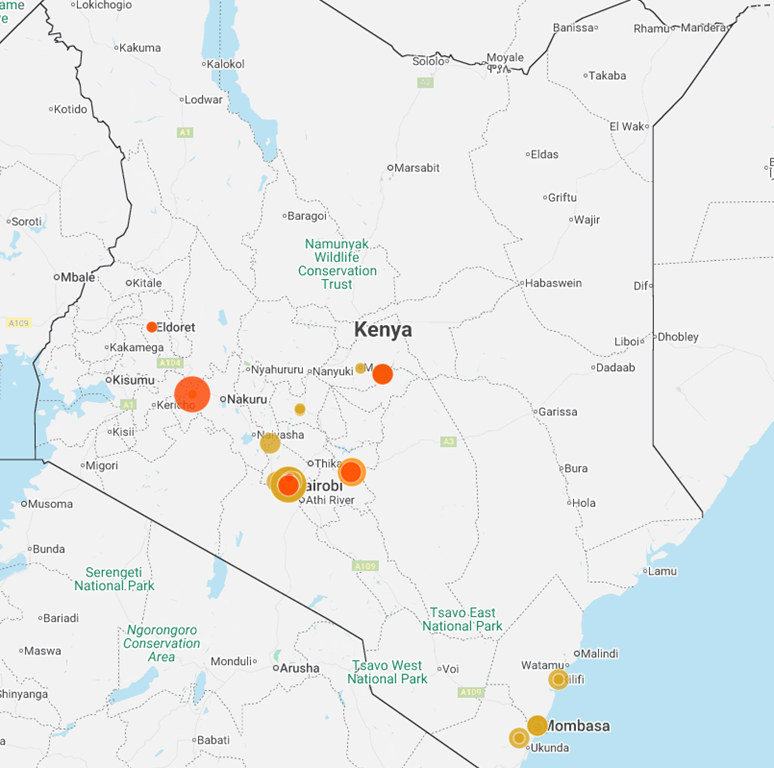
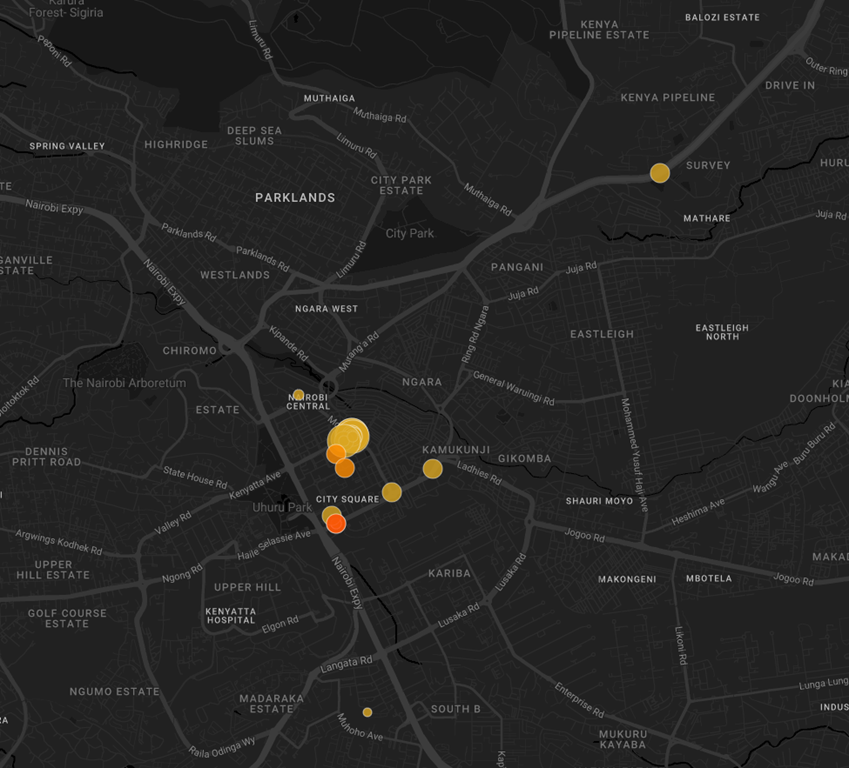
Intelligence Team’s Advice: Guidance During Protests
- Avoid all non-essential travel to Kenya, particularly Nairobi, Mombasa, and Matuu.
- Avoid the central business district in Nairobi, particularly around Kenyatta Avenue, Haile Selassie Avenue, City Hall, and any other wide roads conducive to the staging of protests, as well as all major government buildings such as the Kenyan Parliament or the Governor’s Office.
- Closely monitor announcements from local authorities and media sources for any developments that may severely impact the local security environment.
- Avoid all areas of unrest due to incidental risks to bystanders. If caught in the unrest, travellers should move with the crowd until they find the nearest opportunity to escape. If in a vehicle, look to turn down the nearest road. If driving away is not an option, lock the vehicle and escape on foot.
- Always follow all instructions and orders from security forces. Where possible, avoid areas of active unrest and remain in a secure accommodation.
- Prolonged civil unrest can disrupt travel, especially if protesters begin targeting airports. Travellers should have contingency measures in place, including evacuation plans and reliable access to food, water and medication.
- Have emergency contact numbers saved on your phone. These should include the local authorities, medical facilities and any consular support. Ensure that mobile phones are charged in case of any losses in electricity.
- If caught in the vicinity of a security incident, seek shelter immediately and leave the area if safe to do so. Continue to adhere to all instructions issued by authorities and obey any security cordons in place.
- The overall security situation in Kenya, including Nairobi, is likely to remain severe in the coming days.
- Monitor the Solace Secure platform and trusted local media for updates relevant to the conflict.

Live Webinar: Israel-Iran Conflict High-Priority Briefing
Strategic Intelligence for Global Security & Risk Leaders
As the conflict between Israel and Iran intensifies, with confirmed US airstrikes on Iranian nuclear facilities, the risk of regional escalation is rapidly increasing. For organisations with global operations, personnel in affected areas, or exposure to Middle East supply chains, access to trusted, real-time insight is essential.
Last Thursday, Solace Global’s intelligence team delivered a high-priority briefing to clients, providing clarity on the evolving security landscape. The session explored Israel’s strategic intent, Iran’s military response, and the rising likelihood of further US involvement.
INTELLIGENCE ANALYSIS
Topics Covered in the Middle-East Security Briefing
Delivered by Head of Intelligence Mark Overington and Chief Customer Officer Robert Aldous, the session highlighted:
- Israel’s objective to degrade Iran’s nuclear and ballistic missile capabilities
- Tactical airstrikes on high-value targets, including infrastructure and security networks
- Iran’s ongoing retaliatory missile attacks and use of regional proxy forces
- Potential risks to international shipping, airspace, and supply chain continuity
- The operational outlook for US assets in Iraq, Syria, and the Gulf states

Mark Overington
Head of Intelligence

Robert Aldous
Chief Customer Officer
LIVE WEBINAR
Gain Access to Next Israel-Iran Security Briefing
On June 21, at approx. 2300 GMT, the US Air Force & Navy carried out attacks at three Iranian Nuclear sites. The attack has been confirmed by US President Donald Trump following days of tit-for-tat strikes between Israel and Iran.
Solace Global clients will receive these alerts and extended assessment through Solace Secure and through the GIS Subscription. We are advising clients on all potential scenarios, ensuring businesses are prioritising their people, assets and their Operational Resilience.
Next Israel-Iran Conflict Security Briefing: Thursday 26th June 2025
Solace Global will host a follow-up briefing this Thursday, offering updated analysis and forward-looking scenarios to inform your planning.
To access this and future sessions, sign up to our intelligence subscription service
Israel Targets Iran’s Nuclear Sites in Major Attack
Intelligence cut off: 10:00 BST 13 JUNE 2025
At approximately 03:30 local time on 13 June, the Israeli Air Force (IAF) conducted a series of coordinated airstrikes targeting multiple locations and senior figures across Iran associated with Iran’s nuclear program as part of ‘Operation Rising Lion’.
Targets included the Natanz Enrichment Complex; nuclear-related facilities in Qom, Markazi, Kermanshah, and Hamadan; and multiple locations in Tehran. Israeli sources have also claimed to have completed a ‘broad strike’ on Iranian air defence systems in western Iran, resulting in the destruction of dozens of radars and surface-to-air missile launchers (SAMs).
Iranian state media claim the strikes resulted in dozens of fatalities and casualties. Among those reportedly killed are Hossein Salami, Commander-in-Chief of the Islamic Revolutionary Guard Corps (IRGC), Mohammad Bagheri, Chief of Iranian Armed Forces General Staff, and senior nuclear scientists Mohammad Mehdi Tehranchi and Fereydoun Abbasi.
The strikes form part of a broader Israeli strategy aimed at dismantling the IRGC leadership and disrupting Iran’s nuclear programme. The attack follows days of escalating tensions, fuelled by stalled US-Iran negotiations over Iran’s nuclear program.
Israel has declared a state of emergency, closed its airspace, suspended operations at Tel Aviv’s Ben Gurion International Airport (TLV) indefinitely, and Prime Minister Benjamin Netanyahu has warned Israeli citizens that they may have to spend extended periods within air raid shelters. Public offices and educational institutions across the country will remain closed until at least 20:00 local time on 14 June. Emergency services have been placed on high alert, and the Israeli Defence Forces (IDF) have bolstered their presence in the Occupied West Bank
Iranian Supreme Leader, Ali Khamenei, has vowed that Israel will face ‘severe punishment’ for the strikes on its nuclear program. On 13 June, Iran launched 100 uncrewed aerial vehicles (UAVs) in response to the Israeli strikes.
Airspace restrictions have been imposed across Iraq, and flight operations at all Iraqi airports have been suspended as a precautionary measure. Multiple reports indicate that explosions have occurred in various locations across Iraq. Although the nature and cause of these incidents remain unconfirmed at this stage, uncorroborated reports suggest facilities associated with Iranian proxy forces have been targeted.
Jordan has closed its airspace and has stated that it will not tolerate violations of its airspace. Air raid sirens have been activated in the capital, Amman, and Jordanian state media has announced that the Jordanian Armed Forces have intercepted drones that have entered its airspace. Jordanian officials have warned citizens not to gather in the street due to the threat of falling debris from intercepted aerial threats.
US Secretary of State Marco Rubio issued a statement affirming that Israel “took unilateral action against Iran” in what Israel has described as a necessary act of self-defence. Israeli Prime Minister Benjamin Netanyahu characterised the pre-emptive strikes as a military operation aimed at “rolling back the Iranian threat to Israel’s survival.”
Despite repeated denials from senior US officials regarding any direct involvement in the strikes, Iran’s Islamic Revolutionary Guard Corps (IRGC) has accused the United States of assisting in the operation. IRGC officials have vowed a “strong response from Iranian forces” against Israel and US forces in the region.
The International Atomic Energy Agency (IAEA) announced via social media platform X, that they are “in contact with Iranian authorities regarding radiation levels” that may increase as a result of the attack.
INTELLIGENCE ANALYSIS
Airspace Closures Widen as Iran-Israel Conflict Threatens Regional Aviation
The most immediate threat posed by the escalation is of Iranian retaliation strikes against Israel. Reports indicate that the first wave of Iranian UAVs was completely intercepted by Israel or regional forces. However, the first wave was likely an initial response and will almost certainly be followed by larger waves of layered attacks consisting of UAVs and ballistic missiles conducted by Iranian conventional forces.
Israeli attempts to degrade Iranian air defence likely indicate that further Israeli strikes on Iran are impending, which will almost certainly provoke further Iranian retaliation. Given the strategic importance of Iran’s nuclear program, it is likely that future Iranian attacks will be larger than those observed in April and October 2024.
Iranian proxy forces in the region will highly likely form part of Iran’s retaliation against Israel. The Houthi Movement in Yemen will likely conduct missile and drone attacks targeting southern and central Israel. Iranian proxies in Iraq will likely launch drones at Israel. Despite much of its military infrastructure in southern Lebanon having been dismantled, Hezbollah still maintains a credible arsenal of rockets, missiles, and drones, and is likely to conduct attacks primarily against northern Israel.
Whilst Israeli air defence is comprehensive and highly capable, previous Iranian strikes and proxy attacks have managed to successfully penetrate Israel’s defences. Furthermore, there is a high threat from falling debris caused by successful interceptions across Israel, Jordan and Iraq. The resumption of hostilities will almost certainly result in significant airspace closures, and air travel disruption will continue across the region, complicating evacuation.
So far, the US Trump administration has sought to distance itself from the Israeli operation. However, Iran’s foreign ministry has stated that the US will also be responsible for the “dangerous consequences” of Israel’s “adventurism”, and there are indications from Iranian television broadcasts that Iran will now not participate in the scheduled negotiations with the US on 15 June.
The most likely US targets to be attacked are the US military bases in Iraq and Syria. Moreover, it is likely that the Iraq-based Iranian proxies, the Popular Mobilisation Forces (PMFs), will engage in rocket attacks against these US bases. Such attacks would highly likely lead to retaliation from the US, threatening to further escalate the conflict.
Should Hezbollah resume direct conflict with Israel, this would almost certainly be met with Israeli airstrikes against Hezbollah targets across Lebanon, particularly in the Dahieh suburbs of southern Beirut, the Beqaa Valley, and south of the Litani River.
As the Royal Jordanian Air Force has already engaged in interceptions of Iranian aerial threats over Jordan’s airspace, this poses an immediate threat of debris in Jordan. Furthermore, Jordanian involvement has previously led to civil unrest in Amman, and this will likely occur again, particularly in the vicinity of the Israeli and US embassies.
It is unlikely but possible that retaliation from Tehran and its proxies will develop to involve strikes against US military bases in the Gulf states, particularly Kuwait and Bahrain, but also the United Arab Emirates (UAE) and Saudi Arabia. Gulf state leaders have made distinct efforts to condemn the Israeli strikes, with Iranian officials having previously threatened attacks against US interests across the region in the event of escalation.
For the Gulf states, the highest impact potential outcome is the development of the conflict into a protracted regional conflict involving the US, characterised by the targeting of energy facilities across the region. Strikes against Gulf oil facilities are a key capability Iran can deploy against US interests in the region and threaten to disrupt the global economy.
Travel Risk Advice: Safety Guidelines for Los Angeles, USA
- Avoid all non-essential travel to Israel, Iran, the Occupied Palestinian Territories (OPT), Jordan, and Iraq.
- Ensure that you contact and register with your local embassy or consulate if stranded in Israel, Iran, OPT, Jordan, or Iraq.
- Travellers in Israel should familiarise themselves with the nearest air raid shelter and ensure that they have downloaded applications that provide early warning of incoming threats, such as Home Front Command or Red Alert.
- Avoid all military installations, government buildings, and key infrastructure, which may constitute potential targets.
- Ensure you have robust evacuation, communication, and contingency plans in place.
- Adhere to all instructions issued by authorities.
- Expect the security situation in the region to remain highly unstable in the immediate future. There is an increased risk of further strikes, terrorist attacks, and civil unrest.
- Prepare an essential “go-bag” containing, at a minimum, travel documents, cash, medications, basic supplies, and communication devices in case of evacuation.
- Keep emergency contact numbers saved on your phone, including those for local authorities, medical services, and consular assistance. Ensure mobile devices are fully charged in case of potential power outages.
- Closely monitor trusted local news reports and government alerts. Unverified claims and disinformation will almost certainly be widely propagated on social media and unvetted sources.
Subscribe to free weekly intelligence

Air India flight AL171 crashed during take-off in Ahmedabad
Intelligence cut off: 11:15 BST 12 June 2025
On 12 June, Air India flight AI171 crashed during take-off from Sardar Vallabhbhai Patel International Airport (AMD) in Ahmedabad in India’s Gujarat province. The Boeing 787-8 Dreamliner had a capacity of 256 seats onboard and was bound for London Gatwick Airport (LGW). 242 people are believed to be onboard, including the two pilots and 10 cabin crew staff. According to reports, there were 169 Indian nationals, 53 Britons, seven Portuguese, and one Canadian on board.
The plane departed at 13:38 local time (08:08 UTC), and the signal was lost less than a minute after take-off, while the plane was 625 feet (190 metres) high. The plane was due to land at 18:25 local time (17:25 UTC). According to social media footage, the plane crashed outside the airport perimeter in a residential area near the Civil Hospital Ahmedabad, southwest of the airport. The plane, which had a fuel load of 126,000 litres, caught fire after crashing and black smoke was seen rising from the crash site. While casualty figures are currently unclear, there appear to be some survivors.
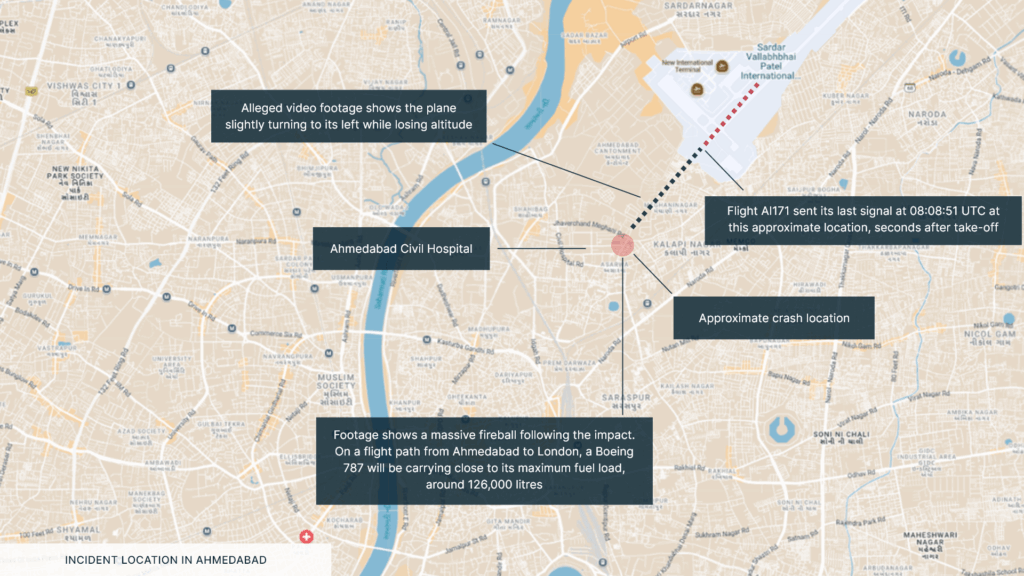
India’s aviation minister has stated that rescue teams have been mobilised. The Chief Minister of Gujarat has stated that officials have been instructed to carry out ‘immediate rescue and relief operations’ and to make arrangements on a ‘war footing’. A green corridor for injured passengers has been arranged to ensure priority at the hospital. The Directorate General of Civil Aviation (DGCA) has been sent from Delhi to investigate the cause of the incident.
While the cause of the crash is unclear, the loss of signal shortly before the crash indicates a critical systems failure is likely. There was high visibility of six kilometres, and there were light surface winds, so a weather-induced accident is unlikely. An investigation into the cause of the incident will almost certainly be quickly carried out by the DGCA and Aircraft Accident Investigation Bureau (AAIB), who will attempt to recover the black boxes (flight data and cockpit voice recorders) to determine the nature of the crash.
The last fatal plane crash in India occurred at Kozhikode International Airport (CCJ) in 2020, where the plane skidded off the runway and crashed into the ground. 21 people were killed and over 100 were injured.
Prime Minister Narendra Modi will likely declare a day of national mourning over the victims of the crash as casualty figures become clear. If the cause of the crash is deemed to be due to poor maintenance, regulatory failures, or negligence, demonstrations are likely to occur outside the airport or outside government buildings.
There will almost certainly be significant flight disruptions over the coming hours. Flight tracking sources indicate that incoming domestic flights have been diverted back to their airports of origin, and departure flights have been cancelled.
INTELLIGENCE TEAM’S GUIDANCE
Travel Risk Advice: Safety Guidelines
•Closely monitor local news reports, government alerts, and the Solace Secure platform and trusted local media for updates. There is a high likelihood of disinformation being published regarding the nature of the plane crash.
•Follow Air India’s X page found here for the latest information regarding the incident.
•Expect significant transport disruptions near the airport and crash site. Where possible, use alternative routes.
•Confirm all flights with your airline if scheduled to depart from or arrive at Sardar Vallabhbhai Patel International Airport.
•If stranded or delayed, contact your airline’s 24/7 helpline to arrange alternative flights.
•If staying near the airport or crash site, expect transit delays due to crash-related roadblocks. Consider moving hotels to somewhere away from the airport.
•Expect reduced capacity for emergency services in the Ahmedabad area over the coming hours.
Subscribe to free weekly intelligence

Anti-ICE Protests Intensify Across US Cities
Intelligence cut off: 12:30 BST 10 JUNE 2025
As of 10 June, demonstrations against the Immigration and Customs Enforcement (ICE) agency entered their fourth consecutive day in Los Angeles. The unrest began on 6 June, triggered by ICE raids in Los Angeles that resulted in the arrest of 118 people.
While Los Angeles has seen the most severe unrest so far, the protests have spread to multiple US cities, including Santa Ana, San Francisco, Austin, New York, Dallas, Houston, San Antonio, Chicago, Washington D.C., and Seattle.
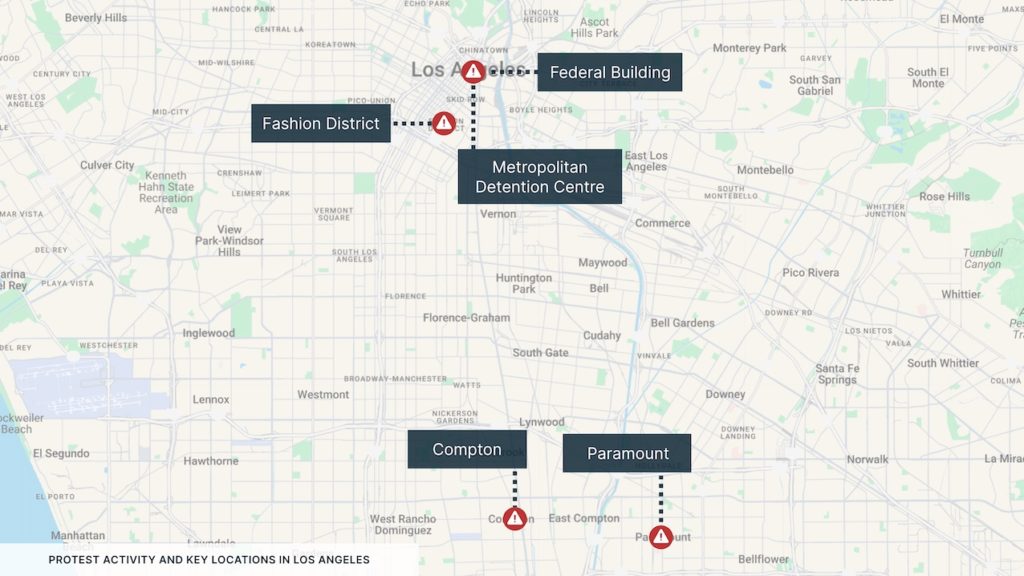
In Los Angeles, the protests have seen the most violence in the Downtown area, which authorities have declared an “unlawful assembly” area. The unrest has resulted in vandalism, the erection of barricades, reports of looting, and the throwing of projectiles, including Molotov cocktails, at law enforcement. Furthermore, both local law enforcement and federal forces have deployed tear gas, rubber bullets, stun grenades, pepper spray and pepper balls, and used mounted units as part of crowd control operations.
The worst-impacted locations in Los Angeles include the area around the Metropolitan Detention Center, with demonstrators blocking the nearby Highway 101 and setting fire to Waymo driverless taxis; the Los Angeles Federal Building; the Fashion District; Paramount; and Compton.
On 7 June, US President Donald Trump ordered the deployment of 2,000 National Guard troops to the Los Angeles area, which has since been doubled to 4,000. 700 US Marines have been additionally activated for potential deployment; however, they are unable to directly participate in civilian policing unless the Insurrection Act is invoked, which the Trump administration has not done as of the time of writing.
The deployment of the National Guard and Marines has been met with staunch opposition by the Governor of California, Gavin Newsom, with the National Guard deployment being the first without a governor’s approval since 1965.
In the days following the initial outbreak of unrest in Los Angeles, “solidarity” protests broke out in multiple other US cities. Of these, the most significant protests took place in San Francisco, where close to 150 people were arrested following violent clashes near a downtown ICE office; Santa Ana, where tear gas and flashbangs were used against protesters outside the Santa Ana Federal Building; and New York, where 24 protesters were arrested at Trump Tower.
INTELLIGENCE ANALYSIS
White House Escalates Response to Unrest: Marines and National Guard Sent to Los Angeles
The civil unrest has been characterised by the relatively small size of demonstrations, compared to, for example, the Black Lives Matter protests. However, despite the low attendance, the level of disruption has been pronounced, highly likely due to a combination of both the propensity for the attendees to conduct direct action and due to the forceful response by authorities.
It is highly likely that protests will continue in the following days, given the so far established cycle of escalation. ICE raids were the initial primary trigger for the unrest, with the protests in Paramount, for example, being triggered by rumours of an ICE raid at a Home Depot. It is almost certain that further ICE raids will continue to act as a trigger for localised demonstrations in major US cities, with protesters attempting to stop the mass detentions through direct action.
As the protests progressed, however, additional triggers for escalation materialised. First, the arrest and hospitalisation of David Huerta, the President of the Service Employees International Union (SEIU), acted as a trigger for protests within the organised labour movement, with union chapters coordinating demonstrations.
Second, the deployment of the National Guard and then the proposed deployment of active-duty US Marines have catalysed so-called “solidarity” protests in other US cities.
A key trigger for further escalation would be the unlikely but possible scenario of the Trump administration invoking the Insurrection Act, which would allow the deployment of the armed forces for law-enforcement activities.
The most likely hotspots for demonstrations (and associated violent clashes with authorities) continue to be federal facilities, particularly ICE offices and federal detention centres, and areas where ICE raids are being conducted (with social media being a key means of enabling this).
There is a high risk of collateral violence to bystanders at these protests, given the levels of violence thus far, and they should be avoided as far as possible. Furthermore, the unrest has resulted in significant transport disruptions, with major freeway closures such as the 101 Freeway being closed in Los Angeles.
Travel Risk Advice: Safety Guidelines for Los Angeles, USA
- Avoid all protest areas in Los Angeles, particularly areas around the Metropolitan Detention Centre, the Fashion District, Compton, and Paramount.
- Closely monitor local news reports, government alerts, and the Solace Secure platform and trusted local media for updates relevant to the demonstrations.
- Follow the Los Angeles Police Department’s X page found here for the latest information regarding protest areas and associated traffic disruptions.
- Where possible, use alternative routes to steer clear of protest locations and avoid public transport.
- If in the vicinity of a protest, try to leave if it is safe to do so. Always abide by authority and police directions.
- If you are in a crowd and unable to leave, take precautions to minimise the risk of a crowd crush. These include staying upright, moving away from all hard barriers, going with and not against the crowd, and holding your arms at chest level in a boxer-like stance to relieve pressure.
- Ensure that you always carry personal identification documents or copies.
- Ensure knowledge of important contact numbers. These should include at least the local emergency number(s) and contacts for your local embassy or consulate.
- Expect a heightened security presence to continue beyond 10 June. This will likely result in protracted transport disruptions.
Subscribe to free weekly intelligence

Travel Advice and Risk Mitigation Measures for the NATO Summit
Executive Summary
- The NATO Summit will take place in The Hague on 25–26 June 2025, attracting around 8,500 attendees, including heads of state, ministers, and international delegates.
- Heightened security and large-scale deployments will significantly affect daily life across the Randstad region from 22 to 27 June.
- Extensive airspace restrictions and runway closures at Schiphol Airport will disrupt commercial flights, with up to 30% reduction in capacity.
- Road closures on key routes around The Hague, Amsterdam, and Rotterdam will lead to severe congestion and travel delays.
- Demonstrations and counter-events are expected, with an increased risk of disruption near designated protest zones.
- There is an elevated cyber threat environment, with risks including disinformation, surveillance, and network intrusions.
- The Netherlands remains at a “substantial” terrorism threat level; lone actor attacks are more likely than coordinated group actions.
- Business and government travellers should adopt robust security measures and avoid affected areas unless operationally required. Learn more about Executive Protection and Secure Journey Management.

SITUATION SUMMARY
What to Expect for NATO Summit in The Hague
On 25 and 26 June 2025, the annual NATO Summit is set to take place in The Hague, Netherlands, for the first time since the founding of NATO in 1949. The event is set to host approximately 8,500 visitors, consisting of approximately 45 heads of state, 45 foreign ministers, 45 defence ministers, 6,000 delegates, 2,000 journalists, and 800 guests.
The summit is occurring within the context of the Trump administration consistently distancing itself from NATO, major developments in the war in Ukraine, and European NATO leaders increasingly discussing the necessity for capable European defence and deterrence against Russia that is independent from US support. While an official agenda has not been published, the summit will almost certainly address defence funding and membership status for its member states, in addition to boosting NATO defence capabilities.
The summit will almost certainly trigger significant travel disruptions and heightened security threats in the Randstad area from 22 to 27 June.
How will security be managed during the NATO Summit in The Hague?
Numerous security measures will be implemented during the summit. 27,000 police officers, approximately half of the Dutch National Police force, are set to be deployed across the two days, supported by 5,000 armed forces personnel and special forces teams on 24-hour standby.
Patriot air defence systems and counter-drone installations will reportedly be used to defend the summit from aerial threats. F-35 fighter jets and Apache patrols will also occur over the city and along the coast. An air exclusion zone will operate over a 22-kilometre stretch of coast between the Hook of Holland and Noordwyk.
Security will be prioritised at the World Forum (where the summit will be taking place), Huis ten Bosch (where the leaders will dine), and the Grand Hotel Huis ter Duin (where President Donald Trump will likely reside).
TRAVEL RISKS
Will flights and public transport be affected during the NATO Summit?
Significant travel disruptions should be expected during the week of the NATO Summit. The World Forum is approximately 30 minutes from two of the Netherlands’ largest airports, Amsterdam Schiphol Airport (AMS) and Rotterdam The Hague Airport (RTM).
Significant airport disruptions are almost certain, particularly at Schiphol, where the Polderbaan Runway will be closed to air traffic between 21 and 27 June. With the Buitenveldertbaan Runway currently under maintenance, commercial air traffic will be reduced by between 25 and 30 per cent during this period, with an estimated 100,000 passengers likely to face cancellations or rescheduling. This may increase traffic at The Hague airport as flights reroute.
Transport disruptions will also affect road travel. Authorities are set to close roads to transport world leaders on the A4, A5, A44, N44, and N440 from 22 to 27 June, which will almost certainly disrupt travel between Amsterdam, The Hague, and Rotterdam. The N434 will also be closed in the afternoon and evening of 25 June. Local and regional roads around the Hague, Wassenaar, Katwijk, Noordwijk, Haarlemmermeer, Leiden, and Rotterdam will also be closed, making several areas difficult to reach. Large-scale diversion routes have been set up.
The most congested periods will highly likely be late 23 June, early 24 June, and late 25 June. Triple the normal traffic volumes are to be expected at least 450 kilometres around the periphery of the World Forum. In anticipation of major traffic disruptions, the Dutch government have warned people to avoid the central Randstad region between 23 and 26 June, advising residents to work from home as much as possible and to use public transport if travel is necessary. Public transport will likely be overcrowded as people avoid driving disruptions and follow government advice, likely leading to an increase in petty crime.
Are protests expected during the NATO Summit in the Netherlands?
There will almost certainly be civil unrest in the days around the event. An international protest has already been organised for 22 June at Koekamp near the Hague Central Station by the Dutch Counter Summit Coalition for Peace and Justice. A “Counter Summit” conference has been scheduled for 21 to 22 June, which may draw additional protesters to The Hague.
Authorities have designated specific areas for demonstrations, with small-scale protests allowed around the World Forum, and larger-scale protests limited to the Malieveld. While the demonstrations will likely be peaceful, the high levels of security during the summit raise the possibility of clashes between protesters and security forces.
What cyber risks and espionage threats are linked to the NATO Summit?
There will likely be a heightened risk of cyberattacks and espionage, perpetrated mostly by Russia. Typical hybrid threats from Russia, in its campaign to gain a competitive advantage over its Western adversaries, include disinformation campaigns, sabotage, and cyberattacks.
Disinformation, particularly on social media platforms like X, will likely be used to sow confusion and undermine confidence in authorities; fake security, transportation, or health and safety alerts online are a potential method. Espionage could additionally target business travellers as hostile actors attempt to access confidential and proprietary information. Public Wi-Fi networks are a likely target, with perpetrators aiming to steal personal data or credentials.
Cyberattacks and sabotage targeting essential services such as transport infrastructure pose another threat, with perpetrators incentivised to cause disruptions to reduce the summit’s credibility.
Is there a terrorism threat during the NATO Summit 2025?
There is an increased threat of terrorism, resulting from the high visibility of the event. Before the event was announced, the Netherlands’ National Coordinator for Security and Counterterrorism (NCTV) placed the country at a threat level four, indicating a “substantial” risk of terrorist attack.
A recent attack took place on 27 March 2025, where a mass stabbing occurred near Dam Square, injuring five individuals. The perpetrator was a Ukrainian citizen from Donetsk; the motive is still unclear, but he has been charged with attempted murder with terrorist intent.
While the high levels of security likely lower the risk of coordinated attacks by violent extremist organisations (VEOs), lone actor attacks are more difficult to mitigate against and predict for intelligence agencies. Lone actors typically use unsophisticated opportunistic methods, including vehicle ramming, knife attacks, and arson.
MITIGATION
Travel Advice and Risk Mitigation Measures for the NATO Summit in The Hague
- Plan for significant travel disruptions. Check with your airline to confirm if your flight is still operating as scheduled.
- Adhere to instructions issued by authorities. Carry valid identification at all times.
- Unless specifically travelling to the event, avoid travelling near the World Forum, Huis ten Bosch, or Grand Hotel Huis ter Duin.
- Avoid the Diplomatic Zone around the Peace Palace, International Court of Justice, and embassies, which may be heavily restricted.
- Avoid areas where demonstrations are taking place.
- Avoid overt displays of wealth and be mindful of pickpockets, particularly in large crowds and on public transportation.
- Stay up to date with local news outlets. The Municipality of The Hague (Gemeente Den Haag) website typically publishes advisories regarding road closures and security perimeters.
- Business travellers in sensitive industries should assume that they are being targeted by espionage and implement the appropriate security protocols and countermeasures. These include avoiding public Wi-Fi networks; using multi-factor authentication, VPNs and loaner devices; and establishing clear red lines for what information they are willing to share and bring in-country. Learn more →

Request an Executive Protection Quote
Contact us to discuss secure transportation during Nato Summit 2025
Vehicle Rams Crowd in Central Liverpool After Premier League Victory Parade
Intelligence cut off: 10:45 BST 27 MAY 2025
At approximately 18:00 local time on 26 May, a vehicle drove into a crowd of football supporters in Water Street, central Liverpool. The incident occurred as supporters were celebrating Liverpool’s victory in this year’s Premier League, with a parade in the city centre having just concluded when the incident happened. Videos taken at the location show a dark van repeatedly driving into the crowd of supporters before coming to a stop.
The responding police stated they had made an arrest in connection with the incident. A 53-year-old individual from the local area is currently alleged to have been responsible for driving the vehicle into the crowd. As of the time of writing, authorities have confirmed that at least 47 people have been injured, 27 of whom were transported to nearby hospitals.
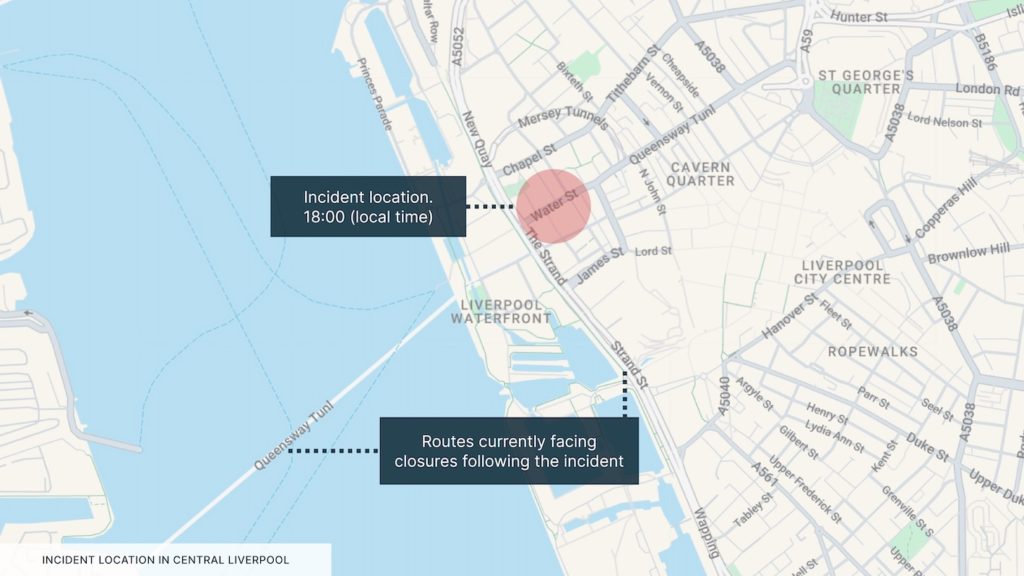
Police stated that they are not currently treating the incident as a terror-related act. They moreover stated that they consider it an “isolated incident” and are not looking for further suspects.
INTELLIGENCE ANALYSIS
Authorities Dismiss Terror Motive in Liverpool Incident Amid Misinformation Concerns
Eyewitness accounts and video footage captured in the immediate prelude to the incident indicate that the car ramming likely occurred after an altercation erupted between the suspect, who had entered the newly reopened street, and supporters who had surrounded his vehicle. The information available thus far likely indicates a lack of premeditation or terror-related motive for the attack.
In the aftermath of the attack, there have been several reported cases of disinformation being spread online regarding the perpetrator’s identity and motive for the attack. These are almost certainly meant to provoke retaliatory violence against minority communities in the UK and mirror a phenomenon already observed in the immediate aftermath of the stabbing attack in Southport in July 2024.
As of 27 May, UK authorities have taken several steps to combat the spread of misinformation, and a decrease in the engagement of disinformation narratives on select social networks has been observed. Nevertheless, a remote possibility of “retaliatory” attacks following the incident remains extant.
Travel Risk Advice: Safety Guidelines for Liverpool, UK
- In Liverpool, adhere to all safety directives, avoid all gatherings and the area of Water Street, and plan for alternative routes.
- Closely monitor local news reports and government alerts.
- Monitor Merseytravel for updates on public transport services and road closures in Liverpool.
- If you are caught in the vicinity of an attack, follow RUN – HIDE – TELL.
- If caught in the vicinity of an attack, seek immediate hard cover and leave the area if safe to do so. Continue to adhere to all instructions issued by authorities and obey any security cordons in place.
- Ensure that you always carry personal identification documents or copies.
- Have emergency contact numbers saved on your phone. These should include the local authorities, medical facilities and any consular support. Ensure that mobile phones are charged in case of any power outage.
- Monitor the Solace Secure platform and trusted local media for updates relevant to the conflict.
- The emergency number in the United Kingdom is 999.
Subscribe to free weekly intelligence

What is Nakba Day and Why is it Significant?
Intelligence cut-off: 17:00 GMT 14 May 2025
The 77th anniversary of the Nakba falls on 15 May 2025. “Nakba” is an Arabic term that translates to “catastrophe” and is used to describe the mass-displacement of Palestinians that resulted from the 1947-49 war, affecting approximately 750,000 individuals. The Nakba is an important event in shaping Palestinian identity and has a significant influence on Palestinian diaspora politics.
Where Did the Largest Nakba Day Protests Occur in 2024?
The 2024 Nakba Day protests were the most extensive to occur in connection with the commemoration. Several gatherings that were attended by tens of thousands of attendees were recorded in several cities, with hotspots concentrated in Western Europe and in large North American urban centres. On 18 May 2024, protests in London were attended by an estimated 250,000 people, with smaller gatherings in Manchester, Leeds, Cardiff, and Edinburgh among other cities. Large-scale protests were likewise recorded in Barcelona, Madrid, Milan, Bologna, Berlin, Paris, Marseille, Toulouse and other large European urban centres.
In North America, Nakba Day coincided with several large-scale protests, with major demonstrations occurring in cities including New York City, Toronto, Washington, D.C., Miami, Cleveland, and Portland.
Why Are Universities Central to These Demonstrations?
In both Europe and North America, university-based groups have been particularly active in spearheading the unrest, making campuses hotspots of demonstrations. Student groups at, among others, Columbia University in New York, Sorbonne and Sciences Po, in Paris, and Amsterdam University staged large-scale demonstrations and direct action in connection with pro-Palestine unrest.
Nakba Day Protests across the Middle East in 2024
Nakba Day protests are also common in the Middle East, due to the commemoration’s lasting political importance. In 2024, particularly notable demonstrations occurred in Beirut, Tunis, Amman, and Rabat. In Israel, protests were concentrated in Tel Aviv, with the local Tel Aviv University being a focal point for the demonstrations.
The ongoing conflict in Gaza has almost certainly contributed to driving larger Nakba Day protests in countries and regions that have not previously been as impacted by pro-Palestinian protests as Western Europe, the Middle East, and North America. In the Asia-Pacific region, for instance, protests were held in cities like Sydney and Melbourne in Australia, and Osaka and Tokyo, Japan.
Violent Incidents during Protests
During the 2024 Nakba Day protests, episodes of violence between protesters and responding security forces were recorded at some locations. For instance, protests in Brooklyn, New York, resulted in around 40 arrests as violent clashes broke out between police and protesters. In Berlin, protests were halted due to the deployment of fireworks, posing a threat to bystanders. In London, local police arrested several people over violent chants and slogans.
Full Report with analysis and travel risk advice included in Global Intelligence Subscription
India Conducts Airstrikes in Pakistan-Administered Kashmir After Pahalgam Terror Attack
Intelligence cut off: 10:00 BST 07 MAY 2025
At approximately 00:30 local time on 7 May, the Indian Air Force (IAF) conducted airstrikes against nine different locations in both Pakistan-administered Kashmir and Pakistan.
Among the areas targeted are Muzaffarabad, Kotli, and Bagh in Pakistan-administered Kashmir, and Sialkot, Sarjal/Tehra Kalan, Muridke, and Bahawalpur in Pakistan. Pakistani Armed Forces (PAF) spokespersons have claimed the attacks resulted in at least 26 dead and 46 injured.
The strikes, codenamed Operation Sindoor, were carried out as part of India’s broader strategy to dismantle terrorist infrastructure in neighbouring Pakistan, following the 22 April attack in Pahalgam. India’s Defence Ministry has declared that it targeted nine different sites considered “terrorist infrastructure” in a “focused, measured, and non-escalatory” manner, with sites allegedly linked to proscribed militant groups like Lashkar-e-Taiba and Jaish-e-Mohammed. No Pakistani military sites were reportedly targeted. Indian officials issued a list of alleged militant camps targeted across Pakistan in the aftermath.
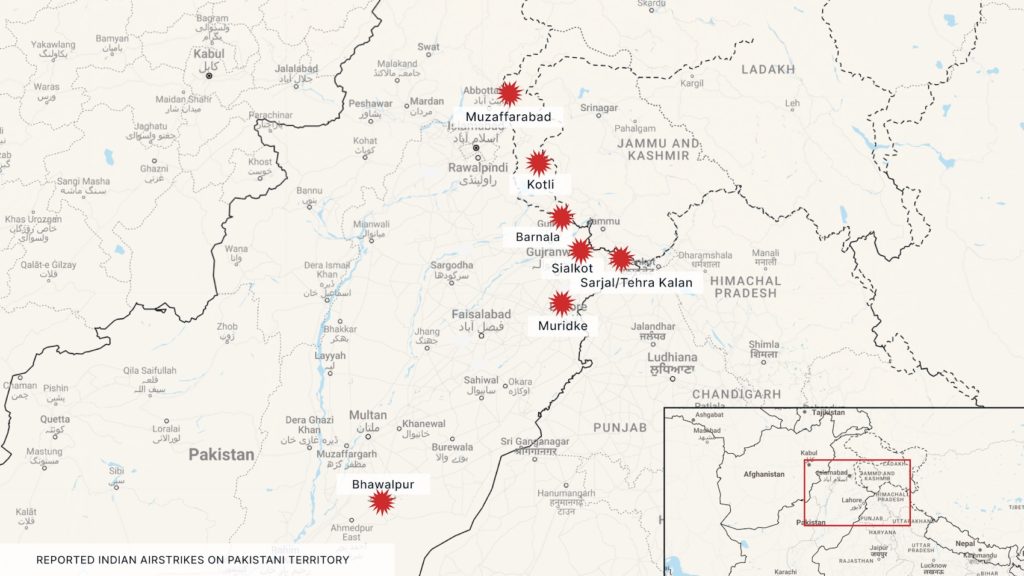
In retaliation, Pakistani forces conducted cross-border shelling in Kashmir, reportedly killing and injuring several civilians, and have claimed to have downed five Indian military aircraft. Flight operations at Karachi’s Jinnah International Airport (KHI) and Lahore’s Allama Iqbal International Airport (LHE) were temporarily suspended overnight due to heightened risks posed by the ongoing aerial engagements.
Similar restrictions have also been implemented across nine airports in northern and western India, with Air India suspending flights to Jammu and Srinagar in Kashmir, Leh, Chandigarh, Jodhpur, Amritsar, Bhuj, Jamnagar, and Rajkot through 10 May.
Air France has suspended flights over Pakistan. Several other airlines have followed suit, re-routing or cancelling flights to and from Europe.
Pakistan’s Prime Minister, Shehbaz Sharif, has described the strikes as an “unprovoked act of war” and referred to the Indian claims of targeting terrorist camps as “false”. Pakistan has justified the retaliatory military action as justified under Article 51 of the United Nations Charter, which allows self-defence in response to armed attack.
Amid the tit-for-tat strikes, both Indian and Pakistani strikes allegedly hit hydropower assets. Unconfirmed reports by Pakistani media have accused India of targeting the Noseri Dam near the Neelum-Jhelum Hydropower Project. Two shells also landed on hydroelectric corporation offices in Indian-administered Kashmir, according to an Indian official.
India’s home ministry ordered mock drills to test preparation for an attack across the country to take place on 7 May, including air raid warning system tests. This constitutes the largest civil defence drill in India since 1971. India’s Air Force is expected to hold drills on the night of 7 May in the west of the country, and Delhi and Bengaluru airports are set to hold disaster management exercises; these are reportedly unlikely to impact passenger operations.
Beijing has declared that it is closely following the situation and has advised its citizens to avoid conflict areas. China’s foreign ministry has urged both India and Pakistan to exercise restraint and refrain from taking escalatory actions.
INTELLIGENCE ANALYSIS
Limited Military Escalation Likely Following India’s Airstrikes on Pakistan Territory
The airstrikes come amid escalatory tit-for-tat actions between India and Pakistan following the Pahalgam attack, which resulted in at least 26 civilian deaths. The attack was allegedly orchestrated by the Resistance Front, a reported offshoot of the Pakistan-linked terror group Lashkar-e-Taiba.
The high civilian toll, almost all of whom were Hindu Indian nationals, has escalated tensions between India and Pakistan, prompting mass deportations and the imposition of airspace restrictions in the days leading up to the 7 May strikes.
There is precedent for India retaliating with airstrikes after perceived Pakistan-backed militant attacks on its territory. In 2016 India launched “surgical strikes” against Pakistan after four militants killed 19 Indian soldiers in Uri, Jammu and Kashmir; in 2019, further strikes were launched in Balakot after 40 Indian paramilitary personnel were killed in a bombing in Pulwama.
Indian strikes on Pakistan have generally been subthreshold, designed to target militant camps to carry out retaliatory measures while not forcing Islamabad into entering into a direct conflict.
While Pakistan has responded with limited artillery shelling along the Line of Control in Jammu and Kashmir, it is likely Pakistan will be forced to respond with airstrikes under mounting public pressure. Pakistani retaliatory strikes are highly likely to be carefully calibrated to remain below the escalation threshold and to avoid triggering a major conflict with a rival nuclear power.
During previous hostilities in 2019, Pakistan refrained from directly targeting Indian military sites, instead striking open areas to demonstrate its capability while limiting civilian casualties. To avoid a major escalation or miscalculation, Pakistan will likely limit its strikes to Indian-administered territory in Jammu and Kashmir.
The targeting of dams, particularly in Indian-administered Kashmir, is highly likely due to India’s perceived weaponisation of water flows after unilaterally pulling out of the Indus Water Treaty. This has significantly escalated tensions between the two sides since it threatens Pakistan’s water supply and agricultural sector, with Pakistan having warned that any attempt from India to disrupt the flow of water from its rivers would be considered an act of war.
Over the past week, India has taken steps to enhance the storage capacity at two hydroelectric facilities in Jammu and Kashmir’s Himalayan region, constituting the first concrete action outside the framework of the Indus Water Treaty. In a highly likely perceived threat to Pakistan’s water supply, India began flushing silt at the Baglihar and Salal dams in the Kashmir valley on 3 May. This would ordinarily only be allowed during the monsoon season, as it involves nearly emptying the reservoirs of silt before closing the dams and slowly refilling them, choking water flow downstream.
Pakistan recorded a significant decrease in the waters of the Chenab River, and since 4 May, almost 90 per cent of the usual volume has been prevented from flowing into the Chenab River.
A full-scale conflict between the two nations remains unlikely despite the airstrikes. For India, a war would highly likely drag the country into a prolonged conflict that would significantly affect its economy. This would almost certainly stretch India’s armed forces, which have been underfunded in recent years, allowing Pakistan to catch up militarily.
Although the US has developed closer ties with India, especially during the Trump administration, a conflict between India and Pakistan would likely impact the global economy, giving the US a strong interest in promoting de-escalation.
Pakistan almost certainly cannot afford to enter a war. Pakistan Armed Forces are currently engaged in a multi-front internal conflict against militant groups, primarily in Balochistan and Khyber Pakhtunkhwa. While its military is more battle-tested than India’s, a war would almost certainly overstretch its armed forces, would risk destabilising the military-dominated government and would provide opportunities for militants to exploit.
Furthermore, a conflict would hinder the country’s progress in stabilising its economy. Pakistan was removed from the Financial Action Task Force (FATF) grey list in 2023 after legislative and institutional reforms to address perceived anti-money laundering and counter-terrorist financing deficiencies. India has indicated plans to advocate for Pakistan’s re-entry in the aftermath of the militant attack, and a war would significantly increase the likelihood of this happening.
Furthermore, a conflict would hinder the country’s progress in stabilising its economy. Pakistan was removed from the Financial Action Task Force (FATF) grey list in 2023 after legislative and institutional reforms to address perceived anti-money laundering and counter-terrorist financing deficiencies. India has indicated plans to advocate for Pakistan’s re-entry in the aftermath of the militant attack, and a war would significantly increase the likelihood of this happening.
If re-added, Pakistan would almost certainly face reduced investment and foreign aid, as well as risk being blacklisted, which would significantly affect is ability to finance its debt repayments.
Given that both nations are nuclear-armed, a full-scale conflict would risk rapid escalation and nuclear war. This acts as a deterrence from escalation for both sides, who will likely favour diplomatic options and limited skirmishes despite the ongoing brinkmanship. Diplomatic pressure will almost certainly be applied by regional powers including China.
Amid heightened sectarian tensions, there will highly likely be increased attacks between Hindus and Muslims in India and Pakistan, with probable clashes during protests. There is a realistic possibility of sectarian tensions also manifesting within diaspora communities, such as within the UK, US, and Canada. Disinformation campaigns framing the attack as a symptom of an inter-religious conflict are likely and will almost certainly exacerbate tensions.
This is especially since the tensions come shortly after Modi passed the Waqf Amendment Act, which changes the way Muslim waqf properties are governed, triggering violent protests by conservative Muslim communities, particularly in West Bengal.
There is a realistic possibility of lone-actor attacks, further inflaming sectarian tensions. Security forces of both countries will almost certainly be at a heightened state of alert during the current tensions, which likely reduces the threshold at which they will respond forcefully to perceived unrest, making clashes between protesters and security forces likely.
Travel Risk Advice: Safety Guidelines for India and Pakistan
- Closely monitor local news reports and government alerts.
- Avoid all non-essential travel to Jammu and Kashmir, as well as Indian-Pakistani border regions.
- Avoid all military installations, government buildings, and key infrastructure.
- Civil unrest and demonstrations are highly likely throughout both India and Pakistan. Travellers are advised to avoid all areas of unrest. Protests are likely to occur near government buildings, foreign embassies, and religious sites.
- Adhere to all instructions issued by authorities.
- Ensure that you contact and register with your local embassy or consulate if stranded in India or Pakistan.
- The security situation in Jammu and Kashmir is likely to remain highly unstable in the coming weeks with an increased potential for further cross-border strikes, terror attacks, and civil unrest.
- Evacuations and internal displacement will almost certainly lead to widespread travel disruption and congestion on major roads. Ensure vehicles are fuelled, consider alternative routes, and ensure that vehicles are loaded with additional fuel, water, food and other critical supplies.
- Confirm booked flights are running before checking out of hotels or travelling to the airport.
- Have emergency contact numbers saved on your phone. These should include the local authorities, medical facilities, and any consular support. Ensure that mobile phones are charged in case of any losses in electricity.
- Monitor the Solace Secure platform and trusted local media for updates relevant to the conflict.
Subscribe to free weekly intelligence

Geopolitical, Global Security & Environmental Events
Key Events This Week
America
Cartel Violence in Mexico
A surge in violence in a Mexican tourist location is highly likely linked to the fragmentation of the Sinaloa Cartel and may serve as a vignette as to how cartels will shift operations as narcotics smuggling is threatened.
Europe, Middle East and Africa
Western Europe Power Grid Incident
The cause of a power outage across Western Europe will likely take weeks to identify, however, the incident almost certainly highlighted major vulnerabilities in the energy network that could be exploited in the future.
Anti-Tourism Protests Set to Rise
Anti-tourism protests are almost certain to increase in frequency in May and peak during the summer, with South European states, like Spain, Portugal, France, and Italy, being particularly affected.
AfD Extremist Label May Backfire
There is a realistic possibility that Germany’s designation of the AfD as an extremist group will result in increased levels of right-wing extremism, resulting from the party’s isolation on the political stage.
Kremlin Likely to Exploit Ceasefire Deal
It is highly likely that the Kremlin will use an announced three-day ceasefire to accuse Ukraine of violations to gain concessions, with the minerals deal likely increasing US interest in supporting Ukraine.
Romania Elections May Spark Protests
The 4 May presidential elections in Romania are highly likely to coincide with demonstrations by the supporters of banned candidate Călin Georgescu.
Burkina Faso Risks Investment Fallout
Burkina Faso’s move to increase state ownership of foreign-operated industrial mines is likely to lead to coercive measures, discourage foreign investment, and cause long-term instability.
Northeast Nigeria Violence Escalates Again
A surge in violence in northeast Nigeria is likely the result of overstretched government forces, an increase in extremist use of technology, and may be indicative of a temporary truce between rival groups.
Asia Pacific
India-Pakistan Tensions Remain Localised
While all-out conflict is unlikely between India and Pakistan, limited airstrikes, protests, and an escalation of sectarian violence in the two countries are highly likely.
North, Central and South America
Mexico: Wave of violence targets popular tourist resort
The US Embassy in Mexico has issued a security alert for the popular tourist areas of Los Cabos (Cabo San Lucas and San José del Cabo) and La Paz in Baja California Sur, following a wave of violence in an area normally shielded from significant levels of cartel violence.
On 22 April, three high-ranking law enforcement officials were killed in the area in two separate attacks. On 24 April, at least three passenger buses were set on fire in Los Cabos and La Paz while passengers were still onboard. On 25 April, a shootout occurred in Cabo San Lucas during a security operation aimed at apprehending those responsible for the arson attacks on the buses.
In addition, cartels operating in the area have displayed “narcomantas” (banners) with threats against officials in public areas, including near the Los Cabos International Airport. The violence has resulted in an increase in security operations in the area and a wave of arrests. In one operation, Marcos Iván “N” (“Marquitos”), a senior figure in the La Mayiza (or Los Mayos) faction of the Sinaloa Cartel, was apprehended.
Solace Global Assessment:
It is highly likely that the increase in violence in Baja California Sur is associated with the fragmentation of the Sinaloa Cartel following the detention of its senior leadership in July 2024. The arrest of Joaquín Guzmán López and Ismael “El Mayo” Zambada resulted in infighting between the two primary factions within the Sinaloa Cartel, the Los Chapitos and the La Mayiza factions.
This has resulted in a steep rise in violence within Sinaloa, which has now likely migrated to Baja California Sur, where both factions are vying for territorial control of key smuggling routes on the Baja California Peninsula and lucrative elements of the tourist industry. The recent arrest of “Marquitos”, of the La Mayiza faction, likely triggered retaliatory actions by elements of Los Chapitos who are likely seeking to exploit the power vacuum and exert control over illicit revenue sources.
Initial reports now indicate that Rene Bastidas Mercado, or “El 00”, of the Los Chapitos faction is now in control of Baja California Sur. However, reports suggest that Abraham Cervantes Escareaga, known as “El Babay” of the La Mayiza faction, is attempting to reassert control over Baja California Sur.
Cartels often refrain from conducting violence in tourist areas for several reasons. Cartels often benefit directly and indirectly from the tourism industry, with profits generated from the direct ownership of tourism-related businesses, local drug sales to visitors, extortion of hospitality venues, and money laundering through cash-rich front companies.
Moreover, violence in tourist areas invariably invites a major increase in security operations and international scrutiny, particularly from the United States, whose travel advisories can significantly affect the local tourism industry. However, this tacit non-aggression pact has almost certainly been suspended as a result of the Sinaloa Cartel’s fragmentation, with rival factions calculating that a transient increase in violence and intimidation will be strategically beneficial in the long term once control is consolidated.
There is also a realistic possibility that the Mexican government’s increased force posture in northern Mexico and increased security on the US-Mexico border have led to a loss of revenue for the Sinaloa Cartel. Recent reporting indicates that the cartel has been forced to suspend or relocate operations due to increased arrests, seizures and raids, largely associated with increased pressure from the US, which has threatened tariffs and even direct action against the cartels if Mexico fails to curtail narcotics smuggling into the US.
This sustained pressure has reportedly impacted both narcotics and human smuggling revenues, two of the Sinaloa Cartel’s primary income streams. In response, it is highly likely that the cartel, especially its more fragmented factions, will attempt to compensate for these financial losses by expanding into alternative illicit revenue sources. One major avenue is extortion, which has long been used by the cartels to extract funds from local businesses.
This may account for the recent attacks on buses, with transport operators frequently for extortion and the attacks potentially retaliation for failing to pay protection fees or for paying the rival faction. If this assessment is accurate, the situation in Baja California Sur may serve as a vignette for how cartel operations are likely to adjust in the near future, with cartels shifting towards more localised and coercive tactics to generate revenue methods such as extortion, as transnational trafficking becomes riskier and less profitable.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Canada’s Liberal Party wins federal elections
The Liberals, led by Prime Minister Mark Carney, have managed to win enough seats to form a minority government, following a last-minute surge in popular support that erased months of Conservative Party dominance in the polls. Carney, who replaced Justin Trudeau after the latter announced he would step down in January 2025, has campaigned on promises to reverse some of Trudeau’s most controversial policies and to respond to US economic coercion.
No party wins a majority in Cayman Islands general election
No party won a majority in the 30 April 2025 General Election. The People’s Progressive Movement won seven seats, but did not meet the ten required to form a majority. Two newly formed parties, the Cayman Islands National Party and the Caymanian Community Party each won four seats. A non-binding referendum on three issues was also held regarding whether the Cayman Islands should develop cruise berthing infrastructure, introduce a national lottery, and legalise marijuana. As with the 2021 election, parties will now engage in coalition talks to attempt to form a government.
Clashes in Dominican Republic over anti-migrant protests
Protests occurred in Santo Domingo on 27 April, coinciding with the 60th anniversary of the start of the Dominican Civil War. Demonstrations during the day were also organised by the Old Dominican Order, a nationalist group, which opposes the alleged “Haitianisation” of the country and has called for mass deportations of Haitian nationals.
While the protests began peacefully, there were reported clashes between protesters and the police, who deployed tear gas. While the current government of President Luis Abinader has adopted a tough stance on migration, the ongoing humanitarian crisis in Haiti has almost certainly driven a rise in support for more radical nationalist and identitarian groups.
Opposition party wins snap election in Trinidad and Tobago
On 29 April, the Union National Congress (UNC), led by former prime minister Kamla Persad-Bissessar, declared victory in a snap election. The election was called by the newly appointed Prime Minister Stuart Young, after Keith Rowley stepped down amid rising cost of living and soaring crime rates.
The election follows a 105-day state of emergency imposed after a surge in homicides, with 623 recorded in 2024 out of a population of approximately 1.5 million. The rise in murders is linked to criminal gangs, including the Venezuelan Tren de Aragua, and has placed the country among the most violent countries in the Americas, with a homicide rate of 37 per 100,000 people.
The Bissessar has promised numerous measures to combat the crime wave, including the establishment of new ministries of defence and justice. She has also promised to raise wages for public sector workers amid economic stagnation triggered by declining natural gas production, which comprises approximately 80 per cent of the country’s economy. Bissessar previously declared a state of emergency to combat crime during her first tenure as prime minister; there is a realistic possibility that she will use similar measures during her new tenure.
Violent protests erupt in Guyana after the death of an 11-year-old girl
Guyana has imposed a curfew effective from 29 April following violent protests caused by the death of an 11-year-old girl. The girl was found dead at a coastal resort in Tuschen, leading to accusations that she was sacrificed as part of a religious ritual.
The alleged murder and resulting police investigations led to protests in Tuschen, in the capital Georgetown and other parts of the country, with reports of looting, property damage and clashes with the police. The police resorted to using tear gas and firing ammunition after blockades were erected in the capital and clashes erupted outside of Georgetown Public Hospital. There is a realistic possibility of renewed unrest following the release of autopsy results, which are currently being finalised.
Security, Armed Conflict and Terror
Trump administration to designate Haitian gangs as FTOs
On 29 April, the Trump administration informed the US Congress of its intent to designate the Haitian gangs, Viv Ansanm and Gran Grif, as foreign terrorist organisations (FTOs). The move will follow the designation of several Latin American cartels as FTOs.
The designation could enable the US to freeze any financial assets held within US jurisdiction linked to the groups and could penalise anyone providing material support to the gangs. The move could also enable the Trump administration to deport anyone connected to the gangs from the US back to Haiti. In a far less likely development, the designation could also help provide legal justification for US counterterrorism or intelligence collection in Haiti.
Environment, Health and Miscellaneous
Red alert issued for Costa Rican volcano
On 24 April, a red alert was issued due to an increasing and significant series of eruptions taking place at the Poas Volcano, situated approximately 30km north of the capital, San José. The authorities have closed the Poas National Park as a result of the volcanic activity and have warned against approaching nearby riverbeds due to the presence of volcanic material. Should the volcano continue to release ash, there is a realistic possibility of disruption to air traffic at Juan Santamaría International Airport.
Powerful earthquake strikes off the coast of Esmeraldas, Ecuador
The earthquake, which struck around midday on 25 April, was magnitude 6.3 with a depth of 35 kilometres. Moderate shaking was felt in Esmeraldas, which led to multiple buildings being significantly damaged, with shaking being reportedly felt as far as Guayaquil. Although the earthquake happened at sea, it resulted in no tsunami threat.
Across Ecuador, at least 179 residences were damaged, with 22 people injured and 716 people being “affected”, the majority in Esmeraldas and Muisne. There were no disruptions recorded at Quito Airport.
Due to Ecuador’s proximity to the Pacific Ring of Fire and multiple fault lines, the country is highly seismically active. Previous powerful earthquakes, such as the 2016 7.8 magnitude quake near Muisne which killed at least 676 people, have caused a significant impact.
Europe, Middle East & Africa
Spain, Portugal and France: Major disruption after power outages
On 28 April 2025, a significant power outage affected mainland Spain, Portugal, Andorra, and parts of southwestern France, disrupting daily life for an estimated 55-60 million people. The blackout commenced at 12:33 CEST and persisted for up to ten hours in various regions. The cause of the blackout remains unknown, with investigations underway. Initial reports indicate a sudden and substantial drop in energy demand, which resulted in the destabilisation of the grid.
In Spain, the blackout halted all train and metro services, stranding an estimated 35,000 passengers, and disrupted operations at Madrid’s Barajas Airport. Internet and telecoms dropped to less than 20 per cent of normal capacity, while nuclear plants shut down automatically and relied on generators for cooling. Madrid enforced its emergency plan, closing shops and deploying police for traffic control. Economic losses were estimated at EUR 1.6 billion, and at least seven deaths were reported, with some linked to generator misuse.
In Portugal, essential services and payment systems failed, hospitals relied on generators, and public transport, including metro and rail, was suspended. Lisbon Airport was temporarily closed, while Porto and Faro airports operated on backup power. In France, the effects were limited to brief outages in parts of the southwest.
Solace Global Assessment:
Investigations as to why the power outages occurred are ongoing and will likely take weeks to establish a widely accepted explanation. Several explanations have been advanced, although several experts are indicating that it may have been a convergence of factors and not a single cause.
As investigations progress, there is a huge risk of disinformation being proliferated, with largely discounted explanations, such as a state-sponsored cyber-attack, gaining a lot of traction in the information space. One popular theory alleges that Spain’s rapid integration of renewable energy is at fault. The theory is likely to fuel further controversy over net-zero energy policies and will almost certainly be leveraged by right-leaning groups to exert pressure on the current Sanchez administration in Spain.
Regardless of what caused the blackout, the incident highlighted multiple vulnerabilities. One of the primary vulnerabilities is Portugal’s overreliance on Spain for electricity imports, which left the country exposed to grid failures.
The disruption demonstrated how energy interdependence, which is typically beneficial under normal conditions, can rapidly become a liability when a neighbouring system experiences instability. The blackout clearly highlighted the fragility of digital and communications infrastructure across the affected areas. Both telecommunication and internet services fell to a fraction of their normal capacity, severely disrupting business and daily life.
The blackout also demonstrated major shortcomings in public sector preparedness, with inconsistent or poor contingency planning evident at multiple hospitals, airports and across the wider transport network.
While a deliberate cyberattack or act of sabotage has so far largely been dismissed as the cause, the scale and speed of the disruption underscore the systemic vulnerabilities within Europe’s interconnected energy networks. In the future, these weaknesses could be deliberately exploited by malicious state or non-state actors seeking to cause widespread disruption and economic loss if the underlying structural causes of the outage are not identified and addressed.
Southern Europe: Anti-tourist groups pledge summer of direct action
On 27 April, a group of anti-tourism protesters surrounded a tourist bus in the centre of Barcelona and sprayed its occupants with water guns. The symbolic event, which mirrors similar protests in 2023 and 2024, was carried out to launch the new manifesto of an international protest group, the Southern European Network Against Touristisation (SET).
Initially launched in 2018 in Spain, SET has gained significant traction since 2021 and has expanded to Italy, Spain, and Portugal, with local chapters in 17 cities. SET has pledged to continue to carry out direct action in the summer and has called for a general demonstration on 15 June.
Solace Global Assessment:
While anti-tourist groups have existed in Europe since the early 2000s, often operating alongside or as part of smaller far-left and anarchist movements, a pan-European anti-tourism movement has considerably grown since the COVID-19 Pandemic. SET is only one of many similar groups, which include regional movements like Less Tourism, More Life (in the Balearic Islands), Banc the Temps (Mallorca), Arran (Catalonia), No Grandi Navi (Venice), Nice a Nous (Nice). However, the manifesto published following the Barcelona protest likely indicates an effort to coordinate direct action as part of an international movement.
Protests by SET and other anti-tourism groups are almost certain to occur in high-visibility areas, usually next to well-known tourist sites. A notable number of protests are likely to include direct action protest tactics. While most protests are likely to be peaceful, there remains a realistic possibility of isolated cases of harassment and vandalism targeting tourists or tourist facilities.
A smaller number of protests, likely including SET’s 15 June demonstration, will entail larger gatherings, meant to disrupt tourism-related activities in city centres. An example of this is the May 2024 march through the centre of Palma de Mallorca, which was attended by around 10,000 people.
In terms of dates, it is highly likely that protests will begin to intensify in frequency in the first weeks of May and will peak in late June and July, coinciding with the end of the academic year in most European countries.
Some elements within the broader movement have reportedly refused to rule out targeting airports and other transportation hubs, a move that could result in major transport disruptions if done at scale. These actions could consist of blockades of roads leading to and from transport hubs, or, particularly in the case of airports, attempts to enter the perimeter, thus forcing a shutdown of airport operations.
Germany: Domestic intelligence agency designates AfD as an extremist group
On 2 May, Germany’s domestic intelligence agency, the Federal Office for the Protection of the Constitution (BfV), officially classified the country’s far-right party, the Alternative for Germany (AfD), as a “proven right-wing extremist organisation.” The move marks the most serious action to date designed to contain Germany’s growing far-right movement and was justified on the grounds that the BfV has definitive evidence that the AfD actively works against Germany’s democratic system.
Solace Global Assessment:
The designation marks the first time in modern German history whereby a party with nationwide representation in parliament has been officially labelled as extremist, although some state-level branches of the AfD, such as those in the eastern states of Saxony and Thuringia, have already received the designation. It is highly unlikely that the designation will result in the banning of the AfD. However, it will serve as a precursor for increased state surveillance of the AfD and will almost certainly isolate the party on the national stage, with other parties now far less likely to cooperate with the AfD within the Bundestag.
For AfD supporters, who secured almost 21 per cent of the vote in the 2025 federal election, the move will almost certainly be perceived as politically motivated and an attempt to suppress dissenting voices. The immediate effect of the designation is likely to be the galvanising of AfD’s base. This could result in the organising of protests across Germany, particularly in the east, which may lead to violent clashes between AfD supporters with both the police and counter-protestors.
In the long term, the designation is likely to lead to deeper divisions and could ultimately drive right-wing extremism underground if supporters feel it is no longer possible to achieve their objectives through established democratic structures. This trend is likely to translate into an increase in right-wing politically motivated violence, with right-wing extremist crimes totalling over 30,000 in 2024, according to the Federal Criminal Police Office (BKA). Moreover, the reallocation of intelligence and counter-terrorism resources to monitor elements of the AfD could result in an overstretching of these resources, ultimately leading to reduced oversight of other forms of extremism within Germany.
Ukraine: Putin announces three-day Victory Day ceasefire and minerals deal signed
After a 26 April meeting between US President Donald Trump and Ukrainian President Volodymyr Zelensky in the Vatican, Trump wrote on social media that Russian President Vladimir Putin may be ‘just tapping me along’ and threatened Russia with ‘Banking or Secondary Sanctions’. This was followed by a Kremlin announcement on 28 April of a unilateral three-day ceasefire between 8 and 10 May during WWII Victory Day commemorations.
Furthermore, Russian Foreign Minister Sergey Lavrov stated on 29 April that the Victory Day ceasefire proposal ‘is the start of direct negotiations, without preconditions. Kyiv has responded by again calling for Washington’s previous proposal for a full, permanent ceasefire, or at least a 30-day ceasefire, as a prelude to comprehensive negotiations for a peace agreement.
Additional statements from the past week, however, from Lavrov, former President Dmitry Medvedev, and senior Kremlin officials, have all variably reiterated maximalist war goals as a condition for peace, which included the ‘destruction’ of the current Ukrainian government and the full annexation of desired oblasts, including currently unoccupied areas.
On 30 April, Ukraine and the US signed what has been termed the ‘minerals deal’, with the agreement having been delayed with talks needing to restart after the fractious February encounter between Zelensky, Trump, and Vice President JD Vance, in the White House.
The newly negotiated agreement is watered down in Ukraine’s favour compared to the previously proposed draft text, with the establishment of a joint fund with the US and Ukraine each contributing 50 per cent of financing and revenues split 50/50.
Following the minerals deal, the US State Department certified a proposed license to export USD 50 million worth of military aid to Ukraine, the first such permission since Trump paused Ukrainian military aid after taking office.
Solace Global Assessment:
The minerals deal is the result of a concerted effort by Kyiv to find ways to incentivise the Trump administration to maintain US support for Ukraine, having been held off during the Joe Biden administration in anticipation of Trump’s second presidency.
The increasing frustration of Trump and US officials over the intransigence of Moscow during talks has led to the development of two highly distinct possible scenarios: a) Washington changes its approach to be more coercive against Russia, with the use of more stringent sanctions (as threatened by Trump), or possibly even the ramping of military support to Kyiv; or b) The Trump administration “washes its hands” of Ukraine, accusing both Moscow and Kyiv as being uncooperative and leaving the support of Ukraine to European allies.
The minerals deal has likely considerably reduced the likelihood of the second scenario in the short to medium term, although the final terms of the deal omit previously demanded stipulations on paying back the US for aid given thus far.
It is highly likely that the Kremlin will use the three-day ceasefire to accuse Kyiv of violations, as it did during the energy infrastructure moratorium. The Easter truce, whilst leading to a pause in long-range strikes against Ukrainian urban centres, was marred by extensive accusations of violations.
However, Moscow is highly likely motivated to keep Washington engaged in talks insofar as the Kremlin can leverage them for concessions to further its objectives, and likely fears forcing Trump into taking a more hardline approach. Although denied by the General Staff of the Ukrainian Armed Forces, Putin’s claims on 26 April that Russian forces have retaken all of Kursk, if true, will likely result in a reorientation of Russian forces concentrated in the area to conduct new operations – including the developing northeastern Ukraine spring offensive towards Sumy.
It is likely that Moscow will continue to offer “olive branches” such as the Easter truce or the possibility of direct talks to set conditions for Washington to make concessions and apply pressure to Kyiv, whilst continuing to pursue results on the battlefield to achieve maximum leverage over Ukraine.
Romania: Unrest likely to occur during and after Romanian elections
Romanians will vote to elect their next president on 4 May, with a second round on 18 May if no candidate receives an absolute majority. The elections are the second to happen in less than a year, as the previous vote in November 2024 was annulled by the Constitutional Court over alleged Russian interference, and the winning candidate, Călin Georgescu, was barred from running. Currently, the polls indicate that George Simion, leader of the populist Alliance for the Union of Romanians (AUR), is the leading candidate. AUR has backed Georgescu’s unsuccessful challenge of the court ruling, and has pledged to give him a government role following a possible victory.
Solace Global Assessment:
Georgescu’s supporters will likely stage demonstrations against the vote in the last days of the campaign, and on 4 May itself. These demonstrations are likely to be concentrated in Bucharest and are unlikely to result in large-scale traffic disruptions. Nevertheless, a realistic possibility remains of clashes between protesters and police.
In the short term, the elections are likely to be a source of political instability in Romania. With Georgescu’s ban, the vote will highly likely function as a “referendum” on the judiciary and on other Romanian state institutions.
Finally, there is a remote possibility of political violence. Following the annulment of the November 2024 vote, several extremist groups and activists have called for a “revolution” against the Romanian state and have encouraged supporters to attack state officials. If political violence were to occur, the most likely targets would be security personnel, state officials, or electoral stations and staff on or near 4 May. While unlikely to be directly targeted, travellers would be at risk of being collaterally impacted.
Burkina Faso: Junta to nationalise more foreign-owned mines
On 28 April, Burkina Faso Prime Minister Jean Emmanuel Ouédraogo announced on a nationwide broadcast that the junta government is planning on increasing state ownership of foreign-operated industrial mines as part of efforts to retain a greater share of mining revenues. The initiative will be led by the recently formed state-owned company, Société de Participation Minière du Burkina (SOPAMIB).
SOPAMIB has already been used to achieve control of two industrial gold mines, which were previously owned by the London-listed firm, Endeavour Mining. The move also follows the revision of Burkina Faso’s mining code, which will prioritise national ownership, local suppliers, labour and expertise, but has generated fears of weakened investor protections, concerns of arbitrary state intervention due to a lack of legal clarity, the potential for retroactive contract changes, and pressure tactics.
Solace Global Assessment:
Burkina Faso’s recent changes towards the mining sector are similar to those observed in Mali and Niger, two other resource-rich but highly unstable and fragile states suffering from endemic poverty, political instability and extremist violence. The junta is likely trying to capitalise on current gold prices, which have increased substantially since the imposition of US tariffs and the associated economic uncertainty.
While this may increase government revenue in the short term, there is a high likelihood that this shift will result in decreased foreign investment, greater economic instability, further isolation and overreliance on extractive industries. In the long term, it is likely that these trends will undermine attempts to stabilise the country, deter investment and reduce job creation, trends that will ultimately be to the advantage of extremists like the al-Qaeda-aligned Jama’at Nasr al-Islam wal-Muslimin (JNIM) and other violent extremist organisations (VEOs), which collectively are assessed to already control approximately 50 per cent of the country.
Burkina Faso’s efforts to consolidate control over the mining industry will likely involve coercive measures similar to those reported in Mali and Niger. This has involved the detention of foreign nationals working for foreign mining companies that have failed to adhere to the imposition of retroactive taxes or changes in mining codes.
In Mali, personnel belonging to Barrick Gold were detained in order to extract leverage from the company after the company allegedly failed to meet its tax obligations, with the junta also threatening to place the mine under provisional administration unless tax payments were made. There have also been reports of gold stocks being seized, mining permits being suspended, and the seizing of mines, all tactics that the Burkina Faso junta is likely to employ as it asserts control over the mining industry.
Nigeria: Potential jihadist resurgence in northeast
A spate of attacks in northeastern Nigeria has resulted in warnings of a jihadist revival in the area. On 24 April, at least 14 farmers were killed in Borno State’s Gwoza district near the border with Cameroon, an attack that has been linked to Boko Haram.
On 26 April, Boko Haram ambushed and killed 10 members of the Civilian Joint Task Force in Adamawa State. Suspected twin Boko Haram attacks on 27 April in Adamawa and Borno resulted in 22 deaths, including hunters and Civilian Joint Task Force members.
On 28 April, Boko Haram attacked a Christian community in Borno, killing seven people and burning homes and churches. Then on 29 April, a roadside improvised explosive device (IED) was detonated on a bridge between Rann and Gamboru Ngala in Borno State, killing 26 civilians. The attack has been claimed by the Islamic State West Africa Province (ISWAP).
The surge in violence since January has already led to a warning from the Borno State Governor, Babagana Zulum, who claimed that insurgents were making gains with minimal resistance from the Nigerian military. On 29 April, the Nigerian government appointed Major General Abdulsalam Abubakar as the new commander of counterinsurgency operations in the northeast but refused to officially link the appointment to the surge in violence.
Solace Global Assessment:
In recent years, the Nigerian military has successfully managed to contain and even push back Boko Haram, with internal fights with ISWAP leading to a further weakening of the broader jihadist movement. However, both internal and external developments have likely shaped the conditions for a jihadist revival in the region.
The wider destabilisation and increase in extremism in the Sahel have severely impacted Nigeria. Groups like Boko Haram have been able to exploit the porous border with Niger to establish safe havens in the ungoverned spaces of the Sahelian state. However, more recently, there has been an emergence of new jihadist threats in the northwest of Nigeria linked to Niger, a development that when combined with a host of other internal threats such as banditry and successionist movements, has likely resulted in the overstretching of Nigeria’s military.
This development has been greatly compounded by the increased use of IEDs and uncrewed aerial vehicles by both groups, particularly ISWAP. This could indicate a shift towards more asymmetric tactics, employing high-impact attacks that are difficult to anticipate while conserving manpower by avoiding direct confrontation with security forces.
UAVs are also being increasingly used in an intelligence, reconnaissance, and surveillance (ISR) capacity by both groups, a trend that will enable the VEOs to better plan, coordinate and execute attacks against government forces, which are often poorly trained and ill-equipped. ISWAP’s increased use of technology may reflect developing links between it and the broader Islamic State (IS) network. IS has facilitated the transfer of funds, technical expertise and training across its affiliates, resulting in a significant enhancement of their capabilities.
If harnessed effectively by ISWAP and emulated by Boko Haram, it is highly likely that the increased use of these technologies will lead to a migration of violence from rural areas to urban areas, resulting in higher rates of civilian casualties.
Following an ideological split in 2016, Boko Haram’s and ISWAP’s relationship has been characterised by internecine fighting and attempts to expand into each other’s areas of influence. However, there have been previous attempts to establish a truce, likely driven by mutual concerns over external pressure.
The recent surge in violence, which has seen coordinated attacks across their typical area of operations, could be anecdotal evidence of a fragile truce in play. If this is the case, then the temporary cooperation and even coordination between Boko Haram and ISWAP could significantly increase the threat to security forces and civilians and could even lead to a transfer of expertise from IS-affiliate to Boko Haram, potentially resulting in more sophisticated tactics and attacks.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Anti-migrant protests and counterprotests on Easter Rising Day in Ireland
At least three people were arrested during protests on 27 April in Dublin. The protests were attended by around 5,000 people and were led by anti-migrant campaigners and activists. The relatively large attendance was highly likely driven by the high social media virality attained by the campaign due to the support of several online influencers and celebrities. Local civil society groups, as well as party members, staged counterprotests. Despite some hostile interactions between the two sides, no clashes were recorded.
Germany’s new cabinet announced
Chancellor Friedrich Merz’s government will reflect the changed power dynamics between the Christian Democratic Union parties (CDU/CSU), and the Social Democrats (SPD), with the former getting ten ministries and the latter seven. The Christian Democratic appointees are in line with Merz’s campaign pledges to increase state security and growth, and to crack down on immigration. The SPD’s main victory is its retention of the Defence Ministry, which will likely allow it to dictate a continuation of Berlin’s support for Kyiv, and a greater say on the direction of Germany’s rearmament plans. The new government is, nevertheless, still likely to face considerable domestic pressure.
Conclave to begin in the Vatican City on 7 May
The voting process to elect the new pope will likely coincide with large influxes of pilgrims and tourists to Rome and other Italian cities. There is a risk of terrorism due to the high visibility of the event and its importance for Catholics. Likewise, civil unrest remains possible, particularly smaller, symbolic actions, as groups capitalise on the visibility of the conclave to mainstream their position. Travellers to Rome are likely to encounter traffic and service disruptions. While a conclave can last indefinitely, the process is likely to take less than a week. Nevertheless, disruptions are likely to continue in the short term following the papal election.
Hungarian opposition lawmakers temporarily barred from parliament
On 28 April, Hungary’s parliament voted to temporarily banish and cut the salaries of six opposition Momentum MPs after they lit flares and played the Soviet national anthem in protest of the 18 March ban on LGBTQ+ Pride marches. The House Speaker Laszlo Kover has also filed a criminal complaint against three of the MPs over the use of flares.
This constitutes the first instance of members of parliament being banned from the chamber since Hungary became a democracy in 1990. Ruling party Fidesz’s decision to ban Pride marches is highly controversial, and the EU is currently investigating whether the party’s plan to deploy facial recognition technology is illegal. Numerous protests have occurred in the wake of the government’s decision to ban Pride events, and more are likely following the news regarding the banning of MPs.
Mali’s junta plans to dissolve all political parties
The national dialogue committees promoted by the junta after taking power in 2021 have issued “recommendations” for junta leader Assimi Goita to become the country’s president and begin a five-year term, and for dissolving all existing parties. The proposals were justified by their proponents as meant to align Mali to the political structure of the other members of the Alliance of Sahel States (AES).
The move, which is likely to be mostly or fully adopted by the junta, will almost certainly further centralise power in the junta’s hands and disenfranchise civil society organisations. The ban on parties and the de facto prohibition of the creation of new ones is likely to be weaponised by the government to target domestic political dissent.
Opposition leader appears in court, and more opposition officials arrested in Tanzania
On 28 April, Tanzanian opposition leader Tundu Lissu appeared in court to face sedition charges following his recent arrest. Armed police barred access to the courthouse to journalists and members of the Chadema Party, resulting in accusations of an attack on press freedom and a violation of constitutional rights. Police also conducted illegal raids in the homes of Lissu and Deputy Chairperson John Heche, and other key officials from Chadema were arrested in separate incidents. These incidents have drawn international condemnation and fears that Tanzania is drifting towards more authoritarianism under President Samia Suluhu Hassan ahead of the November general election.
Security, Armed Conflict and Terror
Lone wolf “Incel” attacker injures two in Leeds, UK
On 26 April, a man reportedly injured two women using a crossbow in Headingley, Leeds. The attacker, who was found to also be in possession of a firearm, was arrested by responding police.
Online posts reportedly originating from the perpetrator’s Facebook profile indicate that he espoused a violent ideology marked by extreme hatred of women, linked to “incel” (“involuntary celibate”) online subcultures. This link with incel ideology is likely further underscored by the attacker’s choice of target. The Headingley area is especially frequented by students of nearby Leeds University, and, by selecting it, the attacker likely sought to harm students.
Past incel lone wolves, like the 2014 Isla Vista attacker, the 2015 Umpqua Community College shooter, the 2017 Aztec, New Mexico and 2018 Parkland, Florida school shooters, all deliberately targeted students.
Online calls for violence targeting UK Hindu and Muslim communities
The rise in tensions between India and Pakistan following the recent terror attack in Jammu and Kashmir has almost certainly driven a sharp increase in the spread of misinformation and hateful content targeting Hindus and Muslims, particularly those from diaspora communities, in the UK.
Notably, a considerable amount of the content espouses far-right and identitarian ideologies, in addition to religious extremism. The development almost certainly showcases the growing threat of sectarian violence within diaspora communities. There is a realistic possibility of political violence, including mob violence, occurring in large UK cities following further increases in India-Pakistan tensions.
Islamophobic stabbing attack kills one in France
On 25 April, a man carried out a stabbing attack at a mosque in Ales, France, killing one worshipper. The alleged perpetrator, who was detained by Italian police after trying to flee the country, is a French-Bosnian citizen who reportedly shouted anti-Islamic slogans and filmed himself during the attack, subsequently sharing the video online.
Civil society organisations have staged rallies in solidarity with the victims and the French Muslim communities and have called for a national day of direct action on 11 May. The attack in Ales shares multiple details with similar lone wolf attacks, including the use of bladed weapons, the selection of a high-visibility target, and the recording and sharing of the attack on social media.
Three people gunned down in Uppsala, Sweden
On 29 April, three people under the age of 20 were shot dead at a hair salon in the Swedish city of Uppsala, approximately 40km north of Stockholm. The police responded by establishing a large cordon of the area, suspending all rail traffic in the immediate area and conducting a manhunt, which ultimately led to the arrest of a 16-year-old suspect.
The motive for the shooting remains unconfirmed; however, authorities believe it is connected to the ongoing gang-related violence that has affected Sweden in recent years, violence that, according to some assessments, has made the country the worst in the EU for gun crime. The incident also highlights the trend of increasing youth involvement in violent crimes.
Israel conducts airstrikes near Syrian presidential palace following sectarian clashes against Druze
On the morning of 2 May, Israel conducted airstrikes within 500 metres of Syria’s presidential palace in Damascus. Syrian sources indicate that the interim-President Ahmad al-Sharaa and top officials had left the palace just an hour prior. The strikes follow sectarian violence in Jaramana and other predominantly Druze areas of southern Syria between 28-30 April, after the circulation online of an audio clip alleged to be a Druze leader insulting the Islamic Prophet Muhammad, which has been denied by the accused Druze sheikh.
Sunni gunmen entered Druze towns and clashed with Druze militias, with the General Security Forces attempting to curb the violence. At least 102 people have reportedly been killed thus far in the clashes. The Israeli Prime Minister Benjamin Netanyahu has stated that the Israeli strikes are intended to be a warning to Damascus, to deter the deployment of Syrian forces south of Damascus or threats against the Druze community.
It is almost certain that the Sharaa government does not exercise control over the fighters who are attacking the Druze. In comparison to the March massacres of Alawites, government-aligned security forces have highly likely been far more effective in attempts to prevent sectarian clashes against the Druze, successfully cordoning off Druze settlements despite suffering casualties. The Israeli strikes, however, will likely further inflame hostilities emanating from Sunni militants against the Druze, and there is a realistic possibility that these hostilities will be increasingly directed against the Sharaa government if it is perceived as being weak against Israel.
Iraqi security arrests one ISIS suspect in connection with New Orleans truck attack
A spokesperson of the Iraqi Supreme Judicial Council said that Iraqi forces had arrested the individual responsible for “inspiring” the New Year’s Eve attack that killed 14 people. This represents an important development for analysing the attack. While it immediately became evident that the perpetrator had pledged allegiance to the Islamic State (IS), the new arrest likely demonstrates a greater level of vertical direction and a sustained commitment from the VEO to conduct external attacks outside of the Levant.
US strikes hit migrant centre in Yemen, as UK joins the new aerial campaign against Houthis
The US-led aerial campaign against the Houthi movement in Yemen has continued, with the UK having now also participated in aerial strikes. On 28 April, a migrant detention centre was reportedly hit by US strikes, with the Houthi-run health ministry and media claiming 68 fatalities and 47 injuries. Whilst Houthi-provided statistics are unreliable, footage from the bombing’s aftermath has been geolocated and verified.
On 29 April, the UK’s Royal Air Force (RAF) conducted strikes using precision-guided bombs against a cluster of buildings identified as being used to manufacture drones, 24km south of Sanaa. The migrant trail from East Africa to Saudi Arabia results in considerable numbers of Ethiopians, Sudanese, Somalis crossing the Bab al-Mandeb Strait to Yemen, and available information indicates that a majority of the casualties from the 28 April attack were Ethiopian.
During US President Donald Trump’s first presidency, the Pentagon relaxed the rules of engagement for airstrikes in 2017, which almost certainly contributed towards a 330 per cent increase in civilian casualties from US airstrikes in 2019 compared to 2016. It is highly likely that Trump has similarly relaxed rules of engagement during his second presidency.
The UK’s participation in the new anti-Houthi aerial campaign is likely partly conditioned by an attempt to appease the Trump administration, with senior advisors and the Vice President having expressed frustration at the lack of European action against the Houthis. With reports indicating that a potential US-UK trade deal is being given ‘second-order priority’, Westminster is likely further incentivised to appease Washington’s desires for increased military involvement against the Houthis.
Islamic State Sahel Province (ISSP) increases kidnapping operations
On 26 April, ISSP operatives attacked a Nigerien military convoy in the Sakoira area. The ambush resulted in the deaths of 12 Nigerien soldiers, and the kidnapping of five Indian nationals. In 2025 alone, ISSP has kidnapped at least 14 foreign nationals. Of these, only four Moroccan truck drivers who had been kidnapped near the Niger-Burkina Faso border have been released (although some sources dispute this), while a Spanish national kidnapped in southern Algeria was rescued by Azawad forces.
The sharp increase in the number of kidnappings makes them highly likely part of a concerted effort by ISSP’s leadership, marking a shift in the group’s strategy. Moreover, unlike the Islamic State in Iraq and Syria (ISIS), which, during its zenith in 2014-2017, sought to kidnap foreigners as a propaganda tool and later executed them, ISSP has not released media regarding the hostages, possibly indicating that it is seeking to negotiate ransom payments for their release.
Reports indicate JNIM attempting to establish presence in eastern Senegal
A report by the Timbuktu Institute has indicated a significant escalation in jihadist activity by the al-Qaeda-affiliated Jama’at Nusrat al-Islam wal-Muslimin (JNIM) in the tri-border region of Kayes, which includes parts of Mali, Mauritania, and Senegal. The report suggests that attacks between 2021 and 2024 have increased sevenfold in the area and that JNIM are attempting to infiltrate eastern Senegal.
JNIM is likely capitalising on weak state governance and the prioritisation of regime survival in Mali to increase its influence in the area, which it will exploit to increase attacks in Senegal. The strategy likely reflects similar attempts to establish safe havens and buffer zones in other countries that border the Sahelian states, such as Benin and Togo, a move that would allow JNIM to expand its economic activity and recruitment in Senegal to exert greater pressure on the Malian government.
Renewed assaults on El Fasher in Sudan’s Darfur region
On 29 April, at least 41 people were killed in shelling of El Fasher in a renewed Rapid Support Forces (RSF) offensive. El Fasher is the regional capital of North Darfur and constitutes the final town held by the Sudanese Armed Forces (SAF). The SAF reported that they killed 600 militants and 25 military vehicles, a number likely inflated.
The RSF is intensifying the siege of the city after being pushed out of Khartoum by the SAF, and its capture is almost certainly a high priority for the paramilitary. By capturing El Fasher, the RSF will complete a crucial step in consolidating its control of Darfur, where it has recently formed a parallel government.
Humanitarian groups in the region have been forced to halt food distributions in the city, and at least 540 people have been killed in the region in the past three weeks. The renewed offensive will almost certainly impact humanitarian operations in Darfur, since El Fasher constitutes a hub for humanitarian operations in all five Darfur states.
Opposition MP killed in “targeted and premeditated” shooting in Nairobi, Kenya
On 30 April, Charles Ong’ondo Were, a member of parliament representing Kasipul constituency in the west of Kenya for the Orange Democratic Movement, was shot and killed in the capital, Nairobi. Were was shot when his vehicle was stationary at traffic lights by a shooter riding as a pillion passenger on the back of a motorcycle. The police have described the killing as “targeted and premeditated”.
The assassination of politicians is relatively rare in Kenya but Were had previously voiced concerns for his safety. Should the public perceive the incumbent administration as being in any way implicated, there is a realistic possibility of civil unrest in Kenya. Public dissatisfaction with President Ruto is already high, resulting from the 2024 attempt to pass a controversial tax bill and the government’s handling of the subsequent protests, which led to multiple civilian fatalities and mass arrests.
Environment, Health and Miscellaneous
Major explosion at Iranian port leads to mass casualties and significant economic disruption
A large explosion on 26 April at Shahid Rajaei Port in Bandar Abbas, Iran killed at least 70 people and injured over 1,000. The port handles 85 per cent of Iran’s shipping, including a considerable proportion of oil exports. 1,500 hectares of the port are estimated to have been affected, and authorities state that it will take one to two weeks to return to normal operations.
The explosion will highly likely exacerbate Iran’s ongoing economic crisis, with losses of approximately USD 25 million per day since 26 April. The Iranian interior minister, Eskander Momeni, blamed noncompliance with safety precautions and negligence for the blast, with customs authorities claiming the trigger was imported cargo catching fire.
Western media, however, has implicated a sodium perchlorate shipment, which is used to produce solid fuels used in ballistic missiles, which has been denied by Iran’s defence ministry. The port reportedly received hundreds of tons of the chemical precursor in February and March, almost certainly delivered from China. Some experts point towards ammonium nitrate, which is a widely used fertiliser and industrial explosive, as a likely culprit, as it was for the 2020 Beirut port explosion. Detonating ammonium nitrate is difficult, however, without other chemicals catalysing it, such as the fireworks which triggered the detonation in Beirut.
While it would be unusual for the sodium perchlorate to be stored at the port for so long after delivery, an unnamed source linked to the Islamic Revolutionary Guard Corps (IRGC) briefed that the chemical was responsible for the explosion. Whatever the cause, there is a realistic possibility of civil unrest due to the number of fatalities, exacerbation of Iran’s economic woes, and the perceived or actual cover-up being conducted by authorities.
Wildfires in Israel threaten Jerusalem
As of 2 May, wildfires that threatened Jerusalem have been largely contained. The Israeli government declared a national emergency after Israel’s largest ever wildfires broke out on 1 May along the Jerusalem-Tel Aviv highway. High winds have exacerbated the fire, spreading it to burn at least 5,000 acres.
Approximately 163 ground crews and 12 aircraft are attempting to contain the fires, with military planes dropping retardant to stop them from spreading. On 2 May, authorities declared the re-opening of the Jerusalem-Tel Aviv highway.
The fires are suspected to have been deliberately started, and conflicting reports have emerged regarding the number of arson suspects detained; Prime Minister Netanyahu mentioned 18 arrests, while police have confirmed only three. Due to the effectiveness of the fires and the associated disruption, there is a realistic possibility that this tactic will be emulated in the future.
Asia–Pacific
India and Pakistan: Tensions escalate following the Pahalgam attack
Following the 22 April militant attack that killed 26 civilians in Pahalgam, Jammu and Kashmir, tensions have escalated between India and Pakistan. On 30 April, India responded in kind to Pakistan’s airspace closure to Indian airlines, closing its airspace for all Pakistani aircraft until 23 May.
On the same day, Modi held a meeting with senior state and defence officials, declaring that the Indian armed forces have the freedom to decide the ‘timing, targets, and mode’ of their response to the militant attack. Pakistan’s information minister has warned of ‘credible intelligence’ that there may be an imminent attack from India and has warned that it will respond appropriately.
Troops have exchanged small-arms fire across the border, but no casualties have been reported. The US and UN have called for de-escalation, with Secretary of State Marco Rubio urging Islamabad to condemn the terror attack and cooperate in its investigation.
Solace Global Assessment:
A full-scale conflict between the two nations remains unlikely despite the escalating tensions and aggressive rhetoric. For India, a war would highly likely drag the country into a prolonged conflict that would significantly affect its economy.
Furthermore, there is a realistic possibility that China would join the conflict as a Pakistani ally, and New Delhi would almost certainly like to avoid a multi-front war, which would stretch its armed forces, which have been underfunded in recent years, allowing Pakistan to catch up militarily.
Although the United States has developed closer ties with India, especially during the Trump administration, a conflict between India and Pakistan would likely impact the global economy, giving the US a strong interest in promoting de-escalation.
Pakistan almost certainly cannot afford to enter a war. Pakistan Armed Forces are currently engaged in a multi-front internal conflict against militant groups, primarily in Balochistan and Khyber Pakhtunkhwa. While its military is more battle-tested than India’s, a war would almost certainly overstretch its armed forces, would risk destabilising the military-dominated government and would provide opportunities for militants to exploit.
Furthermore, Pakistan was removed from the Financial Action Task Force (FATF) grey list in 2023 after legislative and institutional reforms to address perceived anti-money laundering and counter-terrorist financing deficiencies. India has indicated plans to advocate for Pakistan’s re-entry in the aftermath of the militant attack, and a war would significantly increase the likelihood of this happening. If re-added, Pakistan would almost certainly face reduced investment and foreign aid, as well as risk being blacklisted.
Limited airstrikes and limited border clashes are likely amid significant public pressure for visible action. In the aftermath of the 2019 suicide bombing in Pulwama, Jammu and Kashmir by a Pakistan-based militant group Jaish-e-Mohammed (JeM), India launched airstrikes across the line of control in Balakot targeting an alleged JeM training camp. Similar actions are highly likely in the coming days and will likely target militant camps away from populated areas to avoid a miscalculation or significant escalation.
Pakistan will likely respond with limited and sub-threshold military action designed not to provoke an escalation. Cyberattacks targeting critical infrastructure are also likely, due to the minimal threat of loss of life.
Amid heightened sectarian tensions, there will highly likely be increased attacks between Hindus and Muslims in India and Pakistan, with probable clashes during protests. There is a realistic possibility of sectarian tensions also manifesting within diaspora communities, such as within the UK, US and Canada.
Disinformation campaigns framing the attack as a symptom of an inter-religious conflict are likely and will almost certainly exacerbate tensions. There is a realistic possibility of lone-actor attacks, further inflaming sectarian tensions.
Security forces of both countries will almost certainly be at a heightened state of alert during the current tensions, which likely reduces the threshold at which they will respond forcefully to perceived unrest, making clashes between protesters and security forces likely.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Bangladesh seizes Hasina family assets
This follows a ruling by the Anti-Corruption Commission, which targets multiple real estate assets, land, and more than 120 bank accounts. The interim government has capitalised on its efforts to dismantle the remnants of the government led by Sheikh Hasina and her Awami League (AL) party, following their removal from power in August 2024, to increase its support and maintain its unstable hold on power.
The volume and value of the assets that have been targeted almost certainly showcase the extent and penetration of the system of clientelism promoted by AL and Hasina as part of their efforts to maintain political supremacy. While authorities have highlighted the importance of due process, assets linked with AL members have been repeatedly targeted in acts of mob vandalism. There is a high likelihood of this trend continuing, despite government efforts to curtail it.
Security, Armed Conflict and Terror
Pakistani security forces kill 54 militants at Afghan border
Security forces reportedly engaged dozens of militants as they were trying to cross the border on the night of 26-27 April in the North Waziristan area. The Pakistani military called the militants “Khwarij”, a term that usually refers to the Pakistani Taliban (TTP) and is an iteration of “Kharijites”, a name derived from early Islamic history often used as a derogatory term to describe violent, extremist and revolutionary Islamist groups.
The incident’s casualty count is unusually high and likely highlights ongoing TTP efforts to reinforce their position on the Pakistani side of the Durand Line. TTP, moreover, may be seeking to capitalise on Pakistan’s ongoing instability and its tensions with India, which have a realistic possibility of overstretching or unbalancing Islamabad’s security forces. De facto, Pakistani officials have hinted at this logic: following the attack, Pakistan’s Interior Minister Mohsin Naqvi stated that the TTP were prompted to carry out their incursion by “foreign masters” (obviously referring to Kabul) who “[asked] them to enter Pakistan as soon as possible”.
Car-ramming attack at Chinese elementary school
A man reportedly drove a vehicle into a crowd of students and parents outside an elementary school in Jinhua, Zhejiang province. Due to limited information being released about the incident by Chinese media, the exact number of injuries is unclear, although videos taken by bystanders seem to show at least five injuries.
There is a realistic possibility that this attack falls within the “revenge against society” attacks (sometimes referred to with terms like “Zhang Xianzhong” or “Xianzhongxue” on Chinese social media, after the leader of a 17th-century peasant rebellion). These attacks have attracted significant media attention since at least 2021, and around 20 alleged cases occurred in 2024 alone. They are characterised by the lack of a clear ideological motive, the targeting of low-visibility and high-density locations (often schools), and the use of improvised weapons, like vehicles or knives. Moreover, unlike lone wolf attackers in Western countries, perpetrators are not preoccupied with sharing their actions on social media.
Twin attacks in Thailand’s Yala province
Two coordinated insurgent attacks in Thailand’s Yala province between 28–29 April killed three security personnel and injured another, highlighting the persistent threat posed by Muslim separatist groups in the Deep South, despite ongoing peace talks and increased security measures following a spate of attacks in recent months.
If attacks continue at this rate, there is a realistic possibility that the government rejects peace talks and pursues more aggressive military tactics. This would constitute a similar approach seen under former Prime Minister Thaksin Shinawatra, which involved the imposition of curfews, arbitrary arrests, an increase in raids and the use of military tribunals for suspected militants.
Environment, Health and Miscellaneous
Wildfires in South Korea cause significant disruptions in Daegu
Wildfires that began on 28 April in Daegu led to the evacuation of over 5,000 residents and the issuance of a Level 3 wildfire response, the highest tier, from the Korea Forest Service. Several disruptions resulted from the fires, including the closure of local schools and key infrastructure such as Gyeongbu expressway. By the evening of 28 April, the fire was reportedly 50 per cent contained and by the afternoon of 29 April, the fire was reportedly fully extinguished. On 30 April, however, the fire rekindled, prompting further evacuation advisories for nearby residents, particularly around the Guam neighbourhood.
In addition to the considerable impact in neighbourhoods close to the fires, the wildfires caused a deterioration in air quality across Daegu. The Daegu wildfires follow the March wildfires that originated in Ulseong, which were the worst in South Korean history and killed at least 28 people. According to a report published by an independent body of scientists and researchers, the Ulseong fires were highly unusual in terms of scale and speed, with climate change being a significant factor. Climate change is expected to increase both the frequency and severity of wildfires globally.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Delays and Closures Expected Following Major Outages in Spain and Portugal
Intelligence cut off: 14:00 BST 28 April 2025
At approximately 12:30 local time (10:30 UTC) on 28 April, Spain, Portugal, Andorra, and parts of France and Belgium experienced power outages. The outage was most widespread in Spain and Portugal, hitting several Spanish regions in the north and south. In Portugal, the blackouts affected most of the country.
In Spain, train services have been significantly affected, with trains ceasing to operate at all stations in Spain according to the national operator, Renfe, and passengers were evacuated from metro systems and trains. Airports across the country, including Madrid’s Barajas Airport, have activated contingency generators, but considerable delays are ongoing. The disruptions have also affected hospitals, ATMs, shops, restaurants, traffic lights, and mobile networks across the region. In Portugal, the metro in Lisbon and Porto have been affected and Lisbon’s Humberto Delgado airport has been disrupted. Portuguese airline TAP Air has informed passengers to avoid heading to airports.
The Spanish operator Red Electrica has declared that it is beginning to restore power in northern and southern regions, indicating that it will ‘gradually’ return. The full restoration is expected to take six to ten hours. While parts of France temporarily lost power, electricity has since been restored.
INTELLIGENCE ANALYSIS
Increased Crime and Emergency Response Delays Likely During Power Outage
While the cause has not yet been fully established, a fire in southwest France reportedly damaged a power line between Perpignan and eastern Narbonne, potentially triggering the blackouts. Portugal’s government announced that the incident appeared to stem from outside the country, and a cabinet minister suggested it may be a problem with the distribution network in Spain. Domestic media have pointed to issues with the European electric grid, which may have impacted Spain and Portugal’s national grids. Spain’s cybersecurity institute is investigating the possibility that it was caused by a cyberattack.
During the power outages, it is highly likely that there will be a temporary increase in opportunistic crime and petty theft. This is likely exacerbated by the fact that citizens have been asked not to call the emergency number, 112, unless in an emergency, to avoid overloading the phone lines.
Significant traffic disruptions are almost certain, particularly in Spain and Portugal. Traffic light outages will highly likely trigger increased congestion, which will likely be exacerbated by rail network disruptions, forcing more people to drive. There will likely also be higher rates of road traffic accidents. Portuguese police have deployed extra officers to assist with traffic circulation. There will highly likely be a knock-on effect to travel over at least the next 24 hours, even after power is restored.
Travel Risk Advice: Safety Guidelines for Spain, Portugal, Andorra, France and Belgium
- Allocate more time for travel and reassess the necessity of travel. Avoid using all public transport. Avoid all nighttime travel during power outages. Taxis should be booked well in advance due to increased demand caused by disruptions to public transport.
- Due to the highly likely increased traffic congestion and likely increased rates of road traffic accidents in areas impacted by traffic-light failures, it is advised to avoid any non-essential driving.
- If scheduled to fly, confirm flight status with the carrier prior to travelling to the airport.
- Note that power grid disruptions are likely to have short-term impacts even after power is restored. Likewise, assume that further power outages remain possible in the immediate term.
- Note that power outages can coincide with an increased risk of crime. Take heightened crime-mitigation measures.
- Avoid all solo travel and nighttime movement if the disruptions persist. Ensure that residential or office premises are secured.
- Ensure that you always carry personal identification documents or copies.
- Turn off appliances to prevent damage from electricity surges when power is restored.
- If available, use emergency light sources, like a battery-powered or wind-up torch. If using candles, be wary of fire hazards. Only run generators outside, in a clear area away from any building openings.
- Prioritise sending SMS messages over making phone calls as networks are likely to be overloaded.
- Monitor the Solace Secure platform and trusted local media. Disinformation is widely propagated during crises.
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
Gangs are almost certainly continuing their efforts to surround the capital of Haiti by intensifying operations to its north and south. Kenyan and Haitian forces will highly likely fail to contain the spread of violence.
Europe, Middle East & Africa (EMEA)
Russian hybrid attacks in Europe will likely intensify as a result of US disengagement, resulting in increased acts of sabotage and cyberattacks against companies and infrastructure supporting Ukraine.
The largest attack on Kyiv, Ukraine, in 2025 is almost certainly reflective of the Kremlin’s continued priority of using military force to fulfil its objectives, and reflects the particular threat posed by ballistic missiles.
Burkina Faso’s junta’s claim of a foiled coup attempt likely reflects the continuously deteriorating security environment outside the capital and likely increases the threat of arbitrary detention to foreign nationals.
JNIM attacks in northern Benin are almost certainly indicative of the extremist group’s intent to expand outside of the Sahel and establish safe havens in neighbouring countries.
There is a realistic possibility that the growing political crisis in Zimbabwe will trigger widespread civil unrest or a coup attempt.
Asia-Pacific (APAC)
A terrorist attack in Jammu and Kashmir is unlikely to trigger war between India and Pakistan despite a major diplomatic fallout, but is likely to lead to sustained border skirmishes, protests and sectarian violence.
North, Central and South America
Haiti: Mirebalais hospital closes, US declares gang a terrorist group
On 23 April, the University Hospital of Mirebalais declared that it would cease operations following weeks of gang attacks in the area. Hospital administrators and doctors have stated they will seek to move the patients to other regional facilities at a lower risk of gang attacks. Two days prior, on 21 April, Washington announced that it would designate Viv Ansanm, the largest Haitian gang coalition which now occupies large portions of both Mirebalais and the capital, Port-au-Prince, as a foreign terrorist organisation (FTO). During the last reporting period, particularly heavy clashes were recorded in the Kenscoff area in the outskirts of Port-au-Prince, where at least three Haitian soldiers were killed in an ambush by gangs on 20 April.
Solace Global Assessment:
On 21 April, Maria Isabel Salvador, the UN’s special representative to Haiti, stated that, without further support, the UN’s presence in the country may become “unsustainable”. As demonstrated by the gangs’ growing advances on the outskirts of Port-au-Prince, the Kenya-led police contingent continues to struggle to provide a sufficient security response to the crisis. Also on 21 April, the Kenyan ambassador to the UN stated that approximately 260 police officers who are scheduled to be deployed to Haiti remain “on standby” due to the lack of equipment and logistical support. The gangs’ operations in Mirebalais likely continue to demonstrate their commitment to a strategy aimed at destroying all civil institutions to force the civilian population to be dependent on them. In addition to shutting down the local hospital and setting fire to the (now empty) police station, gangs have reportedly also targeted independent radio stations.
The gangs’ offensive on Kenscoff is likely dictated by a similar logic to the previous attack on Mirebalais. Kenscoff is located on the Kenscoff-Marigot road, which, although in a state of disrepair, offers an alternative route south of Port-au-Prince, avoiding the gang-controlled National Route 2. Moreover, Kenscoff overlooks the commune of Pétion-Ville, where numerous government offices, banks, and embassies are located. The fall of Kenscoff would therefore likely cut off humanitarian aid routes connecting Port-au-Prince to southern Haiti, further destabilising the government’s position.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
“National Day of Action” planned for 1 May in US
A collective of US-based civil society groups has called for non-violent protests to occur on 1 May, in opposition to the current administration. Protests are scheduled to occur in all 50 states, with some related events also occurring in Canada. Due to the high visibility of the events and likely high volume of attendees, there is a realistic possibility of violence breaking out during the protests. There is a remote chance of clashes involving counterprotesters. Finally, there is a realistic possibility of the protests driving localised acts of vandalism against assets owned by or associated with private companies perceived to be supportive of the Trump administration.
The US Education Department to begin collection on defaulted student loans
Approximately 5.3 million borrowers are currently assessed to be in default on their federal student loans. The announcement marks the end of a period of leniency supported by the previous administration. On 5 May, the department is expected to begin involuntary collection via the offset program of the Treasury Department, allowing it to withhold tax refunds, federal salaries, or other government payments, and to garnish wages from borrowers. The measure will likely contribute to driving civil unrest, including both large-scale protests and small-scale direct action.
Guatemalan indigenous leader arrested
On 23 April, Guatemalan authorities arrested Luis Pacheco on charges of terrorism and illicit association. Pacheco is one of the country’s most politically important indigenous leaders. In 2023, he led a network of 48 indigenous communities in staging nationwide blockades of the country’s highway network, in opposition to the then-administration’s questioning of the 2023 electoral results. President Bernardo Arevalo, who appointed Pacheco to a post at the sustainable development ministry upon taking power, has opposed the arrest. It is highly likely that the arrest will drive limited civil unrest in Guatemala, possibly impacting road traffic in the country.
Mass evictions in Santa Cruz, Bolivia, resulted in clashes
More than 500 police officers reportedly participated in operations to evict residents of the Santa Lucia area of the department on 21 April. The operation was reportedly aimed at removing makeshift residential buildings in the area, which were allegedly built illegally on privately owned land. Residents protested the decision, claiming that the decision had not been adequately communicated or debated by the authorities. The protests resulted in limited clashes with police forces, who deployed tear gas and carried out multiple arrests.
Security, Armed Conflict and Terror
Mexican cartels stage multi-state road blockades
Starting on 23 April, road blockades were recorded on multiple highways in the Mexican states of Jalisco, Michoacán, and Guanajuato, with dozens of vehicles set on fire to block the roadways. The blockades started the day following clashes between security forces and alleged narcotraffickers in the Apatzingán mountains, in Michoacán. These, in turn, were likely provoked by the arrest of a local drug trafficking leader. The road blockades have highly likely been organised by the Jalisco New Generation Cartel (CJNG), which is the main criminal group in the area, and are likely meant as a show of force. During the Easter celebrations, CJNG members reportedly staged multiple “narco-parades” through town centres in Michoacán, likely a show of force to the local and national governments at a time when both the US and Mexican governments are exerting pressure on the cartels.
Guerilla attack forces shut down of Colombian oil pipeline
On 17 April, the Bicentenario crude oil pipeline in Colombia was forced to shut down following an explosion that the state oil company, Ecopetrol, attributed to a guerrilla attack. Initial reports have indicated that the attack was conducted by the National Liberation Army (ELN), which is currently fighting government forces in multiple parts of Colombia. The pipeline was attacked in the Fortul municipality, in the department of Arauca, a rural area with limited government presence and a known stronghold for the ELN. There is a realistic possibility that the attack may mark a shift in ELN tactics, involving the deliberate targeting of critical national infrastructure (CNI), which the Colombian government heavily relies on, with the ELN having employed this tactic during previous hostilities.
Mapuche leader arrested in Chile
On 24 April, the Chilean Investigative Police (PDI) arrested Federico Astete Catrileo, identified as the leader of the radical Mapuche organisation, Resistencia Mapuche Lafkenche (RML), in the town of Pocuno, Arauco Province. The RML are a militant group made of the indigenous Mapuche that primarily operates in the Araucania and Bio Bio regions of Chile. The group has been implicated in numerous attacks against industries perceived to be exploiting Mapuche lands. Attacks have included acts of arson and sabotage against critical infrastructure and the key industries such as forestry and mining, as well as the deliberate starting of wildfires. The RML has also been involved in armed confrontations with law enforcement, ultimately leading to their designation as a terrorist organisation by the Chilean Congress. Given the RML’s history of retaliatory violence following arrests of its members, there is a realistic possibility that the arrest of their leader will result in reprisal attacks in Chile, most likely targeting the aforementioned industries.
Environment, Health and Miscellaneous
Colombia, facing rising yellow fever cases, declares a national emergency
Authorities announced the measure during the last reporting period. The nationwide emergency follows a reported 74 cases with at least 34 deaths since the start of the outbreak last year. Authorities have stated that the most affected area is Tolima, located in west-central Colombia, which accounts for approximately a quarter of the cases. Yellow fever, which is highly preventable through vaccination, has estimated death rates of between 40 and 50 per cent. While the Colombian government has pledged approximately USD 140 million to respond to the emergency, rural areas are highly likely to remain at a particularly high risk of the disease.
Europe, Middle East & Africa
Europe: Dutch intelligence warns of increased Russian hybrid attacks
On 22 April, the Dutch Military Intelligence and Security Service (MIVD) warned that Russia is increasing its hybrid attacks against the Netherlands and its European allies, including cyberattacks and acts of sabotage.
In its annual report for 2024, the MIVD disclosed that a Russian cyberattack had targeted a Dutch public service, an attempted act of cyber sabotage aimed at gaining control of a system. Although the attack was ultimately thwarted, it marked the first such attack on a public body in the country.
The agency also reported that Russia has attempted to probe critical infrastructure, assessing that this was likely preparation for further sabotage. Broader concerns were raised about Russia’s mapping of infrastructure in the North Sea, potentially to target internet cables, water supplies and energy infrastructure, including oil and gas pipelines as well as offshore wind farms.
Solace Global Assessment:
Throughout the war in Ukraine, Russia has conducted a campaign of hybrid warfare across Europe that has included cyber-attacks, acts of sabotage and even threats of assassination against individuals supporting Ukraine. With the US potentially disengaging from Ukraine entirely and suspending the delivery of further lethal aid, Russia will likely expand its hybrid campaign across Europe as European nations attempt to compensate for the resulting gap in capability and support.
Reports indicate that Russia has effectively established a “gig economy” as part of its hybrid warfare campaign in Europe. This involves the provision of financial incentives through secure online payments or the use of cryptocurrency to disaffected individuals and marginalised groups that are willing to conduct acts of sabotage or cyber-attacks in support of Russia’s efforts to destabilise and deter the West.
This has primarily involved acts of arson, physical tampering and cyberattacks against industries in support of Ukraine, such as defence companies and components of Ukraine’s wider logistics network, including attacks on transport infrastructure. This shift in strategy has enabled Russia to quickly identify, recruit and control agents from within Russia while still maintaining a high level of plausible deniability.
Western intelligence and law enforcement are likely unable to monitor or police the scale of this activity. As the war continues and divisions in Europe increase, Russia will likely continue to increase recruitment and escalate its hybrid attacks to exploit these growing vulnerabilities and to deter further European support for Ukraine and increase division within Europe.
Targets of Russia’s expanded hybrid attacks will likely include European defence companies, suppliers of non-lethal aid to Ukraine, warehouses storing military equipment or other forms of aid, and key transport infrastructure such as railway infrastructure and even air travel, all of which have been previously targeted in attacks attributed to the Kremlin.
Ukraine: Largest attack on Kyiv in 2025 as US talks continue
Overnight on 23-24 April, the deadliest long-range strikes against Kyiv since 8 July 2024 occurred, killing at least 12 and wounding 80. According to the Ukrainian air force, the attack involved 11 ballistic missiles, 55 cruise missiles, four glide bombs and 145 uncrewed aerial vehicles (UAVs).
The Ukrainian air force claims that both F-16 and Mirage multirole fighter aircraft were used in the air defence effort. The Svyatoshynskyi District in the west of Kyiv was the worst hit, with a ballistic missile identified by Ukrainian forces as a North Korean-made KN-23 directly striking a residential building. Fires were reported in multiple other districts of Kyiv, including Holosiivskyi, Solomyanskyi, and the central Shevchenkivskyi district, with most of these almost certainly resulting from debris from successful interception.
Ukraine’s President Volodymyr Zelensky curtailed a visit to South Africa as a result of the attack, and the US President Donald Trump stated that he was ‘not happy’ and that Russian President Vladimir Putin should ‘STOP!’. The Trump administration has threatened to pull out of the bilateral negotiations if progress is not soon made.
In the first indication of potential concessions to the Kremlin’s previously stated maximalist war goals, sources briefed the Financial Times that Putin is willing to settle on the current frontlines of the conflict.
Zelensky stated that Ukraine will not legally recognise the occupation of Crimea, leading to staunch criticism from Trump, and the Mayor of Kyiv, Vitali Klitschko, suggested that Ukraine may have to give up territory for peace.
Solace Global Assessment:
The major attack on Kyiv is almost certainly reflective of the continued priority of the Kremlin to use military force to gain leverage to achieve its objectives. With the vaguely defined and enforced moratorium on long-range strikes against energy infrastructure having expired on either 16 or 23 April, there have so far been no indications of an extension.
It is highly likely that Moscow is heavily incentivised to deplete Kyiv’s stockpile of Patriot interceptor missiles, with previous shortages due to delays in US Congress approval in late 2023 to early 2024 resulting in a significant increase in the efficacy of Russian long-range strikes. The Patriot air defence system is Ukraine’s most reliable method of intercepting ballistic missiles, which pose the greatest rates of penetration against Ukrainian air defence, with most of the casualties from the 23-24 April Kyiv attack resulting from a ballistic missile.
While Ukraine’s current stockpiles are likely not currently critically low due to the efforts by the previous Biden administration prior to Trump’s inauguration, the Trump administration is far less likely to agree to further replenishment. Ukraine’s European partners, however, are attempting to find methods of indirectly replenishing Ukraine’s stockpiles by purchasing interceptors or even systems from the US.
Whilst the threat of Russian long-range strikes to Kyiv has been lower than in most other major urban centres due to the considerable concentration of air defence assets, renewed interceptor shortages would highly likely significantly increase the risks in Kyiv.
It is highly likely that Moscow has thus far engaged in the US bilateral talks and limited ceasefire proposals primarily to gain concessions to further their continued pursuit of objectives on the battlefield. The briefing of potential acceptance of a deal on current frontlines, as opposed to previously stated demands of full annexation of Crimea, Kherson, Zaporizhia, Donetsk and Luhansk (including all currently unoccupied areas of these administrative divisions), is likely intended to condition the US to apply further pressure on Zelensky to make concessions, which has already materialised to some extent with Trump’s social media posts.
The comments from Klitschko are notable in that they additionally represent an internal division of messaging in Ukraine, which is highly likely also an objective of the Kremlin. As supported by comments from Kremlin Spokesperson Dmitry Peskov on 23 April, even if Russia agrees to a truce on current frontlines without the fulfilment of the objectives to demilitarise Ukraine and replace Kyiv’s government with a puppet government, Russia would restart the war if the ‘legitimacy’ of Zelensky is questioned by the ‘people’.
Kyiv, therefore, is almost certainly highly reluctant to make concessions for a truce if adequate security guarantees against Russian re-invasion are not in place.
Burkina Faso: Junta claims to have foiled ‘major plot’ planned from Ivory Coast
On 21 April, Burkina Faso’s junta government claimed it had foiled a ‘major plot’ emanating from Abidjan. According to the Burkinabe Ministry of Security, communications between a Burkinabe military officer and “terrorist leaders” were intercepted, revealing a plan to “sow total chaos, and place the country under the supervision of an international organisation”. The plan was alleged to ultimately culminate in an assault on the presidency by soldiers on 16 April. Security forces reportedly arrested a dozen military personnel (including two officers) following the plot’s discovery.
Solace Global Assessment:
Since the successful 2022 coup led by Capt. Ibrahim Traoré, the junta has claimed to have thwarted multiple attempts to “destabilise” the government, with the accusations typically involving Abidjan as a source for the plots. The last alleged “destabilisation” plot to be foiled was in November 2024. While the Traoré regime is almost certainly heavily incentivised to generate an atmosphere of paranoia, particularly involving accusations against a foreign power, there have likely been genuine plans of varying degrees of sophistication that have intended to oust Traoré.
Jihadist insurgent groups in Burkina Faso, particularly the al-Qaeda affiliated Jama’at Nasr al-Islam wal-Muslimin (JNIM), are currently estimated to control between 40 to 60 per cent of the country. Widely considered the most fragile of the Sahel junta states, the Ouagadougou-based junta is highly likely to be gradually losing the war against JNIM, despite its claims to the contrary. In 2024, Burkina Faso was ranked by the Global Terrorism Index as the country most affected by terrorism for the second year in a row.
Due to continuously deteriorating security outside of Ouagadougou, where the junta has likely overconcentrated forces due to a prioritisation of regime survival, there is a realistic possibility of multiple currents within the Burkinabe military that wish to depose the junta in another coup d’etat. Despite the extensive operational freedom JNIM exercises across the country, the situation in Ouagadougou remains stable, with no major attacks having been conducted in the city in the last few years.
Should a coup attempt be actioned, however, the security situation could rapidly deteriorate in the city. Additionally, the junta continues to heavily repress civil society. While the crackdown following the latest alleged coup plot has reportedly been limited to a few military personnel, it is likely that the posture of security forces in Ouagadougou is heightened, posing increased threats of arbitrary detention to foreign nationals.
Benin: Al-Qaeda affiliate claims mass casualty attacks on army
On 17 April, the al-Qaeda affiliated transregional violent extremist organisation (VEO), Jama’at Nusrat al-Islam wal-Muslimin (JNIM), conducted twin attacks on army bases in northern Benin in the Kandi province, approximately 500 km (300 miles) from the capital Cotonou. JNIM claims that it killed 70 Beninese soldiers in the attacks, which would mark the most successful attack in Benin since JNIM’s formation in 2017. Official statements from the Benin Armed Forces (BAF) acknowledged the attacks, initially providing a death toll of only eight, however, this was later revised to 54 and marks the highest death toll since JNIM attacks started in the north of the country.
Solace Global Assessment:
The attacks in northern Benin by JNIM likely illustrate the group’s intent to expand its operational footprint into countries bordering the Sahelian states of Niger, Mali and Burkina Faso and into coastal West Africa. The objectives of this broader JNIM strategy are likely manifold.
By increasing instability in the regions that border the Sahel, the group is likely attempting to establish safe havens in these areas and increase recruitment from the local and often disenfranchised Muslim communities. In this context, Benin likely initially published a much lower death toll to limit the effectiveness of JNIM’s propaganda and recruitment messaging.
The establishment of safe havens in the north of Benin and the north of Togo would help shield the group from the junta forces of Burkina Faso and Niger, and also help the group consolidate control of its supply chains.
In the long term, this may also help the group shift operations further towards the coast, placing it in a better position to conduct high-profile mass casualty attacks, such as the 2016 Grand-Bassam beach resort attack in Côte d’Ivoire, which was linked to JNIM.
The destabilisation of areas that border the Sahel also presents JNIM and other violent extremist organisations (VEOs) with the opportunity to limit external intervention in the Sahel. If JNIM can sustain its attacks in Benin, Togo and other neighbouring countries like Côte d’Ivoire, it could force regional nations and groups like the Economic Community of West African States (ECOWAS) to divert resources internally and away from the Sahel, which is JNIM’s primary area of operations.
If attacks continue at such a scale, there is a realistic possibility that Benin will impose a state of emergency in the north in a move that mirrors the strategy already set by Togo.
Zimbabwe: Growing pressure on president amid calls for nationwide shutdown
On 21 April, Blessed Geza, who was recently expelled from the ruling ZANU-PF party, called for an indefinite nationwide shutdown on 22 April to pressure President Emmerson Mnangagwa into resigning. According to Geza’s statement, the shutdown would constitute a final push to end a ‘corrupt’ and ‘incapacitated’ regime.
Geza has also claimed to be working with elements of the security establishment, including the armed forces, in his attempt to remove Mnangagwa from power. This was implicitly denied by the armed forces, who denounced individuals misusing military uniforms.
The calls for a nationwide shutdown largely failed, with most people going about their daily routines. Security forces were on high alert, with increased security presence in urban centres. On 22 April, an apparent cabinet memorandum outlining constitutional amendments which would allow Mnangagwa to remain in office until 2031 was leaked. The document has been dismissed as ‘fabricated’ by Ziyambi Ziyambi, Zimbabwe’s Justice, Legal, and Parliamentary Affairs minister.
Solace Global Assessment:
Zimbabwe is undergoing significant economic problems characterised by volatile inflation, unsustainable debt, energy shortages, a collapsing currency, and unpredictable regulation. These have been exacerbated by governance failures and corruption, with Mnangagwa consolidating political power. The current tensions come amid proposals by ZANU-PF members to delay the 2028 elections to 2031, which would exceed the two five-year term presidential limit.
Following Mnangagwa’s rise to power in a 2017 coup, he reportedly pledged to hand over leadership to Vice President Constantino Chiwenga after completing his term. This agreement now appears at risk if elections are postponed, prompting Geza to urge Mnangagwa to uphold his promise and step down so Chiwenga can take his place. In recent weeks, Mnangagwa has reportedly come under significant pressure from ZANU-PF loyalists to oust Chiwenga, threatening a political crisis.
So far, despite public discontent over the economy and Mnangagwa’s political manoeuvring, demonstrations have failed to gain traction. A previous call by Geza for protests on 31 March was largely ignored by the population. This is highly likely due to fears that the country may descend into civil war, as well as fears of repression by security forces. Before the 31 March demonstrations, Mnangagwa emphasised that security forces would respond with force, and there is a historical precedent of intense repression by ZANU-PF, which killed approximately 20,000 civilians in demonstrations in the 1980s.
While the population remains tentative, there is a realistic possibility that continued economic difficulties combined with perceived authoritarian moves by Mnangagwa, such as the dismissal of Chiwenga, will contribute to a growing public anger and pressure to resign, which could result in large-scale demonstrations across the country. Alternatively, the growing political divisions could result in a coup attempt, with Mnangagwa having recently replaced army chief General Anlem Sanyatwe with loyalist Emmanuel Matatu, triggering anonymous military factions to issue coup threats in February.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
International Workers Day almost certain to coincide with large-scale protests
Civil unrest is likely to occur across all large European urban centres. Violent clashes are likely to occur in cities that have a history of escalating tensions during the day, including Paris and other French cities, Istanbul, Amsterdam, Brussels, and Berlin. There is a high likelihood of traffic disruptions in local city centres during the day. As in 2024, it is highly likely that concurrent pro-Palestine protests will be held on 1 May.
Anti-government, far-right protests planned across Germany on 26 April
The group Together for Germany (GfD) has announced that it will stage demonstrations in 16 federal states on 26 April. The group opposes the current government’s policy of support to Ukraine and particularly the possibility of its supplying of Taurus missiles to Kyiv. Moreover, GfD calls for “comprehensive border controls” and safeguarding freedom of expression.
While the group’s website states that the organisers are “working to exclude extreme movements” from participating in the demonstrations, past GfD demonstrations, including one in late March in Dresden, attracted multiple far-right and identitarian groups. The 26 April protests are likely to be the largest organised by the group so far.
It is almost certain that they will attract counterprotesters and that they will result in significant police deployments at the protest locations. There is a realistic possibility of violence erupting between the protesters and counterprotesters or the police.
Pope Francis dies aged 88
The Pontiff died on 21 April in Rome, just weeks after being hospitalised for double pneumonia. The College of Cardinals is now set to hold a conclave – the papal election – beginning around 5-10 May. The conclave, which happens during the Jubilee – the Catholic holy year that attracts millions of pilgrims to Rome – is likely to impact the risks faced by travellers to Italy and the Vatican.
First, the influx of pilgrims to Rome is almost certain to increase in the short term, possibly resulting in traffic and service disruptions in the Italian capital. Second, the Pope’s death is a high-visibility event and may drive unrest or direct action by groups seeking to mainstream their political or religious positions. Finally, the visibility of the event may result in an increased threat of terrorism, particularly that linked with religious extremism.
Protests continue in Slovakia over controversial NGO law
On 24 April, protests occurred in Bratislava and several other Slovakian cities over the government’s passing of a law which mandates that non-governmental organisations (NGOs) disclose their funding sources. The legislation has been widely criticised as a “Russian law” due to its perceived targeting of NGOs receiving foreign funding, like Russia’s “foreign agents” bill. The law has ignited multiple previous rounds of protests across Slovakia, with critics arguing that it infringes on privacy and freedom of expression and is in violation of EU regulations. President Peter Pellegrini could veto the law before 2 May. However, his decision could be overridden by a majority in parliament. A refusal to veto the legislation or its ultimate passing will likely result in widespread protests across Slovakia.
Moldova to hold elections in September
The country’s parliament voted to hold the contest on 28 September. The elections are highly likely to be extremely competitive and will likely shape the future of Moldova’s relations with the EU. Moldova is currently ruled by the pro-EU Party of Action and Solidarity (PAS), whose leader, Maia Sandu, became the country’s president in 2024 in an election that was perceived as a referendum between Brussels and Moscow. Sandu has sought to combat the pro-Russian regionalist elements in Transnistria, which is a hub for Moscow-backed hybrid warfare, and Gagauzia. The elections are likely to drive civil unrest and possibly political violence. Unrest is particularly likely in the Gagauzia and Transnistria. Moreover, the elections will almost certainly be shaped by the developments in Ukraine.
Bulgarian government survives no-confidence vote
On 17 April, the centre-right Citizens for European Development of Bulgaria (GERB) party survived its second no-confidence motion in two weeks. The motion put forward by the Morality, Unity, Honour (Mech) party and two other nationalist parties, Vazrazhdane and Velichie, was defeated 130-72.
The pro-Western opposition party PP-DB refused to back the motion due to not wanting to destabilise the government before the upcoming European Commission report on Bulgaria’s proposed entry into the Eurozone. The motions were put forward after the opposition accused the government of failing to fight against widespread corruption.
Corruption levels in Bulgaria are high, with accusations of underhanded public procurement procedures, rampant lobbying, and vote buying. Until 2023, when Hungary took first place, Bulgaria consistently ranked as the most corrupt country in the European Union, according to the Corruption Perception Index. Given the failure of the first two motions, another imminent no-confidence motion is unlikely.
Tunisian opposition leaders receive harsh prison sentences
A Tunisian court handed down terms of up to 66 years in prison to a group of 40 figures of the opposition, ending a mass trial that started in March. Among those charged, there are several politicians, journalists, and private sector figures. Around 20 of the defendants have escaped the country since being charged.
The development is almost certainly a further escalation in Tunisian President Kais Saied’s efforts to silence civil society and opposition voices, and to centralise power. Saied, who was elected in 2019, has gradually demolished Tunisia’s opposition, particularly following a “self-coup” in 2021.
Internationally, Saied has pursued close relations with the European Union, and particularly southern states like Italy, which see Tunisia as fundamental to stopping migrant flows in the Mediterranean. In doing so, Saied has likely significantly weakened the EU powers’ appetite to question the country’s authoritarian backsliding.
Jordan outlaws Muslim Brotherhood
Coinciding with the decision, Jordanian police seized the offices and assets used by the Islamist group in the country. The development follows the arrest of 16 Muslim Brotherhood members over alleged participation in a foiled coup plot. The Muslim Brotherhood is Jordan’s main political opposition force and can count on a transnational support network. Consequently, the ban has a realistic possibility of triggering civil unrest and political violence targeting government and police officials.
The government of Jordan has played a balancing act, seeking to retain positive relations with the West and Israel, while simultaneously appeasing a strongly pro-Palestinian civil society. The recent ban is likely to damage this policy, as it is a major shift in the country’s domestic political structure, and could realistically destabilise the Jordanian government.
In particular, if unrest or violence follows the ban, the government is likely to respond by cracking down on dissent. However, such a move could offer an opportunity for anti-government forces and their international supporters, like Iran, to intensify anti-government action, thus driving overall instability.
ECOWAS to withdraw key institutions from Sahelian states
The Economic Community of West African States (ECOWAS) has initiated the process of relocating key institutions out of the breakaway Alliance of Sahel States (AES), which includes Mali, Burkina Faso, and Niger, following their formal withdrawal from the regional bloc earlier in 2025. The move will almost certainly lead to the further isolation of the junta governments and is likely to lead to greater economic instability in the Sahelian states. These developments will likely continue to foster an environment conducive to the proliferation of extremism within the Sahel, which in the long term is likely to increase the risk of violence spreading to neighbouring nations, such as Togo, Benin and other West African states.
Multiple airport workers’ unions in Nigeria begin indefinite nationwide strike
On 23 April, Nigeria Meteorology Agency (NiMet) workers began an indefinite nationwide strike over poor working conditions, low salaries, and inadequate welfare packages compared to other government agencies. The suspension of meteorological services has resulted in other unions suspending operations, including the Union of Air Transport Employees and the Association of Nigerian Aviation Professions, due to the heightened risk associated with operating without meteorological services. The strikes will almost certainly disrupt flights over the coming days, and potentially weeks, unless a settlement is reached.
Ex-DRC President Joseph Kabila’s party suspended
On 19 April, the DRC’s government announced that Joseph Kabila’s People’s Party for Reconstruction and Democracy (PPRD), is suspended and that the other leaders’ assets would be seized in connection with acts constituting high treason, with the government accusing Kabila of supporting AFC/M23 rebels amid their ongoing offensive in the eastern DRC.
While Kabila has not yet responded, Ferdinand Kambere, secretary of Kabila’s party, called the suspension a flagrant violation of the constitution. Kabila’s spokesperson, Barbara Nzimbi, announced that she would address the nation in the coming days or hours.
The decision comes after Kabila announced his return to the country after a self-imposed exile in South Africa following significant unrest that forced him to step down in 2019. While his current whereabouts are unconfirmed, he is rumoured to be in the AFC/M23-controlled Goma. There is a realistic possibility that his return to the country will trigger civil unrest in the capital, Kinshasa.
Ugandan security forces use tear gas and live ammunition against protests at Kyambogo University
On 21 April, students protested against a UGX 50,000 (GBP 10) surcharge for late tuition registration implemented by the university administration, as well as the disallowing of students who have not paid at least 70 per cent of their tuition to sit end-of-semester examinations. Security forces fired tear gas and live ammunition into the air to disperse the protesters (which triggered a stampede), and arrested the guild president, Benjamin Akiso, alongside 10 other students. The university responded by citing existing policies.
Public universities in Uganda have faced underfunding in recent years, relying on non-tax revenue, including tuition, to cover operating costs. Other public universities, including Makerere University in Kampala, have raised tuition fees, raising the possibility of more widespread student protests amid likely frustration, which could result in clashes with security forces.
Security, Armed Conflict and Terror
Attacks on prison apparatus continue in France
Alleged members of the Defence of the Rights of French Prisoners (DDPF) group, which in the last weeks staged attacks across multiple detention facilities, carried out a firebombing at the house of a prison officer in Lyon. Moreover, the group published online “bounties” for information on the residences of prison officers.
The recent attacks are almost certainly meant as a response to the government, which has pledged to crack down on the group. While DDPF’s name is likely meant to give the group’s actions a sense of political legitimacy, the group is likely operating with the backing or direct guidance of organised criminal groups. Further attacks, especially following a government crackdown, remain likely. As French criminal gangs are extremely well-armed, future attacks are likely to pose a significant threat to bystanders.
Turkey detains 525 in biggest-ever anti-drugs bust
The raids targeted Ankara only, following a large-scale Europe-wide operation which was led by Europol and arrested around 230 suspects in the Netherlands, Turkey, Spain, Germany, and Belgium. The operation is notable as it targeted individuals at multiple levels of drug-trafficking organisations, including street sellers. Consequently, it is likely meant to cripple drug revenues and logistics in the short term, and there is a realistic possibility that further arrests will be carried out in the short term.
Turkey has emerged as a key drug trafficking hub since 2022-2023, particularly for cocaine and methamphetamine. This has been driven by multiple factors, including the increase in smuggling routes from Russia following the beginning of the war in Ukraine, and the Dutch authorities’ crackdown on smuggling at the port of Rotterdam.
Salafi extremists capitalise on Syrian regime transition, target pro-Assad elements
Syrian sources reported the increase in extrajudicial killings of individuals perceived as being associated with the ousted Assad regime by a group known as Saraya Ansar al Sunnah. The group appears to share an ideology similar to that of the Islamic State (IS) and has pledged to attack the “apostates” who fought IS. This includes not only elements of the pro-Assad forces, but also religious minority communities like Syrian Druzes and Alawites. Notably, the group rejects the interim government as a “nationalist” entity but has refrained from attacking government forces. Consequently, its targeted efforts are likely meant to stoke tensions between Damascus and the communities newly under its control, possibly driving them to arm themselves and increase the overall insecurity in Syria.
Al-Shabaab fight government forces over strategic base as Turkey enhances force posture in Somalia
Militants from the extremist group, al-Shabaab, are fighting Somali government forces over control of the Wargaadhi base in the Middle Shabelle region. Capturing the base would enable al-Shabaab to sever the main supply route between Mogadishu and the Galmudug State, a key area of influence for the al-Qaeda aligned group, and also place it in an improved position to threaten the capital. Somali forces are reportedly struggling to reinforce the base, with most avenues of approach traversing through al-Shabaab-held territory. On 21 April, Turkey deployed an extra 400 troops to the TURKSOM base in Mogadishu, bringing its total contingent of troops in Somalia to approximately 2,500. The deployment is almost certainly linked to Turkey’s recent securing of oil and gas contracts in Somalia and is likely to be followed by further deployments and military assistance to Somalia in response to al-Shabaab’s offensive.
RSF continue attacks on El Fasher and displacement camps in western Sudan
The Rapid Support Forces have continued to indiscriminately shell El Fasher in North Darfur and neighbouring displacement camps, resulting in dozens of casualties. El Fasher is the last remaining stronghold of the Sudanese Armed Forces (SAF) in the Darfur region and is estimated to house more than one million people. The city is home to tens of thousands of internally displaced persons (IDPs), following attacks on displacement camps and rural areas in the region. Attacks have involved the deliberate shelling of residential areas and open markets, likely in a move to likely in a move to depopulate the city and deny humanitarian access and external oversight of their actions. Sustained attacks are almost certain to continue with the RSF siege aimed at dislocating the city and the SAF from resupply or mutual support.
Kinshasa and AFC/M23 agree to pause fighting in Eastern DRC
On 24 April, the DRC government and Congo River Alliance (AFC), of which M23 is a principal member, announced they would work towards a truce to end the ongoing fighting in Kivu after further Qatar-mediated talks. The statement declared that “both parties reaffirm their commitment to an immediate cessation of hostilities”, seemingly agreeing to a pause in fighting as they work towards a peace deal.
While this marks a significant development in the conflict, at least six ceasefires have been agreed between Kinshasa and M23 since 2021, each one collapsing due to perceived violations. Furthermore, it is not clear whether the agreement constitutes a definitive ceasefire agreement.
Despite the apparent truce agreement, there were reports of clashes between AFC/M23 and the pro-FARDC Wazalendo in a village south of Bukavu on 24 April. Clashes also occurred in Uvira between the FARDC and Wazalendo after the FARDC attempted to dislodge some fighters from strategic positions close to the town.
This reflects both the fragility of ceasefire deals in the DRC as well as the lack of control the FARDC has over the Wazalendo fighters, which could jeopardise agreements made between the government and AFC/M23.
Environment, Health and Miscellaneous
Severe flooding in northern Italy
The northwest region of Piedmont, where Turin is located, had severe flooding following multiple days of heavy rain. According to Italian authorities, the extreme weather event, with 500 mm of rain recorded in 72 hours in some areas near the Alps, is the most severe to strike the region in 30 years. Usually, floods in Piedmont occur during the September-November period, meaning that the recent event is somewhat unusual. Floods in central and northern Italian regions like Tuscany, Emilia-Romagna, and Veneto have, in recent years, become more frequent and destructive. Limited traffic and service disruptions are likely to continue, particularly in rural areas in the region’s north, following the floods.
Earthquake strikes close to Istanbul, Turkey in Sea of Amara
On 23 April, a 6.2 magnitude earthquake occurred in the Sea of Amara, with the epicentre approximately only 40km southwest of Istanbul. The earthquake resulted in damage to almost 400 buildings, and almost 400 people were injured, primarily from people attempting to evacuate. At least 180 aftershocks were recorded, including several over magnitude 4. The earthquake’s epicentre was situated along the North Anatolian Fault, a region of significant seismic activity. Experts have long warned that Istanbul is overdue for a major earthquake, potentially exceeding magnitude 7, and recent estimates have indicated that the city is underprepared for a major earthquake, with over 1.5 million buildings in Istanbul at risk of severe structural damage.
Cholera outbreak in Lakes State, South Sudan
The local ministry of health has stated that three counties in Lake State are currently affected by the outbreak, which has killed at least 27 people. South Sudan recently launched a vaccination campaign, reaching approximately 300,000 people in the state. Nevertheless, multiple factors are likely to contribute to spreading cholera. These include the ongoing internal instability plaguing the country; the remoteness of some local communities, which are difficult to reach due to poor infrastructure, and the beginning of the rainy season, which usually lasts from April to November and facilitates the spread of water-borne diseases.
Asia–Pacific
India: Militant group conduct mass casualty attack in Jammu and Kashmir
On 22 April, militants opened fire on a popular tourist site in Jammu and Kashmir, killing 26 people and injuring 17, with 25 of the fatalities being Indian nationals. The incident took place in Baisaran Valley, a well-known tourist destination in the Himalayan region often referred to as a mini-Switzerland due to its unspoilt natural scenery. The authorities reported that about 1,000 people were in the area at the time, which has an influx of tourists during the spring season.
The attack has been claimed on social media by the militant group Kashmir Resistance or The Resistance Front (TRF), with the group espousing its hostility to “outsiders” in the region, however, some sources have questioned the authenticity of the post. Following the attack, Indian tourists are urgently attempting to leave Kashmir, with airlines arranging additional flights to meet the demand.
According to Indian sources, the TRF is an offshoot of the Pakistan-based Lashkar-e-Taiba (LeT), and India has previously accused Pakistan of supporting militant activity in the disputed region. On 24 April, Indian Defence Minister Rajnath Singh vowed to deliver a “very loud response” to those behind the attack and promised to retaliate against those sitting behind the scenes, without explicitly referring to Islamabad.
Indian Prime Minister Narendra Modi cut short his diplomatic visit to Saudi Arabia to return to India after the attack and also swore to bring justice for those behind the attack. Following the attack, India has closed the border with Pakistan, suspended a water-sharing treaty, downgraded diplomatic ties and has instructed Pakistani nationals in India to leave within 48 hours.
Pakistan has responded by suspending all visas issued to Indian nationals under an exemption scheme, reducing the number of Indian diplomats in Islamabad, asking all Indian military advisers in Pakistan to leave the country, closing its airspace to all Indian airlines and suspending all trade with India. Islamabad also declared that any attempt to stop or divert water will be considered an “act of war”. There have also been reports of skirmishes involving small arms fire along the Line of Control in Jammu and Kashmir.
Solace Global Assessment:
The attack was almost certainly designed to deter further Indian and primarily Hindu tourism from the disputed region. The Modi administration has implemented several initiatives to bolster tourism in Jammu and Kashmir following the controversial removal of the region’s special autonomous status in 2019, resulting in huge increases in tourists.
The revocation of the special autonomous status has also allowed the Indian government to implement new domicile laws, which significantly broaden eligibility for residency and land ownership in Jammu and Kashmir, leading to the settlement of non-local populations, particularly Hindus from other parts of India.
The combined effect of these trends has hugely increased tensions and resulted in growing perceptions among local communities of a deliberate effort to alter the region’s demographic and cultural identity, effectively amounting to a process of ‘Hindufication’ championed by the Modi administration. This has resulted in higher levels of militancy and has been heavily condemned by Pakistan, which continues to claim Jammu and Kashmir as its territory.
India has long accused Pakistan of supporting militancy in Jammu and Kashmir, primarily through established groups like Lashkar-e-Taiba (LeT), Jaish-e-Mohammed (JeM), and Hizbul Mujahideen (HM), which have been associated with numerous attacks on Indian security services, civilians and infrastructure.
The emergence of groups like KRF, which claim to be an entirely local force with no overt ties to Pakistan, could provide Islamabad with greater plausible deniability. This has likely complicated India’s ability to establish direct evidence of Pakistani involvement, although Indian security assessments suggest that the KRF is effectively a rebranded version of LeT and therefore maintains operational ties to Islamabad.
Moreover, Indian reports are claiming that at least three of the assailants were natives of Pakistan and were members of LeT. This claim has almost certainly accounted for the diplomatic fallout.
This was the worst terrorist attack targeting civilians on Indian territory since the 2008 Mumbai attack, with the publicity and success of the attack having the potential to inspire other attacks in both Jammu and Kashmir, and potentially other parts of India. India is almost certain to respond to the attack with a significant escalation in internal security measures and increased operations across Jammu and Kashmir.
This is likely to include a rise in arrests, with 1,500 already recorded, focused security raids, the expansion of checkpoints, heightened surveillance, intensified patrols, restrictions on movement and public gatherings, and the temporary suspension of communications.
Despite the major diplomatic fallout, extreme rhetoric espoused from both sides, and reports of border skirmishes, the risk of an all-out war or major escalation remains low, given that both India and Pakistan are nuclear-armed states with an established history of managing crises below the threshold of a full-scale conflict. However, there is a realistic possibility that sustained exchanges of fire along the Line of Control as of 25 April could provoke a miscalculation and eventual escalation in hostilities.
Outside of Jammu and Kashmir, a well-publicised attack on Indian tourists has the potential to instigate sectarian tensions and violent protests across India. The attack follows recent and controversial changes to the Waqf system, which governs Islamic religious endowments. These changes have sparked widespread protests within India’s Muslim community, with many viewing it as a move by the Modi administration to diminish religious and cultural autonomy, which has increased sectarian tensions.
In Pakistan, protests have erupted over India’s threats, especially regarding the threat to suspend the delivery of water to Pakistan, which is being characterised as “water terrorism”. If India decides to limit the flow of water to Pakistan from the Indus, Jhelum, and Chenab rivers, Pakistan’s water security will almost certainly be severely affected. Such a move would threaten Pakistan’s access to drinking water, its ability to generate energy and its agriculture, with approximately 80 per cent of its crops irrigated by the three western rivers.
However, India is highly unlikely to immediately alter the flow of water, partially due to legal restraints under the treaty, which prohibit the unilateral suspension, but primarily due to technical constraints, with changes to water distribution demanding substantial infrastructural developments.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Russia removes Afghan Taliban from list of banned terrorist groups
The Taliban had been on the list for two decades, and Moscow’s shift is likely to open the way for a normalisation of relations between Russia and Afghanistan. Moscow almost certainly considers establishing positive relations with the Taliban as a vital interest in both economic and security terms.
First, despite being extremely underdeveloped, Afghanistan is a crucial node in China’s Belt and Road Initiative (BRI), particularly as part of the Wakhan Corridor, which bypasses maritime routes controlled by India. Moreover, the country has vast mineral resources, including vast lithium deposits, valued at up to USD 3 trillion.
In security terms, Moscow almost certainly sees Afghanistan’s stability as key to combating the Islamic State Khorasan Province (ISKP), which was responsible for the 2024 Crocus Hall attack near Moscow, and continues to seek to expand to both the central Asian states and Russian territory.
Protesters destroy fast food restaurants in Pakistan
During the last reporting period, at least 20 American-owned fast food restaurants were vandalised by attendees of pro-Palestine protests. At least one employee was shot and killed during an attack in Sheikhupura, near Lahore. American-owned businesses, including fast food chains, have been accused of supporting the Israeli war efforts in Gaza and have been targeted in multiple countries where large-scale pro-Palestine protests have been held. It is almost certain that the restart of hostilities in Gaza in late March has significantly increased the threat to Western, and particularly American, personnel and property.
Security, Armed Conflict and Terror
Myanmar’s military junta extends ceasefire to support earthquake relief
The ceasefire, which ended on 22 April, has been extended until 30 April to support humanitarian efforts in the wake of the 7.7 magnitude earthquake which struck northwest of Mandalay on 28 March. The decision comes following the head of the junta, Min Aung Hlaing’s visit to Bangkok to meet with regional leaders, who reportedly attempted to persuade him to extend the ceasefire.
Likely, the decision was also influenced by the fact that the earthquake damaged many Tatmadaw-held areas of Mandalay, making them vulnerable to an offensive by insurgent groups in the Mandalay region. Despite the ceasefire agreement, the junta has been accused of numerous violations, most recently conducting airstrikes on Singu Township of Mandalay on 21 April, as well as blocking humanitarian aid to rebel-held areas. Further ceasefire violations will likely occur, despite the decision to extend the agreement.
Environment, Health and Miscellaneous
At least 253 people killed during Songkran celebrations in Thailand in 2025
Songkran celebrations marking the Thai New Year are known locally as the “seven dangerous days”, occurring from 11 to 17 April. According to Thailand’s Road Safety Operation Centre, a total of 253 people were killed and 1,495 injured in road traffic accidents (RTAs) during celebrations this year. Bangkok recorded the most fatalities with 19 deaths, and Phatthalung had the highest number of accidents and injuries. Only six provinces reported zero RTA deaths.
Motorcycles accounted for 84.11 per cent of RTAs, the high rate of which is largely attributed to driving under the influence, speeding, crossing lanes, and inadequate safety wear during a period of elevated traffic levels. Overall, the number of accidents significantly decreased from the same period in 2024, which recorded 480 RTA fatalities.
The decrease is highly likely due to the impact of the 28 March Myanmar earthquake, which also affected Bangkok, causing many tourists to reconsider travel to Thailand.
New Zealand healthcare workers plan strike on 1 May
On 24 April, the members of the Association of Salaried Medical Specialists (ASMS), a union of health sector workers, voted in favour of holding the first general strike since the union was established in 1989. At least 5,500 senior doctors are expected to strike nationwide, with the action motivated by pay disputes. ASMS has demanded a 12 per cent pay rise for hospital specialists, and has cited the government’s approval of only below-inflation wage increases since 2020.
In addition, union officials have accused the government of systemically underfunding and understaffing the healthcare sector, with some hospitals facing precarious operating conditions. The strike is likely to be the highest-profile labour action by healthcare workers in years. On 1 May, there is a high likelihood of limited availability of non-emergency health services at public hospitals across New Zealand.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
Haitian gangs will almost certainly continue to expand their territorial control and increase attacks across the country until significant external intervention is achieved.
President Noboa’s securing of a second term in Ecuador was likely achieved by his tough stance on organised crime and will almost certainly result in a continuation of draconian policies aimed at curbing violence.
Europe, Middle East & Africa (EMEA)
The firebombings at French prisons are highly likely an escalation by criminal groups in response to Paris’ efforts to crack down on organised crime. There is a realistic possibility of further attacks on security personnel.
In the likely scenario that Russia does not extend the ‘energy ceasefire’, significant long-range strikes against Ukrainian energy infrastructure and urban centres will likely follow, almost certainly posing risks to civilians.
Lebanon’s push to disarm Hezbollah is unlikely to succeed, with recent moves by the militant group likely aimed at buying time to regroup and continue its armed resistance against Israel.
RSF attacks on displacement camps in western Sudan are likely aimed at forcing displacement, reducing foreign oversight and securing vital ground to undermine the SAF’s control of El Fasher.
Asia-Pacific (APAC)
Further and potentially violent protests are highly likely across India after the government passes controversial amendments to the Waqf Act.
Dangerous driving conditions are almost certain to lead to increased road traffic accidents across Thailand as the country celebrates the Songkran festival.
North, Central and South America
Haiti: Gangs continue attempts to expand territorial control.
Gang violence has continued to spread in Haiti and has resulted in a series of attacks in areas previously assessed as more secure. On 10 April, gangs launched an attack in Léogâne, located approximately 30km west of Port-au-Prince, marking the onset of a surge in violence. This was followed by another gang assault in Gode, situated in the northwest of the country, on 12 April. Additional gang attacks occurred on 13 and 14 April in Madelaine, near the area of Kenscoff, to the south of Port-au-Prince, and the gangs have continued attacks in Mirebalais, approximately 40km northeast of the capital.
In response to the increased violence, the United States Embassy in Haiti updated its security alert to include multiple regions of the country, advising American citizens to avoid travel. In addition, the Heads of Government of the Caribbean Community (Caricom) issued a statement on 14 April indicating that it is deeply concerned over reports of a coalition of armed gangs seeking to seize power by force and “disrupt the transitional arrangements currently in place.” Caricom has called on the international community, particularly the United Nations and the Organization of American States, to take “all necessary measures” to support the Haitian authorities during this critical period. On 16 April, the cruise line company, Royal Caribbean, suspended its port calls to the Haitian tourist destination of Labadee in the north of the country.
Solace Global Assessment:
Recent attempts to expand their area of operations likely indicate a concerted effort to undermine the government’s authority and deny humanitarian aid to areas under gang control, particularly in and around Port-au-Prince (PAP). This strategy is likely aimed at further destabilising the state by making communities dependent on the gangs for access to essential services and will likely involve increased attacks on public services and the looting of critical supplies, as evidenced by the looting of the hospital in Mirebalais.
On 14 April and in reaction to the effective loss of Mirebalais, the Haitian government adopted a “war budget” aimed at combating the gangs. However, the budget only included USD 275,000, indicating the lack of resources available to the government and the urgent need for greater external assistance. Approximately 40 per cent of the budget will go to the Haitian military and police, with nearly 20 per cent being used to enhance security at the border with the Dominican Republic, a key entry point for illicit weapons. The remainder will be spent on social programmes focused on education, health and humanitarian assistance.
However, given the expanding territorial control of the gangs, who have consistently blocked key supply routes, looted critical supplies, and currently maintain near-total control in several regions, it is highly unlikely that the budget will have any meaningful impact in countering the gangs’ influence or restoring state control. Until significant external intervention is achieved, the gangs will almost certainly continue their attempts to expand their control and increase their attacks, resulting in a deterioration in the humanitarian situation.
Ecuador: President Noboa secures second term
On 13 April, President Daniel Nobia was re-elected following the second round of Ecuador’s presidential election. Figure’s released by Ecuador’s National Electoral Council indicate that Noboa received almost 56 per cent of the vote compared to his rival, leftist lawyer Luisa Gonzalez, who secured 44 per cent of the vote. Gonzalez has demanded a recount of the vote, suggesting that the process was marked by ‘grotesque’ electoral fraud and that pre-election polls had put her ahead of President Noboa. The vote was monitored by international observers from the Organization of American States and the European Union, but neither body has released its official reports.
Solace Global Assessment:
Noboa’s re-election was almost certainly secured by his tough stance on organised crime, which closely mirrors the strategies implemented by President Bukele in El Salvador. However, unlike in El Salvador, the imposition of states of emergencies, the mass deployment of the police and the military, and the suspension of many civil liberties have yet to yield a significant improvement in Ecuador’s security environment.
Ecuador’s challenges differ substantially from those faced in El Salvador. Gangs in Ecuador are more sophisticated and involve transnational criminal organisations such as the Mexican Sinaloa and Jalisco New Generation cartels. These organisations have entrenched themselves in Ecuador, seeking to benefit from the country’s porous borders, proximity to the major cocaine producing nations of Peru and Colombia, and to exploit Ecuador’s access to the Pacific Ocean.
Moreover, these transnational criminal organisations are far better funded and armed than the gangs in El Salvador, likely suggesting that an emulation of Bukele’s tactics is not sufficient for effectively addressing the scale of Ecuador’s security challenges.
President Noboa has recently expressed that he is willing to host US military forces in Ecuador and would welcome US support in combating organised crime in the country. The Trump administration’s recent designation of organised crime groups, including the Sinaloa and Jalisco New Generation Cartels, as Foreign Terrorist Organisations (FTOs) could provide a foundation for increased US involvement. The designation, combined with Trump’s commitment to combating organised crime, could result in greater access to intelligence-sharing, specialised resources, and in the long term could potentially involve direct US military support to combat the cartels, although initial Ecuadorian plans only involve the US providing supportive roles, such as intelligence gathering and surveillance operations.
Ecuador is currently constructing a naval base in the city of Manta, and there are proposals to host the US military there. If the US establishes a naval presence on the Ecuadorian coast and is involved in maritime interdiction efforts, this could disrupt cocaine smuggling from Ecuador and ultimately deter transnational organised crime groups from operating in the country, a development that would likely improve Ecuador’s internal security.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
USA gets El Salvador’s support for further deportations
On 14 April, US President Donald Trump met his Salvadoran counterpart, Nayib Bukele, in Washington. The president of the Central American country endorsed Trump’s plans to carry out further deportations of migrants, and possibly US citizens who commit crimes, to his country. Moreover, Bukele backed Trump over the issue of a citizen of El Salvador who was deported despite having protected status, a decision that the White House has refused to reverse.
El Salvador, which in recent years has built massive prisons to house more than 80,000 individuals accused of having ties to criminal groups, has increasingly portrayed itself as a means for the US to “offshore” its migrants abroad. A growing partnership between San Salvador and Washington is likely to drive civil unrest in the US. High-visibility deportations, such as those of the Salvadoran citizen or those of Columbia University activists, are particularly likely to result in protests in large cities and near university campuses.
First report on Dominican Republic roof collapse released
The document was published by the government on 11 April. Notably, the report did not clarify what caused the incident, which killed 221 people at a packed nightclub in the country’s capital, Santo Domingo. The incident is one of the largest mass casualty events in the country’s history and has attracted massive domestic and international attention. Consequently, as more details emerge, there is a realistic possibility of civil unrest, especially if investigations indicate the government was at fault or the accident was a result of corruption.
Deaths of two football fans result in protests in Santiago, Chile
Two individuals, including a minor, were killed during a stampede at the Monumental Stadium on 10 April. On the following day, protests erupted in multiple parts of the capital, including downtown Santiago, La Pintana, Cerro Navia, and San Joaquín. According to local media, protests began peacefully as groups of fans of the Colo-Colo football club gathered near the stadium before a Copa Libertadores match. However, a group of protesters reportedly began to throw rocks at police and passing vehicles. The spread of the protests throughout the night resulted in limited traffic disruptions and some cases of vandalism.
Argentina secures USD 20 billion deal with the International Monetary Fund (IMF)
The announcement follows Buenos Aires’ decision to lift its strict currency controls, which limit the ability for Argentine nationals to purchase US Dollars, and to float the official Peso exchange rate. The IMF has stated that it would transfer USD 12 billion upfront on 15 April, an unusually large amount. The deal is a political victory for President Javier Milei, but the possibility of significant currency devaluation following the deal, which could push inflation higher, may drive short-term civil unrest.
Security, Armed Conflict and Terror
US Army to control parts of the US-Mexico border
On 15 April, the Trump administration announced the emergency transfer of nearly 110,000 acres of federal land along the US-Mexico border within New Mexico. The move is almost certainly part of Trump’s broader efforts to improve border security, disrupt drug smuggling and deter illegal immigration and could authorise the US Army to detain migrants. The move to detain migrants is likely to be challenged in the courts, although US Army personnel would technically not be detaining migrants but rather trespassers on military land.
The land only encompasses a 170-mile section of a nearly 2,000-mile border, but will likely drive migration flows to other parts, potentially enabling law enforcement to focus resources on a more concentrated area. Moreover, approximately 30 per cent of the US-Mexico border is federally owned, suggesting that such a strategy could be greatly expanded to cover additional sections of the border if deemed effective.
Environment, Health and Miscellaneous
Pennsylvania governor’s residence firebombed
On the night of 13-14 April, an individual reportedly broke into Governor Josh Shapiro’s residence and started a fire, which destroyed parts of the building but resulted in no injuries. The perpetrator reportedly turned himself in and stated that he planned to kill Shapiro. Early authority reports state that the perpetrator was motivated by a “deep hatred” for Shapiro.
The incident is almost certainly to be politically motivated and to be linked to the high visibility of the target. Shapiro is one of the key Democratic politicians in the early race for the 2028 presidential nomination and was considered a front-runner to be Kamala Harris’s running mate in 2024. Moreover, there is a realistic possibility that the attack was religiously motivated, as it took place only hours after a Passover Seder dinner.
Increasing signs of volcanic activity from Mount Spurr, Alaska
The US Geological Survey (USGS) has detected hundreds of small tremors within a 30-mile radius of Alaska’s Mount Spurr, resulting in it issuing an advisory warning that the volcano is likely, but not certain, to erupt in the next weeks to months. The volcano lies around 129 km (80 miles) west of Anchorage, the largest city in Alaska, which is comprised of almost 300,000 inhabitants. The authorities have instructed citizens to be vigilant and prepare in case of widespread disruption caused by ash and other volcanic material, which is likely to shut down air travel. However, this has reportedly resulted in panic buying in the area, with locals in anticipation of a state of emergency, amassing food, N95 masks and other critical supplies.
Aftershocks possible after earthquake registered near San Diego, California
On 14 April, a 5.1 magnitude earthquake was registered near Julian, California, with tremors felt in San Diego and as far away as Los Angeles. Initial damage assessments are ongoing, but no major damage has been recorded. However, at least seven aftershocks have been recorded, increasing the chances of structural strain in the affected areas. Governor Gavin Newsom has been briefed, and the authorities are reportedly on high alert to respond to any further seismic activity.
Europe, Middle East & Africa
France: Coordinated attacks against prisons
On the night between 14 and 15 April, coordinated firebombings and shootings occurred at various prisons across the French mainland, including in Valence, Marseilles, Nanterre, and Toulon. Some of the attackers reportedly wrote the acronym “DDPF” on torched police vehicles or prison walls. “DDPF” highly likely means “Droits des Prisonniers Francais” – Rights of French Prisoners. In the early hours of 16 April, another attack was recorded at a prison in the town of Tarascon in southern France, only hours after the French government commented on the first wave of incidents. The attacks, while not resulting in any casualties, are almost unprecedented in scale and scope.
Solace Global Assessment:
French media have claimed that the attacks were carried out by organised criminal groups, and that they are in response to the government’s prison reform efforts. Paris has recently pledged to open a new maximum-security facility in July 2025 to house approximately 100 drug trafficking leaders. Moreover, the government has more broadly intensified its efforts to combat drug trafficking, and drug seizures have increased in 2024 compared to previous years. This has continued in 2025: in March, French police seized ten tonnes of cocaine in Dunkirk in a single raid, an amount which is approximately equal to a fifth of the total seizures of 2024.
The attack almost certainly demonstrates a growing vulnerability of the French state against organised groups, and is meant to send a political message by attacking symbols of France’s security apparatus. French organised criminal groups are extremely well armed and have shown their ability to carry out sophisticated attacks. A notable example of this was the ambush on a prison van that led to the (temporary) escape of jailed drug trafficker Mohamed Amra in May 2024.
The scope and scale of the attacks pose an almost certainly immense pressure on the Macron government, which has long faced accusations of being unable to contain criminality in France. They will, therefore, highly likely force the government to respond aggressively, possibly tackling organised criminal groups in at-risk cities like Marseille, Nice, and Grenoble. However, such a development could result in tit-for-tat escalations on the part of the gangs. There is a realistic possibility of further coordinated attacks targeting security personnel and offices, which would pose a severe threat to bystanders.
Ukraine: Deadliest attack of the year on Sumy City and Kremlin reiterates war goals
On 13 April, two Russian ballistic missiles struck Sumy City during Palm Sunday, killing at least 35 people and wounding 117. The attack is the deadliest strike on Ukraine thus far in 2025. Moscow claims that the attack involved two Iskander ballistic missiles targeting a gathering of Ukrainian personnel, killing 60.
The US President Donald Trump called the attack “terrible”, but he had been told that Russia “made a mistake”. Trump furthermore restated his belief that Ukraine started the war. One of the missiles struck a road in Sumy’s busy city centre, which caused the most casualties.
Local media reports indicate that a medal ceremony for veterans was being held in Sumy on the day of the attack, with Ukrainian President Volodymyr Zelensky sacking Sumy’s regional chief on 15 April for hosting the event.
The attack occurred within the context of an assessed developing new spring offensive by Russian forces in northeastern Ukraine and ongoing attempts by Washington to engage in separate bilateral peace negotiations with both Ukraine and Russia. On 11 April, Trump’s Special Envoy to Ukraine, General Keith Kellogg, suggested that a ceasefire agreement could see partitioned areas of responsibility for Ukraine (as in post-WWII Germany) between an Anglo-French “reassurance force” alongside Ukrainian forces west of the Dnipro River, solely Ukrainian forces in Ukrainian-held eastern Ukraine, and Russian forces in Russian-occupied southern and eastern Ukraine, with a 29-kilometre-wide “demilitarised zone” across the current frontline.
The Kremlin and Kremlin-affiliated media channels rejected the proposal outright, and Russia’s head of the Foreign Intelligence Service and Foreign Minister both reiterated Moscow’s position that peace would require the fulfilment of Russian President Vladimir Putin’s stated war goals from his 14 June 2024 speech.
Solace Global Assessment:
Despite Washington’s efforts to broker a peace agreement between Moscow and Kyiv, the Kremlin has not yet indicated willingness to make even marginal concessions on any of its maximalist war goals. Stated most clearly in Putin’s June 2024 speech, and reiterated this past week, these include: the demilitarisation and ‘denazification’ (regime change with imposed puppet government) of Ukraine, annexation of all southern and eastern Ukraine (including currently unoccupied areas), and enforced Ukrainian neutrality with a ban on joining any security arrangements (particularly NATO).
This has been reflected by Russian military action, with the developing northeastern spring offensive highly likely intended to gain further leverage to achieve these maximalist objectives. The ballistic missile strikes on Sumy City, which resulted in significant civilian casualties, likely reflect Russia’s growing focus on targeting both Sumy and Kharkiv, as the two urban centres present the primary axes for the potential new northeastern offensive.
It is highly likely that intensified Russian strikes against these locations will continue in the coming weeks, with glide bomb and one-way attack uncrewed aerial vehicle (OWA-UAV) attacks already occurring in the days following the 13 April Sumy strikes, posing significant risks to both civilians and foreign nationals operating in these areas.
While Moscow previously presented a more optimistic narrative of the US-Russia negotiations, Kremlin officials have been increasingly forthright about the inability of the talks to provide results. It is likely that Moscow will continue to leverage the talks as far as possible to gain immediate concessions, so that it may better pursue its maximalist war goals on the battlefield.
This assessment is reflected by the likely continued use of the moratorium on long-range strikes against energy infrastructure as a means to pressure Washington to punish Ukraine for violations. Since the ‘energy ceasefire’ was implemented, Russia has accused Ukrainian forces of violations on an almost daily basis, most of which have been unsubstantiated. With the moratorium set to last 30 days and expiring on either 16 April or 23 April (due to the different understandings of when it actually began), there have been no indications yet of an extension. It is likely that Moscow will leverage the unsubstantiated claims of Ukrainian violations to justify not extending the moratorium.
In this scenario, it is highly likely that mass Russian long-range strikes against Ukrainian critical national infrastructure (CNI) will follow. These strikes could further deplete Ukraine’s stockpile of advanced air interceptor munitions (particularly Patriot), a depletion that Moscow is likely motivated to achieve given the reduced likelihood of replenishment under the Trump administration. Previous interceptor shortages, caused by delays in US Congress approval, led to a drastic increase in Russian long-range strike efficacy rates. An increase in strikes against Ukrainian CNI would almost certainly pose considerable risks of collateral damage, with even successful interceptions posing dangers due to debris.
Lebanon: President seeks to disarm Hezbollah this year
Lebanese President Joseph Aoun has stated that he hopes to achieve the disarmament of the Shia militant group, Hezbollah, by the end of 2025. President Aoun stated that his intent is for all of Hezbollah’s weapons to be withdrawn or that their possession will be restricted to the state. He also stated that Hezbollah was ultimately a Lebanese group and that members could join the Lebanese Armed Forces (LAF) if they participated in “absorption courses”. However, President Aoun stressed that Hezbollah would not be able to function as a distinct unit within the Lebanese Army.
A spokesperson for Hezbollah recently commented that the group would be willing to disarm if Israel fully withdraws from Lebanon, with the Israel Defense Forces (IDF) still holding five strategic locations in the south of the country. However, this statement has been denied by key figures within Hezbollah and by the group’s media office.
Solace Global Assessment:
The majority of Hezbollah military sites in southern Lebanon are now under the control of the LAF, after Hezbollah agreed to withdraw from 190 out of 265 positions as part of the ceasefire agreement achieved with Israel in November 2024. While this withdrawal could be interpreted as an act of good faith and a move that is in alignment with the provisions of UN Security Council Resolution 170, it is unlikely to be reflective of a broader effort to disarm or demobilise.
The IDF still maintain key terrain in southern Lebanon, in violation of the same resolution, and Israel’s Defence Minister, Israel Katz, stated on 16 April that IDF units will remain in Lebanon indefinitely to guarantee the security of Israel. It is highly unlikely that Hezbollah would accept disarmament while these conditions are present.
In addition, recent intelligence has purportedly uncovered Hezbollah external attack plans, European drone smuggling networks, the resumption of arms production within Lebanon and Iranian attempts to facilitate lethal aid to the group, via both maritime smuggling networks and attempts to reestablish ground lines of communication through Syria. Moreover, Hezbollah senior leadership, including Secretary-General Naim Qassem, have reiterated their commitment to the principle of armed resistance against Israel, framing it as a non-negotiable component of Lebanese national defence and urging for patience among Hezbollah’s base.
After Israel’s campaign against Hezbollah, which has destroyed much of the group’s key equipment and degraded its leadership, Hezbollah is almost certainly not in a position to sustain major operations against Israel, especially after losing its main supply routes in Syria. Recent actions have likely been intended to alleviate both domestic and international pressure on Hezbollah and to create space for the group to reorganise and regroup.
Hezbollah has likely adapted its targets, seeking more covert methods to resupply and has dispersed its forces to minimise opportunities to be further degraded by Israel. Further reporting may indicate that the group is evolving its attack methodology, with evidence that it has been planning external attacks against Israel in coordination with Iran, and uncorroborated reports suggest that as many as 400 Hezbollah commanders have relocated to South American countries, where the group has an established network primarily involved in illicit finance, logistics, and transnational organised crime in support of the group’s wider objectives.
The Lebanese government’s approach to Hezbollah’s disarmament has consistently favoured dialogue and political negotiation over the use of force. An attempt to forcibly disarm Hezbollah is unlikely to be successful and could provoke a violent retaliation, which could ultimately threaten civil war in Lebanon. The LAF are unlikely to be in a condition to actively confront Hezbollah without risking a major escalation, as the militant group still maintains an assessed fighting force close to 100,000 and a credible arsenal of weapons.
Furthermore, Hezbollah’s rank and file remain ideologically committed to armed resistance and perceive the group to be a guarantor of national defence, not a destabilising force within Lebanon. Even if progress towards disarmament, demobilisation or integration were to be made, there is a high threat of factionalism, especially after Israel’s recent campaign. Splinter groups would likely emerge from more hardline factions, which would likely operate independently of a centralised command and potentially align with other external actors of transnational organisations, a development that could jeopardise Lebanon’s stability or provoke further Israeli intervention.
Sudan: Paramilitary forces coordinate attacks on displacement camps
On 11 April 2025, the paramilitary Rapid Support Forces (RSF) launched a coordinated attack across North Darfur, which involved attacks on the besieged state capital, El Fasher, and several targets within the wider area. As part of the offensive, RSF claimed control of Zamzam and Abu Shouk displacement camps, stating they had “liberated” them from the Sudanese Armed Forces (SAF). RSF personnel reportedly began burning buildings and shelters within the camps in an effort to identify and capture SAF personnel allegedly hiding among civilians.
A separate RSF attack was carried out in Um Kadadah, approximately 180 kilometres east of El Fasher. Reports from the area indicate multiple fatalities, with accounts suggesting the killings were based on ethnicity.
Current estimates indicate that the attack on Zamzam camp has resulted in the displacement of between 60,000 and 80,000 households or up to 400,000 people, according to the UN’s International Organisation for Migration. At least 400 civilians have been confirmed killed during the operations, with the actual number assessed to increase substantially, with reports of ongoing killings and heavy use of artillery. Aid workers from Relief International operating a clinic in Zamzam camp were also reportedly deliberately targeted during the assault.
Solace Global Assessment:
The RSF attacks in the El Fasher area are highly likely reflective of a strategic effort by the group to consolidate control over the entire Darfur region. The RSF almost certainly views the capture of El Fasher, the last Sudanese Armed Forces (SAF) stronghold in North Darfur, as integral to achieving this objective and will likely continue their offensive operations in the area.
The RSF likely attacked the displacement camps for several reasons. Zamzam camp is located on the intersection of multiple main supply routes, the A5, A43 and B26. Control of Zamzam would likely enable the RSF to severely disrupt SAF logistics and deny SAF units the opportunity to mutually support one another, especially in El Fasher. The attacks were also likely a form of retaliation for the RSF’s recent loss of Khartoum, with the withdrawal of forces from the capital likely enabling the redeployment of RSF personnel and resources to Darfur.
The RSF’s broader strategy likely includes forced displacement and the deliberate targeting of civilians perceived to support the government. The RSF’s objective is likely to punish communities supportive of the SAF, to instil fear among the civilian population, deny humanitarian access and to expropriate critical aid resources such as food and medicine.
This campaign may also aim to forcibly remove ethnic communities from parts of Sudan, contributing to patterns of ethnic cleansing. The reports of the deliberate targeting of humanitarian actors may be intended to deter aid groups from operating within RSF-controlled areas, a strategy that will reduce international oversight and help enable the group to commit acts of genocide with impunity.
The attacks and subsequent displacement of an estimated 400,000 people are almost certain to result in the deterioration of the humanitarian situation. It is estimated that 25 million people, approximately half of Sudan’s population, are already facing extreme hunger, a number that has likely increased since the cessation of USAID, which accounted for almost half of all aid to Sudan.
Deliberate RSF attacks on displacement camps, the killing of aid workers, the disruption of aid routes and the destruction of critical infrastructure will almost certainly increase internal displacement, increase mortality rates, overstretch humanitarian efforts and lead to increased cross-border refugee flows.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Protests likely in London over UK Supreme Court gender identity decision
On 16 April, the UK’s highest court ruled that the definition of “woman” under equality legislation will only apply to the category of “biological sex”. The ruling relates to a case regarding gender recognition certificates, documents that certify someone’s gender transition. While the court stated that trans people would not be discriminated against under the new ruling, the landmark decision will likely provoke a reaction from LGBTQ advocacy groups.
Protests are likely in London during the 17-21 April bank holiday weekend. While these protests are likely to be small and peaceful, there is a realistic possibility of limited public transport or road blockades, particularly in London’s Strand area, where the court is located.
Spanish anti-tourism protests likely to intensify over Easter
Several anti-tourism groups have called for unrest during the 18-20 April weekend in opposition to perceived overtourism at high-visibility destinations. Locations where protests are likely to occur include the main towns in the Canary Islands, Malaga, Barcelona, Valencia, and smaller centres that have highly popular Easter celebrations, like Valladolid, Leon, and Segovia.
Anti-tourist sentiment has increased in Spain since the COVID-19 pandemic, and particularly since 2023. As the high tourist season approaches, protests are highly likely to intensify. While most of the unrest is peaceful, there is a realistic possibility of isolated cases of harassment, vandalism or violence against tourists or their property.
Protests likely in Italy on 25 April
The commemoration of Italy’s liberation from the fascist regime is likely to coincide with protests in Rome, Bologna, Milan, and other large cities. In 2024, clashes between pro-Palestine and pro-Israel protesters were recorded in Rome, while, in Milan, protesters clashed with responding police in Piazza Duomo. Protests in 2025 are likely to be particularly large, as the commemoration marks the 80th year since liberation (25 April 1945).
Hungary continues to repress LGBTQ+ community
On 14 April, the Hungarian parliament continued its repression of the LGBTQ community by passing an amendmentto the Hungarian constitution which permits the government to ban public events organised by the LGBTQ community. The amendment passed with 140 votes in favour and 21 against, easily surpassing the two-thirds majority that it required, despite opposition members and supporters attempting to block access to the parliament building.
The amendment is the most recent act of part of a broader campaign by Prime Minister Viktor Orbán and his ruling Fidesz-KDNP coalition, who are highly likely attempting to appeal to their conservative base ahead of the 2026 election. However, opposition parties, civil rights organisations, and many members of the Hungarian public have condemned these measures, describing them as authoritarian, intentionally discriminatory towards minority groups, and designed to restrict civil liberties.
The government’s agenda has already sparked widespread unrest and periodic demonstrations, some of which have led to violent interactions with the police. This latest amendment is likely to provoke further protests, as opposition to Orbán’s increasingly illiberal policies continues to grow. The threat environment for LGBTQ travellers to Hungary has almost certainly deteriorated, with these travellers increasingly likely to be targeted by harassment or even assault.
Serbian anti-corruption protests continue
Anti-corruption protests have continued to be organised across Serbia and were likely rekindled after Serbian President Vučić held a large rally in Belgrade to show support for his leadership amid the ongoing protests. On 14 April, protestors blocked the city administration office in Vrsac, followed by a protest outside the state-owned broadcaster in Novi Sad on 15 April. The same day, another protest took place at the state broadcaster RTS in Belgrade, and a student protest occurred in Nis.
The EU stated on 15 April that it will ban Serbia from joining the bloc if President Vučić attends a Victory Day parade in Russia on 9 May, after being invited by President Putin. President Vučić’s attendance would likely be a catalyst for further protests, with approximately 40 per cent of the country supporting joining the EU, although this number is likely to be much higher among the sections of the population currently involved in the anti-corruption protests.
Algeria expels 12 French diplomats
The announcement followed the arrest of an Algerian consular official in France, suspected of having participated in the abduction of a French-based Algerian anti-government influencer in 2024. The development marks a further escalation in tensions between Algeria and France, which encompasses the areas of security, immigration, and domestic politics.
The latest expulsions are likely to prompt a reprisal from Paris. However, this is likely to result in a tit-for-tat escalation. In France, there is a realistic possibility that growing tensions with Algeria will drive protests and possibly political violence. In January 2025, France arrested several influencers who had allegedly used social media to call for violence against French citizens in response to Paris-Algiers tensions.
Malian authorities shut down Canadian mining company
The authorities in Mali have shut down the office of the Canadian mining company Barrick Gold in the capital, Bamako, over the alleged non-payment of taxes. The move follows multiple disputes between Barrick Gold and the Malian government, following the junta’s imposition of a new tax code, which demanded the payment of retroactive taxes. This development is indicative of a wider trend across the Sahel, where military-led governments are increasingly asserting control over natural resource sectors and taking punitive action against Western firms, while increasing cooperation with strategic rivals like Russia and China.
Junta easily wins elections in Gabon
Exit polls on 13 April indicated that approximately 90 per cent of the vote went to General Brice Oligui Nguema, the leader of the junta that carried out a successful coup in 2023, ousting the powerful Bongo family that had ruled the country since 1967. While some observers remarked that the elections were fair and transparent, several irregularities were noted, including some reports of ballots being tampered with. The vote is almost certainly an important political boost for the junta, which has pledged to prioritise economic reform and a bolder foreign policy in the medium term.
Main opposition party barred from contesting election in Tanzania
Tanzania’s main opposition party, Chadema, has been disqualified from participating in the October 2025 elections after failing to sign a mandatory code of conduct by the mandated 12 April 12 deadline. The exclusion of Chadema follows the arrest and treason charges filed against the party’s leader, Tundu Lissu, who was charged on 6 April after he called for electoral reforms at a political rally.
Lissu had been expected to challenge President Samia Suluhu Hassan in the upcoming elections, with her Chama Cha Mapinduzi (CCM) party maintaining its grip on power since 1977. These developments have been widely criticised by both internal and external observers, raising fears of a push towards authoritarianism, despite Hassan’s initial praise for her efforts to reverse some of the more repressive policies of her predecessor.
There is a realistic possibility of civil unrest in the country after the disqualification of Chadema, the ongoing repression of opposition figures and general pattern of democratic backsliding.
Security, Armed Conflict and Terror
Anarchists bomb Hellenic Train offices in Athens, Greece
On the night of 11-12 April, an improvised explosive device (IED) detonated outside the offices of the Greek railway company in Athens. The attack damaged the office building but resulted in no casualties, and, according to local media, multiple anonymous calls were made to police warning them about the danger.
The attack was claimed by a local anarchist group, the Revolutionary Class Self-defence Group. In Greece, anarchists and other far-left activists often carry out bombings targeting state institutions or private companies. Most of these attacks happen at night to minimise the risk of civilian casualties. The bombing is almost certainly linked with the ongoing unrest related to the 2023 Tempi railway disaster, which killed 57 people, most of whom were students.
Kurdish-led SDF withdraw from Tishreen Dam in Syria after agreement with Damascus
On 14 April, the Kurdish-led and US-backed group Syrian Democratic Forces (SDF), which de facto autonomously controls northeastern Syria, withdrew from the strategically significant dam. The withdrawal follows an agreement made by the SDF with the transitional government led by President Ahmad al-Sharaa.
The issues of Kurdish rights, autonomy, and the aggression of Turkish-led Syrian National Army (SNA) militants, in addition to conventional Turkish forces, have been a key challenge to the stability of the new post-Assad Syria. With Tishreen Dam being the primary site of heavy fighting between the SDF and SNA (with Turkish air support) in the past few months, the deconfliction agreement will likely lessen tensions in the area and risks of further conflict escalation.
However, there remain key issues to be resolved despite agreement from the SDF to ultimately integrate into the national military, with the SDF commander-in-chief Mazloum Abdi stating that the SDF need both federalism and quasi-autonomy as a separate bloc within the national army, conditions that Damascus is unlikely to agree to.
Jordan arrests 16 involved in possible Hamas plot
Jordanian authorities stated, on 15 April, that they arrested a cell aiming to “threaten national security”, via improvised drones, rockets, and explosives. Local and international media quoted security sources’ allegations that the 16 were part of Hamas. It is highly likely that the cell was operating with Iran-sourced supplies, and to arm Palestinian militants in the West Bank.
Jordan remains the key country for Iranian smuggling routes towards the West Bank. The kingdom has likely aimed to remain ambivalent, seeking to both avoid a confrontation with Iran, which could drive protests among the largely pro-Palestinian public, and to reduce the destabilising impact of Iranian arms being present on its territory.
The latest arrests are likely either reflective of Jordanian security forces’ assessment that the cell constituted an unacceptable domestic security threat or, less likely, could be meant as a signal to Tel Aviv and, more broadly, Washington, at a moment where the situation in both Gaza and the West Bank is precarious.
Further briefings made regarding potential ground offensive against Houthis in Yemen
‘Yemeni and US officials’ briefed the Wall Street Journal (WSJ) in an article published on 15 April that Yemeni militias are planning a ground offensive against Houthi-controlled Hodeidah. This adds to previous briefings made to CNN in an article published on 6 April from ‘regional diplomatic sources’. Private American security contractors have reportedly advised the Yemeni factions on the potential offensive.
Riyadh is likely reluctant to return to open civil war in Yemen due to the reputational and economic costs associated, and the potential offensive would likely be mainly conducted using the United Arab Emirates (UAE)-backed Southern Transition Council’s (STC’s) forces with US air support. This assessment has been further supported by the WSJ report, which states that Saudi officials ‘have privately told American and Yemeni officials they won’t join or help a ground offensive in Yemen again’, although this position is likely to change if the Houthis directly attack Saudi Arabia.
Should the civil war be reignited with an STC-led ground offensive towards Hodeidah, it is likely that the Houthis will attempt long-range strikes with either or both ballistic missiles and long-range one-way attack uncrewed aerial vehicles (OWA-UAVs) against targets in the UAE. Previously, the Houthis primarily attempted to strike targets in the vicinity of Abu Dhabi, including oil refineries, the international airport and Al Dhafra airbase.
US and Iran begin talks in Muscat
On 12 April, delegations from Washington and Tehran met in Muscat, Oman, to begin negotiations regarding Iran’s nuclear program. Tehran previously refused the prospect of direct talks with the US; however, US President Donald Trump’s threats of a bombing campaign, in combination with increasing concerns of a planned Israeli attack later this year, likely compelled Tehran to concede to direct talks.
In the initial meeting, clear red lines were set by both delegations. The Iranian delegation, led by Foreign Affairs Minister Abbas Araghchi, stated that Tehran requires guarantees on sanction relief, access to its frozen assets, and the end of the ‘maximum pressure’ campaign spearheaded by the Trump administration. The US delegation, led by US Special Envoy to the Middle East Steve Witkoff, has indicated that their fundamental demand is the abandonment of Iran’s nuclear weapons program.
With the Iranian regime likely in its most geopolitically vulnerable position in decades, Tehran is likely highly susceptible to US pressure. Nonetheless, the incentive for a nuclear deterrent has almost certainly increased, precisely because of their current vulnerability following the fall of the Assad regime, the degradation of their previously primary regional deterrent, Lebanon’s Hezbollah, and the weakening of their air defence capabilities by Israeli military operations.
Should the talks fail to achieve results, it is likely that the US, with the support of Israel, will pursue a military solution that risks broader escalation across the Middle East. There is a realistic possibility that even if Washington feels it is making progress in the talks (or even agrees to a deal), Israel’s government could still pursue a military escalation with Iran later in the year.
Eight Pakistani citizens killed in eastern Iran
Islamabad has demanded answers after eight Pakistani nationals were killed on 13 April by separatists in Iran’s Sistan-Baluchestan province, which shares a border with Pakistan’s restless southwestern Balochistan province. The Baloch Nationalist Army (BNA), a Pakistani separatist group, has claimed responsibility for the attack.
The victims were all from the Punjab areas of Pakistan and were attacked when working at a workshop in Mehrestan county, located roughly 230km (142 miles) from the Pakistan border. The attack is likely indicative of increased cross-border operations by Baloch separatist groups, who have increased attacks on Punjabis, who are viewed as an extension of Pakistan’s government and military.
Iran and Pakistan have repeatedly accused each other of harbouring militants in their respective territories. Moreover, both nations have conducted strikes inside each other’s territory in support of counter terrorism operations, most notably in January 2024, when Iranian missile and drone strikes in Pakistan were met with retaliatory strikes.
There is a realistic possibility that Pakistan may retaliate if it deems Iran’s response to separatists insufficient, increasing the risk of cross-border tensions in the coming weeks.
Medical services suspended after looting of hospital in Upper Nile State, South Sudan
On 14 April, dozens of armed men stormed a hospital in Ulang, Upper Nile State operated by Médecins Sans Frontières (MSF) and stole vital medical supplies and equipment. The raid forced the hospital, which was the only functioning health facility in the area, to close. At least 100 patients were receiving treatment including trauma, maternity, and paediatric care at the time, and many were forced to flee.
Similar patterns of violence targeting healthcare in the region has taken place in recent months; in January 2025, armed men attacked two MSF boats on their way to Ulang. Violence has re-ignited in the White Nile State since early March 2025, when the White Army launched attacks targeting the South Sudan People’s Defence Forces in a conflict that has threatened to reignite the South Sudan civil war. Further targeting of healthcare facilities in the region is highly likely.
Al-Shabaab claim control of Adan Yabaal during the ongoing Somalia offensive
On 16 April, al-Shabaab militants released a statement claiming control of Adan Yabaal, a town in the Middle Shabelle region, northeast of Mogadishu. They also claimed to have overrun 10 military installations in the region. If true, this constitutes a major strategic loss for Somali forces, who have used the town as a launch pad for counterinsurgency operations in Middle Shabelle against the al-Qaeda-linked al-Shabaab.
The Somali military has denied the group’s capture of Adan Yabaal, claiming that government forces repelled an al-Shabaab attack. This is the latest in a series of government setbacks, with al-Shabaab recently seizing control of the Afgoye-Mogadishu and Mogadishu-Balcad corridors. Al-Shabaab will highly likely intensify attacks on the capital, Mogadishu, following their recent strategic gains.
Spate of attacks kills over 50 in Nigeria’s Plateau State
On 14 April, over 50 people were killed after villages were attacked in Nigeria’s Plateau State, with several others injured and over 2,000 displaced. The attackers, believed to be cattle herders belonging to the Muslim Fulani community, also looted and burned homes, with the majority of the victims reportedly Christian. This follows a series of deadly incidents in the region, including the killing of 52 people two weeks prior. Fighting between Fulani herders and Christian farmers is a regular occurrence in the region, but the attack has raised concerns that attacks are increasing in frequency, largely driven by resource competition resulting from the effects of climate change. There is a realistic possibility of increased attacks over the Easter holidays, with militants establishing a pattern of targeting Christian communities around significant religious dates.
Environment, Health and Miscellaneous
Storm Olivier triggers flooding in Spain
Storm Olivier has continued to cause significant disruptions across Spain. Spanish weather services have issued alerts for rain, storms, and snow in Castile and León. On 14 April, orange and yellow warnings for wind and heavy rain were in effect in northern and northeast Spain, as well as the Balearic Islands.
The storm has caused severe flooding in the Canary Islands, particularly on Lanzarote, where a state of emergency was declared on 12 April due to heavy precipitation, leading to 150 emergency calls in just two hours. Recovery efforts are underway as officials have organised fire crews to assist with pumping efforts. Five people sustained minor injuries, and there were power interruptions reported in Costa Teguise.
Various regions of Spain have been placed under weather alerts. On April 11, Andalusia was on an orange alert due to significant risks posed by the storm, while other regions like Asturias, Castillas, Extremadura, Galicia, and Melilla were on yellow alerts. Madrid experienced rain and hail, and a landslide blocked a road on Tenerife.
Asia–Pacific
India: Protests erupt over controversial Waqf bill
Widespread protests have broken out across India following the passage of controversial amendments to the Waqf Act by the Lok Sabha, which was originally passed on 4 April. Opponents of the amendments have argued that they would dilute the rights of Muslims to manage religious-based endowments or “waqfs.”
In particular, the inclusion of non-Muslims in the management of waqfs has generated fears that the federal government, which is led by the Hindu nationalist Bharatiya Janata Party (BJP), is engaging in discriminatory practices, and opponents have stressed that other religious communities can continue to retain full control over their respective faith-based institutions.
Prime Minister Narendra Modi’s BJP has defended the amendments, stating that they are intended to enhance transparency and address corruption and mismanagement within the waqf administration.
Protests have occurred across multiple cities in India, but have been particularly intense in West Bengal. In Murshidabad, violent demonstrations involving stone throwing and Molotov cocktails broke out on 11 April and have resulted in the deaths of at least three people and the arrest of 118.
In response to the violence, the Kolkata High Court ordered the deployment of central forces to Murshidabad, and the West Bengal home secretary has imposed restrictions on public gatherings and suspended internet services in certain areas. On 14 April, protesters blocked the national highway outside Kolkata and set multiple vehicles on fire, as well as gathering in Bhangar, setting a barricade alight. On 15 April, the regional Andhra Pradesh party filed a petition challenging the bill with India’s Supreme Court.
Solace Global Assessment:
Waqf, meaning “confinement and prohibition”, is a charitable endowment under Islamic law in which donated properties managed by waqf boards are used for schools, orphanages, hospitals, banks, and graveyards. Once established, these properties cannot be sold or transferred and are considered Allah’s property to be used for charitable purposes. Waqf properties have become a significant asset class in India, encompassing approximately 870,000 properties spread over 940,000 acres of land, making waqf India’s third-biggest property holder.
The waqf bill introduces significant changes to the management of waqf properties. Key provisions include restricting waqf creation to Muslims practising Islam for at least five years, the elimination of the “waqf by user” common law establishment of waqf properties, ensuring family waqf do not deny inheritance to female heirs, the inclusion of female Muslims, non-Muslims, and various Muslim sect representation in the Central Waqf Council and State Waqf Boards, and tightening the registration and procedures for waqfs.
These measures are controversial among India’s Muslim community, who view the amendments as eroding religious autonomy, breaking from tradition by giving non-Muslims, women, and other historically underrepresented Muslim sects more control over waqf administration, and potentially invalidating properties that are considered waqf but lack the formal documentation. While the act is framed as easing administration and introducing “progressive” measures, opponents argue that the bill will eliminate many existing waqf properties and expose waqf properties, including historic mosques, shrines, shops, graveyards, and vast tracts of land to legal disputes, state confiscation, or even demolition.
The bill is perceived as a deliberate repressive measure towards the Muslim community. Since gaining power in 2014, Modi, a Hindu nationalist, has employed anti-Muslim rhetoric and discriminatory acts towards the Muslim community. The act is highly likely designed to spark a backlash and inflame the Muslim community while appealing to the BJP’s Hindu nationalist base. The challenge to the Waqf Amendment Bill will almost certainly generate more publicity for opposition to the bill and drag out the public debate, which will highly likely inflame further protests.
Thailand: Surge in traffic accidents during Songkran celebrations
Statistics from 16 April, six days into what is domestically known as the “seven dangerous days”, list over 1,000 extra road traffic accidents (RTAs) during the Songkran holiday period. The increase in RTAs has resulted in almost 200 deaths and over 1,000 injuries nationwide.
The leading causes of accidents are speeding (44 per cent) and drunk driving (25 per cent), with motorcycles involved in over 80 per cent of all incidents. The highest number of fatalities has been recorded in Bangkok, although accidents have been observed nationwide, with the southern province of Phatthalung recording the most overall accidents. Thai authorities have deployed additional trains and buses to reduce congestion and support safer travel.
Solace Global Assessment:
Songkran, meaning “passage of the sun”, occurs from 13 to 15 April each year (although celebrations usually extend from 11 to 17 April) and celebrates the Thai/Buddhist New Year. It is one of Thailand’s most important holidays and is marked by nationwide celebrations including parades, religious festivities, and family gatherings. The festival attracts many tourists, stretching transportation networks and local infrastructure. In 2024, approximately 1.9 million foreign tourists visited Thailand during Songkran, which was a 37.54 per cent increase from the year before, something attributed to government measures to ease travel and post-COVID increases in tourism. Tourists typically cause an increased demand for public transport, including taxis and buses, further exacerbating the need for locals to use private transport.
Songkran causes a spike in road traffic accidents (RTAs). During this period, the RTA rate approximately doubles in a country already experiencing very high rates. From 11 to 17 April 2024, there were at least 480 RTA fatalities and over 2,000 injuries, equating to approximately 69 fatalities per day. This puts Thailand temporarily in the top 10 most dangerous countries in the world for RTAs during the Songkran period.
The slight reduction in deaths this year is highly likely due to the impact of the 28 March earthquake, which occurred in Myanmar, also impacting Bangkok. In the lead up to Songkran, the Thai Hotels Association (THA) predicted that tourism revenue would fall by approximately 10-15 per cent, with tourists cancelling their trips. Motorcycles account for most of the deaths, which are generally attributed to driving while intoxicated, speeding, cutting lanes, wet road surfaces, and inadequate safety wear.
While celebrations are widespread, travellers can face penalties for involving unwilling participants. Splashing water on people not involved in the celebrations can be considered causing a nuisance or damaging property, leading to potential prison sentences of up to one month or a 10,000-baht (228 GBP) fine. During the 2024 celebrations, for example, three tourists from Hong Kong were jailed for 28 days after splashing a police officer with water. Similarly, dumping powder on unwilling participants, an act which typically involves non-consensual contact, could result in a public indecency charge.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Around 60,000 Afghans deported from Pakistan in two weeks
The figure was announced on 15 April by the International Organisation for Migration (IOM). Pakistan has pledged to deport the approximately 800,000 Afghan nationals who have Afghan Citizen Cards (ACC), as part of larger efforts to repatriate the millions of individuals who have entered the country following the Taliban’s takeover in 2021.
Humanitarian organisations have noted that transiting through the poorly policed areas near the Durand Line poses a significant threat to returning migrants, and there have been several cases of extortion and violence carried out by Pakistani security forces. Moreover, the threat of terrorism in the area remains extremely high, with several Islamist groups likely attempting to recruit disenfranchised Afghans for radicalisation and potential attacks.
Hong Kong’s largest pro-democracy party set to disband
On 13 April, the Hong Kong Democratic Party, Hong Kong’s last remaining major opposition party, conducted a meeting approving arrangements to disband. The decision came after pressure from Beijing, which has allegedly warned the party in recent months to disband or face potential arrest.
There is currently no precise date for the dissolution of the party, but a final vote will be held in the coming months. A majority of 75 per cent will be required to pass the motion. It is highly likely that the motion will pass, marking the end of political opposition in Hong Kong. Pro-democracy movements in Hong Kong have been largely curtailed since Beijing imposed the National Security Law in 2020, which triggered major protests across the region.
Security, Armed Conflict and Terror
Three police officers killed and 16 injured in Pakistan bombing attack
On 15 April, an improvised explosive device (IED) placed on a parked motorcycle detonated while a convoy carrying around 40 police officers transited past it in Mastung, Balochistan. The attack was claimed by the Islamic State Khorasan Province (ISKP) and marks the first notable attack conducted by ISKP in weeks and follows an unusual period of inactivity for the group, which is one of the Islamic State’s more active branches.
While it is difficult to definitively assess the cause of this decrease in attack volume, it is likely that it has been partly driven by an internal reshuffle of ISKP’s leadership and key roles, which was launched by the group’s leaders in February-March 2025.
The Maldives bans entry for Israeli passport-holders
On 14 April, the Maldives’ parliament passed an amendment to its immigration law, which was subsequently approved by President Mohamed Muizzu on 15 April. A Cabinet statement declared that ‘The ratification reflects the government’s firm stance in response to the continuing atrocities and ongoing acts of genocide committed by Israel against the Palestinian people.’
A similar ban was in place in the early 1990s but was rescinded in 2010 during renewed relations. Given the low Israeli visitor rates to the Maldives, with only 59 people with Israeli passports (out of a total 214,000 visitors) entering in February 2025, protests across the archipelago are unlikely.
However, there is a realistic possibility that small-scale protests will occur outside the Maldives’ embassies in other major cities, including London, following the decision.
Russia requests access to Indonesian air base
Australia has raised concerns in response to reports that Russia has requested permission to base Russian Aerospace Forces (VKS) aircraft at an Indonesian air base in Biak, in the remote Papua region. Australian Prime Minister Anthony Albanese has stated that he considers Russia an authoritarian regime and reiterated Australia’s support for Ukraine.
A Russian military presence in Papua would almost certainly enhance its surveillance of the region, placing its aircraft within 1,400km of Darwin, home to an Australian air force and naval base that regularly hosts US military assets.
However, Indonesia has consistently pursued a policy of “independent and active” foreign policy doctrine, engaging with multiple global powers while maintaining strategic neutrality, and has persistently refused to host foreign militaries on its soil regardless of alignment.
Myanmar’s junta chief Min Aung Hlaing visited Bangkok, Thailand for a rare summit visit
On 3 April, Myanmar’s junta chief Min Aung Hlaing visited Thailand for a regional summit for a joint statement on the earthquake. The leaders from the seven Bay of Bengal Initiative for Multi-Sectoral Technical and Economic Cooperation (BIMSTEC) members attended: Bangladesh, Bhutan, India, Myanmar, Nepal, Sri Lanka, and Thailand. The invitation of the junta leader marks a break from the regional policy of not inviting junta leaders to major events.
For the junta, the attendance at the summit is highly likely a symbolic act amid growing criticism regarding the Tatmadaw’s handling of the earthquake, having been accused of violating the ceasefire and blocking aid to rebel-held areas. Former Thai Prime Minister Thaksin Shinawatra and Malaysian Prime Minister Anwar Ibrahim reportedly pushed for a continuation of the ceasefire imposed from 2-22 April as a humanitarian pause to support post-earthquake relief efforts.
There is a realistic possibility that they will extend the ceasefire, given that the earthquake primarily damaged junta-controlled regions of Mandalay and preventing a rebel offensive is almost certainly beneficial to the junta. However, given China’s ongoing economic and diplomatic support for the junta and the disunity of regional powers regarding intervention, it is unlikely that the Tatmadaw would cave to international pressure regarding a formal peace process.
Environment, Health and Miscellaneous
Earthquake kills one in Tajikistan
The 6.4 magnitude tremor struck the Rasht district at a depth of 16 kilometres, destroying approximately 100 houses and killing one person in the village of Ushturpasta. Multiple aftershocks of between 3 and 5 magnitude also occurred in the area. Tremors were also recorded in Myanmar and India around the same time. All the affected locations are near the borders between the Indian and Eurasian plates. This area is undergoing a higher frequency of seismic activity, which included the 28 March 7.8 magnitude earthquake in Myanmar that killed more than 5,000.
New Zealand hit by Tropical Cyclone Tam
Tropical Cyclone Tam is impacting New Zealand’s North Island, particularly the Northland region, with significant disruptions. Flights at Whangārei Airport (WRE) were cancelled on 16 and 17 April. At Auckland Airport (AKL), some international flights have been delayed until 18 April.
Firefighters in Northland have so far responded to 120 weather-related calls on 17 April. State Highway 1 near Umawera has experienced flooding, and nearly 15,000 people remain without power in Northland. The New Zealand MetService has issued warnings for coastal flooding and erosion due to large waves, and a power outage is affecting several hundred residents in the Whangārei and Kaipara districts. Cyclone Tam is expected to weaken into a subtropical low but may re-intensify later in the week.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
Reports that the US is considering drone strikes on cartels in Mexico will likely strain bilateral relations and provoke retaliation from cartel groups if authorised.
The gangs’ occupation of Mirebalais, Haiti is likely to be a setback for the government and international forces. It will almost certainly give criminal groups more control over aid routes supplying Port-au-Prince.
Europe, Middle East & Africa (EMEA)
Protests in Spain, driven by rising living costs, are likely to continue over Easter and during this year’s high tourism season. While likely to be peaceful, there is a realistic possibility of isolated cases of harassment.
Russia is highly likely incentivised to launch its new spring offensive in northeastern Ukraine to gain further leverage to achieve its maximalist war goals, but its forces will likely struggle to successfully seize Sumy City.
Sustained Israeli strikes in Lebanon and reports that Iran is continuing to resupply Hezbollah through the Port of Beirut are likely to undermine the ceasefire agreement and increase the chances of renewed conflict.
The downing of a Malian drone in Algeria has precipitated a diplomatic crisis between the two countries. The incident likely showcases Algeria’s deteriorating position in the Sahel and vis-à-vis the junta states.
A return to civil war in Yemen, if unconfirmed reports of preparations for a ground offensive in Yemen are accurate, likely pose risks of renewed long-range strikes by the Houthis against Saudi Arabia and the UAE.
Al-Shabaab unlikely to imminently take control of Mogadishu, Somalia, but is likely to conduct more attacks in the capital amid significant territorial gains.
Asia-Pacific (APAC)
Multiple ceasefire violations in Myanmar almost certainly indicate that both sides are exploiting the aftermath of the earthquake to consolidate territory and advance under the cover of relief efforts.
North, Central and South America
US and Mexico: Trump administration considers drone strikes on cartels.
Reporting from current and former US officials indicates that the Trump administration is exploring the possibility of conducting drone strikes as part of a wider effort to counter narcotics trafficking on the US’ southern border. Proposals that include the White House, Pentagon and US intelligence agencies are in the early stages but have included the option of directly targeting Mexican cartel leaders in Mexico. Discussions have included the US conducting joint operations with Mexico as well as the potential for unilateral strikes.
Additional reporting indicates that the Central Intelligence Agency (CIA) is currently reviewing its authorities to use lethal force against Mexican cartels in Mexico and in other parts of the world. This has involved consultation with legal experts and operational planners to identify what operations the CIA could theoretically conduct and what would be the potential risks of those operations.
Solace Global Assessment:
Since coming to office, President Trump has made combating the illicit flow of narcotics, primarily fentanyl, into the US one his key objectives. Early moves have included the designation of several Mexican cartels as foreign terrorist organisations (FTOs), increased sanctions on cartels, and the deployment of advanced military intelligence, surveillance and reconnaissance (ISR) assets to the border and even over Mexican airspace. These actions have been further supported by the threat of imposing tariffs on Mexico if it does not take action against the cartels, forcing the Mexican government to increase arrests, extraditions, and seizures of cartel members and assets.
Reports suggest that the cartels are under unprecedented pressure and have been forced to adapt their operations as a result of pressure from Mexican operations, which have likely been supported by US intelligence. Advanced US ISR assets capable of signals intelligence (SIGINT) and imagery intelligence (IMINT) have likely afforded the US military and intelligence agencies with a comprehensive understanding of cartel operations, locations, networks and leadership. This has likely allowed the US to develop potential targets, should the use of direct action be sanctioned by the White House.
However, there are likely several factors limiting the US’ use of direct action against the cartels. Firstly, there is a realistic possibility that threats to conduct drone strikes and other forms of direct action are part of a gambit to exert increased pressure on Mexico to deal with the cartels independently. Secondly, while lethal force is theoretically permissible, the presence of a large number of US citizens in Mexico, some of whom are involved with the cartels, means the consequences of such actions could be far-reaching. Collateral damage, such as the accidental death of an American citizen, could create significant diplomatic and legal issues for both the CIA and the US government. Thirdly, using lethal force, especially unilaterally, would almost certainly strain relations with Mexico and could lead to a cessation of intelligence sharing with the US, a move that could ultimately weaken counter-cartel operations.
Most importantly, the use of direct action in any form could precipitate a major change in the security environment in Mexico that could threaten US interests, personnel and assets. The cartels may be forced to alter their tactics, which could involve more sophisticated counter-surveillance measures, more innovative ways to smuggle illicit goods into the US or an escalation in violence, both inside Mexico and potentially in the US. The targeting of cartels, especially leadership, is likely to lead to the fracturing of cartels and power vacuums, resulting in cartel infighting, territorial disputes and rival cartels attempting to exploit weaknesses.
In a worst-case scenario, the cartels may perceive increased US involvement as an existential threat to their operations and could respond with a range of retaliatory actions to deter further intervention. There is a realistic possibility that this could include increased cartel violence on the border, attacks on Mexican security services and assassinations of high-profile civilian targets such as politicians and journalists. A more extreme response could involve cartels deliberately targeting US interests in Mexico or beyond. This might include attacks on American businesses, kidnappings of US citizens or deliberate attempts to flood the US with higher volumes of narcotics and potentially more lethal varieties.
Haiti: Gangs take control of Mirebalais, north of Port-au-Prince.
After more than a week of fighting, gangs associated with the Viv Ansamn coalition have taken control of Mirebalais, north of Port-au-Prince. Gangs have subsequently launched an offensive toward Péligre, where a hydroelectric power plant is located, but have been contained by authorities. In Mirebalais and neighbouring Saut-d’Eau, at least 31,000 people have been displaced and more than 500 prisoners freed. Local sources have reported occasional cases of mob violence by local residents against suspected gang members. Moreover, the arbitrary killing of civilians by gangs has continued. Due to the attacks, the hospital in Mirebalais was forced to close and to evacuate all patients.
Solace Global Assessment:
Mirebalais is a strategic town located at the intersection of Route 305 and National Road 3, and controls part of the northern trade from the border to Port-au-Prince. It is also on the main route connecting the capital to Cap-Haïtien and, therefore, can be used to control or restrict aid flows to Port-au-Prince. This is especially the case due to the renewed gang attacks on Toussaint Louverture International Airport (PAP), which have rendered the airport non-operational and have therefore increased Cap-Haïtien’s importance as the main entry point into Haiti and aid distribution centre. After taking control of the town, the gangs have likely implemented their strategy meant to destroy all civil society and administrative institutions to force the population into a state of dependency. Measures in Mirebalais have included the forced “disappearance” of two journalists, as reported by the Association of Haitian Journalists (AJH), the forced closure of the hospital, and the killing of humanitarian workers, including at least two nuns. Finally, by occupying the town, the gangs are likely seeking to benefit from the smuggling of weapons and ammunition from the border with the Dominican Republic. Improving their position to the north of the capital will likely shape the conditions for a future attack on the remaining territory that the government forces and the Kenyan police mission maintain in Port-au-Prince.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
“Hands Off” protests in all 50 US states.
The protest movement opposes the Trump administration’s policies, particularly the cuts to government agencies being spearheaded by billionaire and government advisor Elon Musk. The “Hands Off” protests have been supported by multiple smaller organisations and movements, like the 50501 movements and other bodies adjacent to the Democratic Party. On 5 April, estimates of nationwide attendance reached three million across more than 1,000 locations. No notable violent incidents were recorded during the protests. The protests constitute the largest civil unrest instance since the beginning of the current administration. Organisers have called for a second large-scale demonstration on 19 April.
Large-scale mobilisation for Ecuador’s presidential elections.
Ecuador’s military is mobilising 1,800 reservists to provide extra security during the second round of presidential elections on 13 April, after the first round resulted in a tie. The reservists will be deployed to protect polling stations. The government has yet to announce what additional security measures will be in place. However, the first round resulted in temporary border closures with Colombia and Peru to limit the influence or organised crime, and curfews were imposed in 22 municipalities. There is a high likelihood of similar measures being introduced during the second round, with Ecuador currently struggling to contain a wave of violence attributed to transnational organised crime groups.
Peruvian transport workers strike over endemic crime.
On 10 April, major transport disruptions were recorded in Lima, Peru, after transport workers went on strike. Transport workers marched on Congress to demand action against a surge in crime in the country, with much of the crime involving the extorting of public transport. This has involved attacks on public transport networks after companies have refused to pay the extortion, resulting in high rates of civilian casualties. Much of the crime has been linked to well-financed and organised transnational criminal groups like Tren de Aragua. The government has recently declared a national emergency in the capital and has introduced emergency measures that will grant the Peruvian National Police greater powers to combat organised crime.
Indigenous groups stage multi-day protest in Brazilian capital.
An estimated 10,000 indigenous people from across Brazil have amassed in Brasília to advocate for land demarcation and to protest a 2023 law that limits their land rights and makes it more difficult for tribes to reclaim lands they were forced to abandon. The protests were organised from 7-11 April and have remained largely peaceful. However, on 10 April, Brazilian police used tear gas against the protestors after they approached government buildings in the capital. Observers have indicated that it is highly likely that indigenous groups will target the upcoming COP30 which is set to be held in the northern Brazilian city of Belem in November.No need to do anything with the section titles.
Security, Armed Conflict and Terror
Colombian dissidents agree to disarm.
A dissident faction of the National Liberation Army (ELN), the Comuneros del Sur, has agreed to demobilise and hand over its weapons as part of President Petro’s objective of securing total peace. While this will be viewed as a win for the incumbent administration, the Comuneros del Sur is only a minor rebel group with an estimated 100-300 fighters, dwarfed by the ELN, which is still fighting an insurgency in multiple parts of Colombia. The agreement will likely only be viewed as a symbolic win and is unlikely to have any significant security considerations for Colombia as a whole.
Environment, Health and Miscellaneous
Third measles death reported in Texas.
It is the third death to occur in the space of months, after ten years during which measles caused no fatalities in the US. Around 650 cases have been recorded so far this year, 500 of them in Texas, as part of an outbreak that likely started in local Mennonite communities, who have extremely low vaccination rates. Washington has deployed the Centers for Disease Control and Prevention (CDC) to assess possible responses to the multi-state outbreak. However, the CDC and the Department of Health, which is led by “vaccine-sceptic” R.F. Kennedy Jr., face severe challenges, including mass layoffs and trust issues among the most at-risk communities, which are likely to make response efforts more complex.
First confirmed human death from bird flu in Mexico.
Mexico has confirmed its first human death from H5N1 bird flu, as a 3-year-old girl in Coahuila, western Mexico, who died due to respiratory complications from the virus. The case marks the first known human infection in the country, though the exact source of transmission is still under investigation. The girl’s case follows a global trend of H5N1 infections, with the virus having spread among birds and a limited number of humans, particularly in the US, where 70 cases have been reported over the past year. The immediate threat to other humans is assessed as low, however, the authorities will almost certainly increase their surveillance and contact tracing to prevent further spread.
Roof collapse in Dominican Republic kills 221, injures hundreds.
On 8 April, the roof of the Jet Set nightclub in Santo Domingo collapsed during a performance. Search efforts to retrieve the bodies of the victims ended on 11 April. Authorities have launched an investigation to determine the causes of the collapse, which was one of the deadliest disasters in the Dominican Republic’s modern history. The investigation is highly likely to have high political visibility and, depending on the findings, could become a driver of civil unrest.
Europe, Middle East & Africa
Spain: Large-scale protests against cost of living crisis.
On 5 April, protests took place in around 40 Spanish cities, with residents calling for policies to reduce growing housing prices. In Madrid, the demonstration was attended by around 150,000 people. The protesters, who are supported by a network of civil society organisations and have increasingly received the support of mainstream left-wing parties like Podemos, made a series of demands including the lowering of rents, the banning of eviction practices, the end to the proliferation of short-term rental contracts aimed at tourists, and the seizing of empty apartments.
Solace Global Assessment:
Since the COVID-19 Pandemic, cities in Spain, particularly highly popular tourist destinations like Barcelona, Palma, or Málaga, have had double-digit increases in housing costs, effectively pricing out long-time residents. According to tenants’ unions, rents have on average increased by 18 per cent over the past two years. The first notable wave of protests related to this issue began in the Canary Islands in 2023 and rapidly expanded to the mainland. The housing protests are indissolubly linked with a growing anti-tourism sentiment, due to the increased number of properties being taken off the long-term rental market in favour of short-term, tourist-focused contracts. Past waves of protests in 2023 and 2024 have been especially intense during the high tourist season between May and September. Further protests will likely occur during the summer. Large-scale protests are also likely to occur on or near Easter, particularly in cities where Easter celebrations attract large numbers of tourists, such as Seville, Málaga, and Valladolid. While these protests are likely to remain peaceful, there is a realistic possibility of acts of vandalism or harassment against foreign travellers or their property.This is the paragraph.
Ukraine: Russian spring offensive in northeastern Ukraine intensifies.
In an interview published on 9 April, Ukraine’s Command-in-Chief Oleksandr Syrskyi stated that a new Russian spring offensive against the Sumy and Kharkiv Oblasts in northeastern Ukraine ‘has effectively already begun’. Syrskyi reported an ‘almost doubling’ of Russian offensive operations in the past week across multiple sectors on the Sumy and Kharkiv axes. Furthermore, Ukrainian President Volodymyr Zelensky stated that 67,000 Russian troops have amassed in preparation for an attack against Sumy City. The Russian Ministry of Defence claimed the capture of the Sumy village of Basivka over the weekend, which was disputed by the Ukrainian State Border Guard Service. Sumy City is only 30 kilometres from the Russian border and had a population of 256,000 in 2022.
Solace Global Assessment:
The intensification of Russian ground assaults in northeastern Ukraine is highly likely indicative of a newly launched strategic offensive, which Zelensky has previously indicated was initially planned to be conducted eight months ago but was delayed by the Ukrainian Kursk offensive. The approximately 60,000-70,000 Russian troops and national guardsmen (Rosgvardia) are primarily concentrated in Kursk Oblast, and are likely currently focused on ejecting the last remaining Ukrainian forces from positions south of Sudzha in the Kursk salient. These forces would likely only dedicate fully towards an offensive towards Sumy City once the Kursk salient has been fully recaptured, with the already ongoing offensive operations against nearby Basivka, for example, likely providing further pressure on Ukrainian forces in Kursk to withdraw. Russian forces will nonetheless likely require additional reinforcements and materiel to successfully seize Sumy City, which Moscow would likely find challenging due to the current significant demands on the Pokrovsk axis in the Donetsk Oblast.
With the senior Ukrainian official Pavlo Palisa reiterating Kyiv’s position on 10 April that an absolute red line for Ukraine in any peace talks would be the imposition of curbs to its military, the Kremlin is highly likely incentivised to launch a new offensive to gain further leverage in potential negotiations to achieve its maximalist war goals. Ukraine’s ability to repel the offensive would likely be significantly hampered by any further suspensions of US intelligence sharing, with Russian forces having made the most rapid advances in Kursk Oblast during the temporary pause in early March. Moscow will likely continue to leverage the limited and vaguely defined moratorium on long-range strikes against energy infrastructure to gain concessions, with a key goal of pressuring Washington to renew its withdrawal of military aid and intelligence sharing. The Russian Ministry of Defence, for example, stated on 9 April that Ukraine had violated the agreement with six attacks on Russian energy infrastructure over the past day. It is likely that Russian long-range and artillery strikes against the urban centres of Sumy and Kharkiv will continue to increase in the coming weeks, posing significant risks to civilians and foreign nationals deployed in the area.
Israel and Lebanon: Hezbollah exploiting maritime routes to rebuild.
Western security sources have indicated that Iranian Revolutionary Guards Corps (IRGC) Quds Force Units have been supplying Hezbollah with arms, equipment and money through maritime routes. The Quds Force Units reportedly involved in the smuggling, Units 190 and 700, are units known to be involved in the facilitation of lethal aid from Iran. The report suggests that Hezbollah maintains an established network of operatives at the Port of Beirut, enabling the organisation to smuggle weapons into the city without restriction. The Lebanese government has rejected the claim, asserting that the Port of Beirut has the same level of inspections and security as Beirut-Rafic Hariri International Airport.
Solace Global Assessment:
Since the collapse of the Assad regime in Syria and the banning of Iranian flights landing at Beirut-Rafic Hariri International Airport (effective February 2025), Hezbollah has effectively been isolated from its traditional ground lines of communication (GLOCs) and air lines of communication (ALOCs). As a result, Tehran has almost certainly prioritised the rearmament of its primary proxy force via sea lines of communication (SLOCs), with the Port of Beirut serving as the largest and most important port in Lebanon. Recent reporting also suggests that Hezbollah has restarted domestic weapons manufacturing in Lebanon, including the resumption of activity at an arms production facility concealed beneath residential buildings in Beirut, a site previously targeted by Israeli airstrikes in November 2024.
These reports contradict claims made by Hezbollah on 8 April that it is willing to disarm entirely if the Israel Defense Forces (IDF) withdraw from its positions on the five hills it currently holds in southern Lebanon and halts its strikes throughout the country. Moreover, the involvement of the Quds Force in the smuggling of arms into Lebanon likely indicates that the rearmament of Hezbollah has become a strategic priority for Iran. Iran is currently scheduled for talks with the US over the abandonment of its nuclear programme. If an agreement is achieved, moves to disarm Hezbollah would almost certainly be unacceptable for Tehran, with the proxy group serving as one of its main deterrents against Israel. This reality is almost certainly understood by key decision makers in Israel, which view Hezbollah’s military capability as an extension of Iranian influence on its northern border.
Israel is unlikely to agree to Hezbollah’s demands for a withdrawal from southern Lebanon, particularly in light of reports regarding renewed arms smuggling from Iran and Hezbollah’s resumption of weapon production. Israel has also demanded that it will not withdraw until the Lebanese Armed Forces (LAF) can fully secure southern Lebanon from Hezbollah, an objective the LAF is unlikely to achieve in the immediate future. To counter the threat of Hezbollah, Israel will likely maintain its positions in southern Lebanon and continue its strikes throughout the country, a course of action that could jeopardise the fragile ceasefire agreement.
Throughout April, the IDF has conducted multiple strikes in southern Lebanon, the Bekaa Valley and several strikes in Beirut against high-value targets within Hezbollah, including against a senior figure responsible for coordinating external attacks against Israel with Iran, strikes that are likely increasing the chances of Hezbollah attacks on Israel. There is a realistic possibility that the recent evidence of the Iranian sustainment of Hezbollah will result in Israel increasing its strikes within Beirut, including strikes on the Port of Beirut and weapon production facilities in the city to counter Hezbollah’s attempts to regroup.
Algeria and Mali: Tensions increase after Algeria shoots down Malian drone.
On 6 April, Malian authorities accused their Algerian counterparts of “exporting terrorism” after Algerian forces shot down a Malian drone which allegedly entered Algerian airspace. In response, Algiers announced a complete airspace closure with its southern neighbour, halting flights between the two countries. According to Malian authorities, the drone was shot down while still in Malian airspace, and as it was carrying out an operation against Azawad fighters present in the area. In addition to Mali, Alliance of Sahel States (AES) members Burkina Faso and Niger also recalled their ambassadors from Algeria over the diplomatic crisis.
Solace Global Assessment:
Mali is currently fighting multiple jihadist and independentist insurgent groups. Several Azawad independentist groups operate in the country’s north under the Strategic Framework for the Defense of the People of Azawad (CSP-DPA) and maintain ties with Jamaat Nusratul Islam wal-Muslimin (JNIM), a jihadist coalition of al-Qaeda-affiliated groups. Mali’s junta has deployed significant resources to root out CSP-DPA, including systems provided by its Russian allies. These have so far been unsuccessful, with the junta forces suffering several notable defeats. In July 2024, Azawad militants, later joined by JNIM fighters, ambushed a convoy of Malian forces and Wagner Group operatives in Tinzaouaten, killing over 80 while suffering small losses.
Algeria’s relations with Mali have significantly worsened following the latter’s January 2024 withdrawal from the 2015 Algiers Accords. Algiers is also highly likely sceptical of Russia’s involvement in the south. While Moscow is one of Algeria’s key allies, the deployment of Russian personnel under the Wagner Group (and later Africa Corps) banner has resulted in a series of atrocities against Tuareg civilians, which have likely increased local support for independentist Azawad groups. While these are mostly active south of the border, Algeria likely assesses that the insurgency has the potential to spill into its territory. Seeking to avoid a confrontation with Russia over Wagner’s destabilising impact, Algeria has so far maintained a balancing approach to diplomacy. However, the downing of the Malian drone likely demonstrates that Algiers is willing to adopt a more assertive approach towards Mali.
Yemen: Potential renewal of civil war poses threat of strikes against Saudi Arabia and UAE.
A CNN article published on 6 April stated that regional diplomatic sources briefed that preparations are underway by the Republic of Yemen Government (ROYG) for a ground offensive against the Houthis. The article indicates that the offensive ‘would be launched from the south and east, as well as along the coast’ and that it could involve ‘Saudi and US naval support in an attempt to retake the port of Hodeidah’. The potential ground offensive comes amidst an intensified US campaign of aerial strikes against Houthi-controlled Yemen since mid-March. On 8 April, the US Ambassador to Yemen, Steve Fagin, met with the leader of ROYG’s Presidential Leadership Council (PLC), President Rashad al-Alimi, to discuss ending the Houthi threat to maritime shipping. On 9 April, the Saudi Foreign Minister Prince Faisal bin Farhan met with the US Secretary of State Marco Rubio in the US and, according to an official statement, discussed eliminating the Houthi threat to the region.
Solace Global Assessment:
The Yemeni civil war, which was primarily fought between 2014-2022, has been essentially frozen, with a six-month UN-brokered ceasefire having officially lapsed in October 2022 but de facto having held since. The Saudi-led coalition that intervened, consisting of Saudi Arabia, the United Arab Emirates (UAE), Kuwait, Bahrain, Qatar, Egypt, Jordan, Morocco and Sudan, conducted over 25,000 airstrikes against the Houthis, the majority in Sanaa, and primarily using the Saudi military. The campaign, however, failed to dislodge the Houthis, and it is almost certain that airpower without comprehensive and capable ground support is insufficient to defeat the Houthis. Riyadh has highly likely been incentivised to avoid a return to war with the Houthis, with their previous intervention having accumulated high economic and diplomatic costs that likely pose a threat to the Saudi Vision 2030 government program to diversify the economy and make Saudi Arabia an inviting location for both investment and tourism.
Riyadh is likely reluctant to return to war, however, the Trump administration likely has a strategic priority to nullify the Houthi threat, an objective that highly likely could only be achieved with significant regional support and a ground offensive. It is likely that a ROYG ground offensive would be mainly conducted using UAE-backed Southern Transition Council (STC) forces, notably the Giants Brigades, with the formerly separatist STC likely controlling the most powerful forces in internationally recognised Yemen. A return to civil war, depending on the level of Saudi and Emirati involvement, could likewise see a return to Houthi long-range strikes against targets in Saudi Arabia and the UAE. In Saudi Arabia, the Houthis previously targeted Saudi Aramco and military facilities across the country, including in and around Riyadh. In the UAE, the Houthis targeted Abu Dhabi National Oil Company (ADNOC) targets, including the Mussafah facility in Abu Dhabi and ADNOC trucks outside Abu Dhabi International Airport (AUH), in addition to a new terminal under construction at AUH, and also targeted Al Dhafra airbase which hosts US forces in Abu Dhabi. A claimed Houthi attack against Dubai International Airport (DBX) was credibly disputed by a Bellingcat investigation.
Between 2015 and 2018, the Houthis conducted long-range attacks across the Arabian peninsula primarily with ballistic missiles, whereas between 2019 and 2022, Houthi attacks were primarily conducted with one-way attack uncrewed aerial vehicles (OWA-UAVs). While Houthi launch capabilities have likely been degraded by recent US and Israeli military action, it is highly likely that the Houthis have gained proficiency in the use of OWA-UAVs and other long-range weapon systems through their anti-shipping and anti-Israel campaign. Saudi and Emirati air defence is proficient, with Saudi Arabia having addressed their likely previous vulnerability to ballistic missiles with the addition of Terminal High Altitude Area Defense (THAAD) systems. Nonetheless, a return to regular long-range Houthi strikes against the Gulf states would likely cause significant air travel disruption with airport and airspace closures, and even successful interceptions can pose risks due to the danger of debris.
Somalia: Al-Shabaab make significant territorial gains, threatening Mogadishu.This is the title.
In the past week, al-Shabaab seized control of the Afgoye-Mogadishu and Mogadishu-Balcad corridors, tightening control on the outskirts of Mogadishu. The group has also escalated bombing campaigns in recent weeks. On 5 April, mortar rounds landed near the presidential palace in Mogadishu, injuring several people. The following day, al-Shabaab launched mortar strikes, which landed near the airport and near Halane military base, wounding two civilians and triggering flight cancellations from Turkish Airlines. At least six mortar rounds reportedly landed inside the airport compound. Meanwhile, clashes are ongoing across multiple frontlines in the Middle Shabelle region, where a major al-Shabaab offensive has been ongoing since 2025. The government has confirmed it has taken control of Adan Yabaal and a village in Adale. In response to al-Shabaab’s strategic gains, President Hassan Sheikh Mohamud proposed a platform to unite the fractured national government institutions, regional states, and opposition parties.
Solace Global Assessment:
The ongoing al-Shabaab offensive is capitalising on stretched government resources, with the Somali Armed Forces spread between combating al-Shabaab and Islamic State Somalia (ISS) insurgencies, weaknesses in the African Union Support and Stabilization Mission in Somalia (AUSSOM), and Houthi support for the group. Since February, attacks have reportedly increased by approximately 50 per cent compared to its 2024 average, with al-Shabaab recapturing several areas of the Middle Shabelle region. AUSSOM has, so far, been relatively ineffective and marred by funding shortages and internal disagreements, with Burundi recently withdrawing from the mission.
Given the weakness of Somalia’s armed forces, Mogadishu is heavily reliant on external support. The US has ramped up air support, with President Donald Trump relaxing the rules of engagement for field commanders, enabling air campaigns against al-Shabaab in the Middle Shabelle region, as well as ISS in Puntland. Turkey, meanwhile, has agreed to provide additional military aid, equipment, intelligence sharing, and the deployment of approximately 5,000 personnel from the President Recep Tayyip Erdoğan-aligned private military company SADAT. Turkey’s support is likely crucial for ensuring the survival of Somalia’s government, with its largest overseas base being in Mogadishu. Continued government survival is of significant interest to Turkey. Turkish companies manage critical infrastructure in Somalia, including Mogadishu’s port and airport, and Erdogan has emerged as an influential mediator in regional disputes in the Horn of Africa and a key security partner to Mogadishu.
The loss of the Afgoye-Mogadishu and Mogadishu-Balcad corridors will highly likely precipitate intensified attacks in central Mogadishu, with al-Shabaab likely having more chances to smuggle explosives into the capital. Furthermore, the Mogadishu-Balcad corridor connects Mogadishu to Middle Shabelle, which will highly likely weaken government efforts to counter the ongoing al-Shabaab offensive in the region. The capture of the corridors will also highly likely reduce trade and commerce in the region, driving up consumer costs and increasing pressure on the government. While an imminent complete capture of Mogadishu is unlikely due to the continued international support to the government, it will almost certainly further exacerbate the security situation by weakening government counteroffensive measures and easing al-Shabaab’s access to the capital.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Nationwide strike scheduled in Belgium throughout April.
Nationwide strikes have been organised throughout April in response to the federal government’s plans to cut social spending to reduce the federal budget. Following a 7 April nationwide strike, further strikes have been organised throughout the month, with several key sectors involved. Five railway trade unions are planning four 24-hour strike actions every Tuesday in April (8, 15, 22, and 29 April). A planned national strike on 29 April will likely result in major disruptions to public transport and other public services across the country, with previous strikes leading to the suspension of services at both of Brussels’ international airports.
Germany’s Christian Democrats and Social Democrats agree on coalition deal.
The so-called “grand coalition” between the Christian Democrat sister parties (CDU-CSU) and the Social Democrats (SPD) was the obvious outcome of the last elections, guaranteeing the survival of Germany’s cordon sanitaire against the far-right Alternative for Germany (AfD), now the second force in parliament. The CDU-led government will likely remain fragile. Chancellor Friedrich Merz has promised his voters harsher measures on migration, also intending to keep the AfD at bay. However, the implementation of these policies, such as turning away asylum seekers at Germany’s borders, may indirectly put pressure on the SPD, whose electorate remains opposes Merz on migration, threatening the coalition. Moreover, the new government, whose members recently agreed on revising Germany’s “debt brake” to increase defence spending, will likely have to confront a more pessimistic economic outlook resulting from the trade war with the US.
Large-scale protests in Rome against European rearmament.
Around 80,000 people gathered in the Italian capital on 5 April, under the lead of the populist 5 Star Movement (M5S) and some left-wing parties. The demonstrations opposed the Meloni government’s support for ReArm Europe, the EU’s military development and procurement plan aimed at reducing reliance on Washington. M5S, which, although founded as a big-tent party, has increasingly established itself as a populist left-wing alternative to the “establishment” Democratic Party (PD), is likely seeking to capitalise on the Italian electorate’s relatively high levels of scepticism towards Brussels’ support for Kyiv.
Thousands rally in Central African Republic (CAR).
On 4 April, thousands of protesters gathered in Bangui to peacefully protest the Wagner-backed President Faustin Archange Touadera’s plans to run for a third term in a rare demonstration of public anger. Demonstrations were organised by opposition parties who reject Touadera’s plans for a third term and come amid worsening living conditions and reports of Wagner’s extrajudicial killings, sexual violence, and looting by Wagner forces. Demonstrators signalled their anger at the governance of Touadera and his Wagner backers, calling for the protection of CAR’s sovereignty and for Touadera, and by extension Wagner, to be removed from power. The CAR was the first African country where Wagner established operations, helping the government prevent rebels from taking control of Bangui in 2021, propping up Touadera under the guise of protecting state sovereignty. The growing protest movement reflects an increasing loss of legitimacy for Touadera, who is perceived as dependent on Wagner to hold power, as well as a broader resistance to perceived foreign occupation. While the protest movement is likely to grow, Touadera will highly likely prioritise regime survival and use security forces to crack down on demonstrations with force.
Detained South Sudanese vice president ousted by his party.
On 9 April, Sudan People’s Liberation Movement-In-Opposition (SPLM-IO) members voted to replace Riek Machar as head of the party with peacebuilding minister Stephen Par Kuol as interim chair until Machar is released. Machar loyalists did not attend the meeting, with some having fled the country. The decision comes approximately two weeks after Machar was arrested following violence conducted by the Machar-linked White Army in Nasir, Upper Nile state. The arrest, triggered by criticism of the presence of Ugandan troops in South Sudan, has threatened to plunge the country back into civil war by violating the 2018 peace agreement, which stipulated power-sharing terms between the two sides. Despite Kuol’s reaffirmation of the peace commitments, replacing Machar with Kuol risks undermining the peace agreement by fragmenting the SPLM-IO and weakening its role in the unity government, undermining the division of power stipulated by the agreement’s terms.
Tanzanian opposition leader arrested.
On 9 April, Tanzanian opposition leader Tundu Lissu, chairman of the CHADEMA party and a prominent critic of the government, was arrested after a rally in Ruvuma in the south of the country. Lissu has been charged with treason, a capital offence, over allegedly making remarks inciting rebellion and disruption ahead of the 2025 general elections. The charges have been dismissed by the opposition as politically motivated and meant to eliminate Lissu, who had been the runner-up in the 2020 presidential election. The arrest has also drawn widespread international and domestic criticism of President Samia Suluhu Hassan’s human rights record after a series of arrests, abductions and the targeting of opposition figures. There is a realistic possibility that the arrest of Lissu will incite widespread and potentially violent unrest in Tanzania.
Security, Armed Conflict and Terror
Three arrested for planning attack in Dunkirk, France, on behalf of the Islamic State (IS).
French authorities discovered attack plans and, reportedly, an “explosive vest”. This likely makes the recent plot more sophisticated than other “lone wolf” attack plans and could imply that the suspects had some outside direction. Dunkirk is a high-visibility location due to its political relevance on both sides of the Channel, being both a tourist destination and one of the key transit points for migrants seeking to make the crossing to the United Kingdom.
Libyan authorities tell ten aid groups to stop operations helping migrants.
Authorities claim that the groups violate local law and commit “a hostile activity targeting the Libyan demographics” by helping migrants from Sub-Saharan Africa settle in Libya. The vast majority of migrants entering Libya and neighbouring Tunisia do so with the aim of crossing the Mediterranean. However, since the refugee crisis of 2015, the influx of migrants, who often remain for months or years in local towns prior to making the crossing, has driven a considerable increase in anti-migrant sentiment. The ban is likely to result in a worsening of the already poor humanitarian conditions of the migrants in Libya. Aid organisations provide migrants with essential goods and services like food, clothing, housing, and medical care. Without them, there is a realistic possibility of migrants being forced to rely more frequently on local criminal groups, exposing them to a significantly greater threat of violence and abuse, including enslavement.
Reports indicate Boko Haram is gaining ground in northern Nigeria.
The governor of Nigeria’s Borno State, Babagana Zulum, has warned that the jihadist group Boko Haram is staging a comeback. The comments were made after Boko Haram recently staged a series of attacks and seized control of some parts of the north-eastern state. Attacks have targeted Nigerian army bases and police stations, not just the civilian population. Moreover, some operations reportedly involved cooperation with the Islamic State’s West Africa Province (ISWAP). The central government has downplayed the situation, claiming that security in the region has improved. However, the central government has diverted military resources to the northwest of the country to deal with endemic banditry and the emergence of a new jihadist group linked to Niger, the Lakurawa, a move that has likely overstretched government forces and provided Boko Haram with greater freedom of movement.
Environment, Health and Miscellaneous
Severe flooding in Kinshasa, DRC, kills dozens.
At least 33 people have died in the capital of the Democratic Republic of the Congo (DRC) after days of heavy rains resulted in widespread flooding. The rains caused the Ndjili River to overflow, posing a particularly severe risk to the informal settlements located near its banks. The floods also temporarily blocked access to the airport, and to severely impacted parts of the city, complicating search and rescue efforts. Responses to the flooding are likely to be complicated by the ongoing conflict in the eastern DRC, which has both stretched Kinshasa’s resources and prompted the evacuation of international personnel, including some humanitarian workers, from the country.
Asia–Pacific
Myanmar: Fighting continues despite post-earthquake ceasefires.
After a 7.7-magnitude earthquake struck Myanmar on 28 March, the National Unity Government (NUG) and the Three Brotherhood Alliance, representing ethnic resistance groups across the country, announced a temporary ceasefire of one month beginning on 1 April. Under the unilaterally declared ceasefire, the rebel groups agreed not to initiate any offensive operations and would only engage in self-defence. After initial attempts to resist a ceasefire, Myanmar’s State Administration Council announced that it would observe one from 2 April to 22 April. However, multiple international observers, including the UN, have reported widespread ceasefire violations conducted on both sides. The NUG, a shadow government formed after the coup, has accused the junta military of conducting over 60 airstrikes and artillery barrages since the earthquake, resulting in the deaths of at least 68 civilians. Recent estimates indicate that over 3,000 people have now died, with the toll expected to rise significantly as the rubble is cleared. Hospitals are reportedly overwhelmed, and shortages of medical supplies, fuel, clean water and shelter are hampering relief operations.
Solace Global Assessment:
The junta government has a precedent of exploiting ceasefires to contain ethnic rebel groups under the guise of tentative truces. The junta has likely only agreed to a temporary ceasefire publicly to improve both its international and domestic image, with elections planned in late 2025 or early 2026. Reports on the ground even suggest that the junta is actively obstructing relief efforts while expanding operations in earthquake-affected areas. This has reportedly included the hindering of access to aid organisations, the blocking of aid and the seizure of supplies, combined with a continuation of air and artillery strikes.
After months of rebel advances, it is unlikely that the junta will cease offensive operations, likely fearing that the rebel groups will also exploit the ceasefire to regroup and continue their advance. Part of the junta’s strategy is likely to restrict the delivery of aid to areas under rebel control, thus restricting the rebel groups’ access to vital supplies such as water, food, medicine and other equipment, especially near the current lines of engagement.
However, with international aid organisations operating near earthquake-affected areas, there is likely more coverage of junta operations on the ground. As a result, the junta may adapt its strategy by increasing the use of airstrikes, targeting rebel-held or strategically significant areas further behind the front lines, such as Kachin State, Shan, and Kayin (Karen) States, which remains a key stronghold for the resistance forces and are critical to rebel supply chains and operations. High-value targets for the junta are likely to include rebel leadership, force concentration, ammo depots and other military targets. However, reports have also indicated that aid convoys have been targeted, as well as critical infrastructure like roads and bridges that sustain rebel operations and facilitate the delivery of humanitarian aid.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
South Korean election scheduled for 3 June.
On 7 April, South Korea’s cabinet voted to confirm a 3 June election date. The decision follows former President Yoon Suk Yeol’s impeachment and removal from office following his declaration of martial law on 3 December. In the 2022 election, Yoon had beaten opposition liberal Democratic Party Lee Jae-myung by a narrow margin, making him the frontrunner in the upcoming election. However, Lee faces legal challenges due to multiple charges, including violating election law and bribery. Kim Moon-soo will likely lead the incumbent conservative People Power party. A 4 April Gallup poll had 34 per cent of respondents supporting Lee and nine per cent backing Kim.
Garment workers’ protest in Bangladesh results in more than 50 injuries.
The clashes, which lasted for at least three hours, erupted in Rupganj, near Dhaka, outside a local manufacturing plant. According to local media, at least 120 workers, who had been reportedly fired prior to Eid, had been demonstrating in front of the plant for two days prior to the intervention of authorities. In addition to 50 injuries, at least ten workers have been arrested. Further protests regarding labour disputes during Eid have occurred in other parts of Bangladesh, with the garment industry a particularly notable hotspot for unrest.
US academic charged under lèse-majesté laws in Thailand.
The US State Department has expressed its alarm after an American academic, Dr. Paul Chambers, was charged under Thailand’s strict lèse-majesté laws. The laws, aimed at suppressing defamation of Thailand’s monarchy, can carry sentences of up to 15 years and are often used to suppress the opposition. Dr. Chambers, a lecturer at Naresuan University in central Thailand, was reportedly arrested due to his research on the political relationship between Thailand’s monarchy and military. The arrest of a foreigner under lèse-majesté laws is relatively rare, however, Dr. Chambers was likely viewed as an important target by ultra-loyalist groups, who have targeted him with disinformation and online hate campaigns in the past.
Security, Armed Conflict and Terror
Deportations of Afghans from Pakistan underway.
At least 1,600 Afghans had been deported from Punjab and Sindh by the beginning of the week, and authorities have reportedly detained 5,000 for repatriation. In total, around 9,000 people have been deported from Pakistan since 1 April, and an unspecified number have crossed the border spontaneously. A majority of them have Afghan Citizen Cards (ACCs), while a minority reportedly have no identifying documents. Taliban authorities have reacted negatively to the deportations, accusing Islamabad of mistreating its Afghan residents and using them for “political goals”. The deportations are likely to increase tensions between Pakistan and Afghanistan. There is a realistic possibility that the worsening security environment will drive terrorism in Pakistan. In Afghanistan, extremist groups like the Islamic State Khorasan Province (ISKP), which is particularly active in the country’s southeast, may seek to target returning Afghans to destabilise the Taliban government.
Mob violence in Bangladesh continues to rise.
The Daily Star, Bangladesh’s most circulated English-language newspaper, reported that, between February and March, cases of mob violence, including killings, have doubled across the country. This follows a widespread increase in insecurity and crime, particularly violent crime, that has accelerated since the August 2024 ousting of Sheikh Hasina. Recent notable cases of mob violence include an attack on the properties of Awami League (AL) party members in Sylhet, and vandalism of American-owned businesses in Chittagong during a pro-Palestine demonstration. While mob violence – and “bulldozer justice” – are long-standing issues in Bangladesh, the fall of Hasina’s Awami League has almost certainly created a security vacuum. Police forces, which were previously staffed by Hasina loyalists and dependent on AL support, are now at the centre of an often violent, political competition led by the remaining major parties, who seek to govern post-Hasina Bangladesh.
China conducts naval drills at Cambodian naval base.
On 6 April, the People’s Liberation Army Navy (PLAN) conducted naval drills outside of the recently enlarged naval base at Ream, Cambodia, in the Gulf of Thailand. China’s presence in the Gulf of Thailand has raised concerns that the PLAN is establishing a permanent footprint to the south of the South China Sea and will lead to a major increase in Chinese naval and coast guard activity in the contested waters, likely increasing the chances of escalation. Cambodia has repeatedly denied reports that it has agreed to a clandestine deal with China to station its forces at the base, reiterating its stance that it is open to hosting military vessels from other countries.
Environment, Health and Miscellaneous
Eruption at volcano in central Philippines leads to school closures and NOTAM.
On 8 April, the Kanlaon volcano on the island of Negros in central Philippines erupted, leading to a 4,000 metre high ash plume drifting southwest. A level three out of five alert issued by the Philippine Institute of Volcanology and Seismology (Phivolcs), which indicates a high level of volcanic unrest, has been in effect for Mount Kanlaon since another eruption in December 2024. The level three alert recommends all residents within a six-kilometre radius of the volcano to evacuate, with the evacuations having previously taken place in December, which almost certainly reduced the immediate danger of possible casualties. Philippine authorities reported that approximately 48,000 people were impacted by the 8 April eruption. Several precautionary measures have been implemented, including the suspension of schools in four districts west of the volcano in Negros Occidental, and the issuance of a Notice to Airmen (NOTAM) by the Philippines Civil Aviation Authority for flights near Kanlaon volcano.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Increased Risks Expected During Passover Celebrations
Intelligence cut-off: 13:00 GMT 07 April 2025
Passover, or Pesach, is one of the major holidays of the Jewish religious calendar, as it marks the Exodus of the Israelites from Egypt described in the Torah. In 2025, the holiday begins on the evening of 12 April and ends on 20 April.
Passover occurs against a backdrop of sharply rising global antisemitic incidents, which have escalated significantly following Hamas’s 7 October 2023 attack in southern Israel and Israel’s subsequent invasion of Gaza. The holiday also falls during renewed hostilities in Gaza, which reignited after the collapse of the ceasefire between Israel and Hamas in March 2025.
Over the past 18 months, there have been numerous cases of attacks targeting Jewish people and places of worship, as well as any entities associated with Israel. Many of these incidents have occurred on dates of particular significance to Jewish and Israeli communities. They have included religious observances, such as the firebombing of a Melbourne synagogue during Hanukkah; historical commemorations, such as the lone wolf attack on the Israeli consulate in Munich on the 2024 anniversary of the 1972 Olympics massacre; and events linked to Israeli entities, such as the Amsterdam riots on the day of a Europa League football match involving an Israeli team.
On 1 April, Israeli authorities stated that they had thwarted a joint terror attack plot involving Hezbollah, Hamas, and Iran. The alleged plan was to target Israelis abroad or the wider Jewish community in response to the resumption of hostilities in Gaza.
Timeline of Global Security Incidents Since October 7 2023
INTELLIGENCE ANALYSIS
Lone Actor and Organised Group Attacks Possible Around Passover
There is a realistic possibility of terror attacks on or near Passover. Lone wolves, particularly espousing radical Islamist or far-right ideologies, are likely to target Jewish places of worship or community centres. Places of interest associated with Jewish history, such as Holocaust memorials and museums, are also likely targets due to their high traffic and visibility. Attackers may target Israeli consulates and embassies, although the risk here is lower due to their enhanced security presence. Attacks on Jewish interests may not be confined solely to Israel and major Western cities, as evidenced by previous attacks or plots targeting Jewish communities in South America and East Asia.
In addition, organised terror groups may seek to stage attacks during or near the holiday. Groups like Hamas and Palestinian Islamic Jihad likely retain the ability to stage attacks in Israel and the West Bank, particularly targeting security personnel and Israeli civilians. Moreover, the Islamic State (IS) and its network of global affiliates have intensified efforts to stage external attacks over the past two years and may seek to capitalise on the high visibility of the religious holiday to stage a high-impact and symbolic attack.
There is also an elevated threat of civil unrest around Passover, particularly in cities with a history of Gaza-related protests. While most demonstrations are likely to be peaceful, isolated incidents of vandalism or direct action against businesses, diplomatic sites, or religious buildings linked to either side of the conflict remain possible. In 2024, Jewish anti-war protestors staged a demonstration in New York, demanding that the US cease military aid to Israel.
Travel Risk Advice: Safety Guidelines for High-Risk Events and Holidays
- Closely monitor local news reports and government alerts.
- Avoid all large gatherings, including, if possible, large celebrations in public spaces.
- Consider alternative transport routes. Avoid public transport.
- If attending an event, identify exit routes and safe points. Identify if and which authorities are present in the area.
- Maintain regular communication with management or other safe contacts. Establish clear communication protocols ahead of travel.
- Monitor alerts and updates on Solace Secure.
- Adhere to all instructions issued by authorities.
- Have local emergency numbers and other key contacts available and saved on your personal devices.
- When attending events, always carry personal identification documents with you.
Subscribe to free weekly intelligence