Evacuations from Israel and High-Risk Locations Call +44 (0)1202 308810 or Contact Us →
Overview: Active Exploitation of PAN-OS Vulnerability
Risk Factor: Critical
Date: 19th February 2025
Vulnerability: CVE-2025-0108
Get Help Now
Solace Cyber are specialists in securing network infrastructure. Get in touch if you need support.
What We Know
The Cybersecurity and Infrastructure Security Agency (CISA) and Palo Alto Networks have confirmed that CVE-2025-0108 is being actively exploited in the wild, making it a high-priority security concern for organisations using PAN Alto firewalls. Security researchers have observed that attackers are not exploiting CVE-2025-0108 in isolation, but instead, they are chaining this vulnerability with two others: CVE-2024-9474 and CVE-2025-0111, to escalate their privileges and achieve a complete system compromise.When combined, these vulnerabilities can grant attackers full root access to the firewall, leading to severe security breaches.
Recommend Actions
- Immediate Patching: Update your PAN-OS to the latest versions to address CVE-2025-0108 and related vulnerabilities.
- Restrict Management Interface Access: Limit access to the management web interface to trusted internal IP addresses only.
- Implement a Jump Box: Enhance security by using a jump box, ensuring that only authorised systems can access the management interface.
Solace Cyber is available to assist organisations with patching, hardening, and securing their firewall infrastructure against these threats.
Need Help?
Solace Cyber are specialists in securing network infrastructure. Get in touch if you need support.
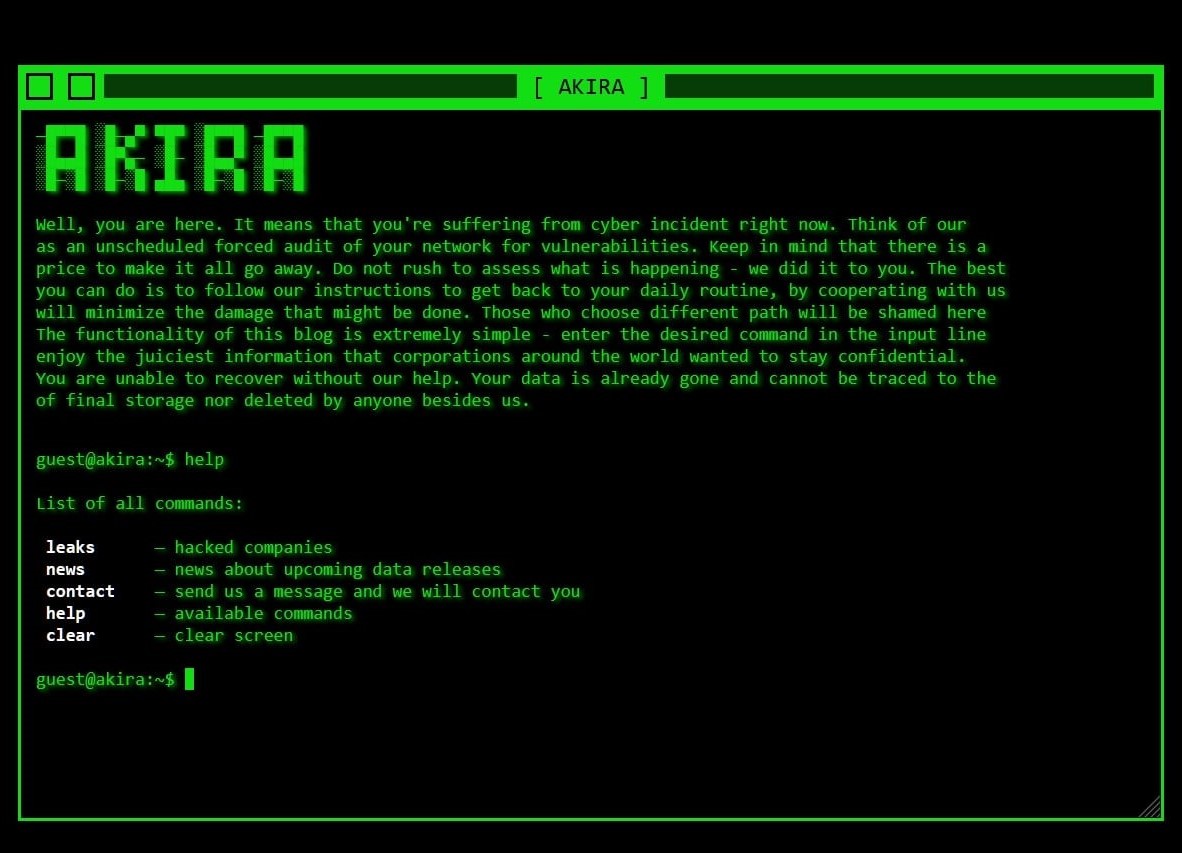
Overview: Akira Ransomware Group Exploiting SonicWall SSLVPN for Initial Access
Risk Factor: Critical
Date: 30th August 2024
Get Help Now
Solace Cyber are specialists in securing perimeter defences. Get in touch if you need support.
What We Know
In recent weeks, new intelligence from our incident response cases has revealed that the Akira ransomware group has started targeting SonicWall SSLVPNs to gain initial access to networks.
This tactic involves exploiting accounts with weak passwords and without Multi-Factor Authentication (MFA). This marks a significant shift in Akira’s initial access methods, which previously focused primarily on Cisco ASA firewalls.
While the possibility of exploiting SonicWall devices through known or unknown vulnerabilities cannot be entirely dismissed, multiple external sources are also reporting the group’s use of SonicWall SSLVPNs for initial access.
This change in Akira’s tactics highlights the critical importance of securing perimeter defences by enforcing strong password policies, regularly patching SonicWall devices, and implementing MFA across all VPN accounts to prevent unauthorised access to internal networks.
Solace Cyber Recommend:
- To ensure all user accounts with SSLVPN permissions, including any local accounts, are secured with multi-factor authentication.
- To conduct a recent audit of all VPN users and groups.
- Implement a strong password policy.
- Keep the SonicWall appliance updated with the latest patches and regularly review SonicWall releases for further patches.
- Enable external audit logging to extend the period of auditability, as SonicWall VPN login events typically do not cover more than 24 hours without external auditing.
Need Help?
Solace Cyber are specialists in securing perimeter defences. Get in touch if you need support.
Overview: Palo Alto has announced a critical zero-day vulnerability that is actively being used in the wild.
Threat Name: CVE-2024-3400
Risk Factor: Critical
Date: April 2024
Get Help Now
Solace Cyber security specialists can assist with updating your firewall to the latest version.
What We Know
CVE-2024-3400 represents a critical command injection vulnerability impacting the GlobalProtect Gateway functionality within PAN-OS. This flaw could be exploited by a remote, unauthenticated attacker to execute arbitrary code on a targeted firewall, granting them root privileges. The vulnerability has been categorised as critical as it poses a significant risk.
What Has Palo Alto Said?
Palo Alto Networks has acknowledged the issue and is working on a patch for CVE-2024-3400. Fixes are starting to become available. Not all versions of PAN-OS have a patch yet, so the advisory is to keep an eye on the Palo Alto Network official site.
Palo Alto Networks has also acknowledged that it’s “aware of a limited number of attacks that leverage the exploitation of this vulnerability.”
According to Palo Alto, the issue applies only to firewalls that have the configurations for both GlobalProtect gateway (Network > GlobalProtect > Gateways) and device telemetry (Device > Setup > Telemetry) enabled.
Recommendations For Navigating The Vulnerability.
When a vulnerability is identified, it’s crucial to take swift action to mitigate any potential risks. Specifically, for PAN-OS versions prior to:
- PAN-OS less than 11.1.2-h3
- PAN-OS less than 11.0.4-h1
- PAN-OS less than 10.2.9-h1
It’s highly recommended to prioritise patching as soon as the updates are released. These patches are vital for bolstering the security of your systems and safeguarding against potential exploitation.
As an interim measure, disabling device telemetry can serve as a temporary workaround until an official patch is made available. This step can help minimise exposure to vulnerabilities while awaiting the official fix.
Remaining vigilant is key. Continuously monitor official communications from Palo Alto Networks for any updates regarding the vulnerability and subsequent patches or mitigations. As soon as updates are released, promptly apply them to your systems to ensure optimal security posture.
It’s imperative to update your firewall to the latest version at the earliest opportunity. Solace Cyber stands ready to assist with this process, ensuring your firewall is promptly updated to the most recent version, thereby fortifying your defenses against potential threats.
Need support?
Solace Cyber security specialists can assist with updating your firewall to the latest version
Overview: Fortinet Warns of Critical FortiOS SSL VPN Flaw Likely Under Active Exploitation. Immediate action required.
Threat Name: CVE-2023-20198
Risk Factor: Critical
Date: 9th Feb 2024
Get Help Now
Solace Cyber security specialists can assist with updating your firewall to the latest version.
What We Know
On February 8, 2023, Fortinet issued a notice addressing a potentially exploited vulnerability in the wild. This vulnerability, found in the SSL VPN component, is classified as a pre-authentication vulnerability, with a critical severity rating of 9.6 CVSSv3. The identified flaw could enable a remote attacker to authenticate remotely by employing carefully crafted HTTP requests. Subsequently, the attacker may execute arbitrary code or commands, as reported by Fortinet.
What Has Fortinet Said About The Vulnerability?
Fortinet has emphasised that the only viable solution is to disable the SSL VPN entirely; opting to deactivate webmode is not considered a valid workaround. Urgent action is advised to promptly patch this vulnerability.
The affected versions and recommended solutions for FortiOS are as follows:
- FortiOS 7.6 is not affected, and no action is required (Not Applicable).
- FortiOS 7.4 versions ranging from 7.4.0 through 7.4.2, users are advised to upgrade to version 7.4.3 or above.
- FortiOS 7.2 with versions between 7.2.0 and 7.2.6, it is recommended to upgrade to 7.2.7 or above.
- FortiOS 7.0 users with versions from 7.0.0 through 7.0.13 should upgrade to 7.0.14 or above.
- FortiOS 6.4, versions 6.4.0 through 6.4.14, an upgrade to version 6.4.15 or above is recommended.
- FortiOS 6.2 users with versions ranging from 6.2.0 through 6.2.15 are advised to upgrade to 6.2.16 or above.
- FortiOS 6.0 in all versions, it is recommended to migrate to a fixed release.
What’s The Impact and Implementation Plan?
The flaw allows an attacker to remotely authenticate using crafted HTTPS requests. According to vuldb.com, technical details are unknown, but an exploit is available.
Swiftly upgrade your firewall to the most recent update. Solace Cyber is available to help you with the process of updating your firewall to the latest version.
Need support?
Solace Cyber security specialists can assist with updating your firewall to the latest version
Solace Cyber Recognised as Assured Service Provider by National Cyber Security Centre.

Solace Cyber, a leading Cyber Security organisation with headquarters in Dorset, has achieved recognition as an Assured Service Provider under the prestigious Cyber Incident Response (Level 2) scheme by the National Cyber Security Centre (NCSC). This accolade positions Solace Cyber among the first in the UK to attain Incident Response accreditation through the scheme, highlighting their commitment to providing high-quality incident response services.
The NCSC’s Cyber Incident Response project aims to offer support to UK organisations that have fallen victim to cyber-attacks, by raising awareness of high-quality incident response providers who can offer external support and advice on how to manage and recover from cyber incidents.
The initiative builds on the Level 1 scheme, which was developed to assure companies that have the capability to provide incident response services to nationally significant organisations such as regulated industries, central government, and critical national infrastructure.

With an impressive track record, Solace Cyber has been instrumental in helping companies across the UK recover from ransomware attacks and data breaches. Serving as representatives for International Loss Adjusters and Cyber Insurance companies, Solace covers more than 30,000 commercial businesses nationwide, through our channels, providing hundreds of successful response recoveries.
Rowland Johnson, President of CREST said, “Congratulations to Solace for gaining NCSC Cyber Incident Response (Level 2) scheme Assured Service Provider status for its incident response services. This means Solace has been assessed as capable of supporting most organisations with common cyberattacks, such as ransomware. It provides valuable assurance to buyers of the high quality of Solace’s incident response services.”
This prestigious accreditation reaffirms Solace Cyber’s dedication to meeting the NCSC’s stringent standards for both technical and organisational capability. By achieving the Cyber Incident Response (Level 2) status, Solace Cyber continues to demonstrate its unwavering commitment to enhancing the cybersecurity landscape and providing unparalleled support to organisations facing the challenges of cyber threats.
For media inquiries, please contact: rbessant@solaceglobal.com
Incident Response Services
Complete a cyber risk assessment
We will test your security posture against the latest cyber threats.

Request your incident response plan
You will receive a comprehensive report detailing the current IT cyber security posture of your estate as well as ongoing access to the Cyber Security Incident Response Team and the Realtime Risk Platform.

Access to Real-time Risk Platform
A comprehensive platform to consolidate all your cyber risk management.
Cloud XDR
Spot malicious activity and respond quickly, before material damage is done to your business.

Managed Detection & Response
Mitigate cyber risk for all endpoints and servers with these critical components; advanced machine learning and AI.

Navigating the Crossroads: The Impact of Cyber Security Threats on the Automotive Industry

In an era marked by rapid technological advancements, the automotive industry is undergoing a transformative shift. With the advent of connected vehicles, autonomous driving, and integrated smart systems, vehicles have evolved from mere mechanical machines to sophisticated computers on wheels. While this evolution brings remarkable benefits, it also introduces a new frontier of challenges, primarily in the realm of cyber security. This blog explores the growing influence of cyber security threats on the automotive industry and the measures being taken to address these challenges.
The Rise of Connected Vehicles and Vulnerabilities
Connected vehicles have become a symbol of convenience and innovation. However, the integration of internet connectivity into cars also presents a potential gateway for cyber attackers. Hackers can exploit vulnerabilities in infotainment systems, telematics, and communication protocols to gain unauthorised access to a vehicle’s network. This access could lead to unauthorised control over critical functions, jeopardising passenger safety.
Autonomous Vehicles and Their Security Quandaries
The pursuit of autonomous driving has further intensified the need for robust cyber security. Autonomous vehicles rely on an array of sensors, cameras, and data-sharing mechanisms to navigate roads safely. Any compromise in the integrity of these systems could result in accidents or even intentional harm. Protecting these vehicles from hacking attempts is crucial to ensure public trust and safety in this transformative technology.
Data Privacy and User Information
Connected vehicles generate an immense amount of data related to driving patterns, user preferences, and geolocation. This data is not only valuable for manufacturers but also for malicious actors seeking to exploit personal information for financial gain or other nefarious purposes. Ensuring the privacy of user data has become a significant concern, necessitating stringent data protection measures.

Supply Chain Vulnerabilities
The automotive industry relies on a complex global supply chain, which can inadvertently introduce vulnerabilities. If even a single component or software module is compromised at any point in the supply chain, it could potentially expose the entire vehicle fleet to cyber threats. Collaborative efforts between manufacturers and suppliers are essential to establish a chain of trust and enhance cyber security resilience.
Industry Response and Collaborative Initiatives
Recognising the severity of cyber security threats, the automotive industry has begun taking proactive measures. Collaboration between automakers, technology companies, and cyber security experts has led to the development of best practices, guidelines, and standards specifically tailored to the industry’s unique challenges. Organisations like the Automotive Information Sharing and Analysis Center (Auto-ISAC) have been established to facilitate information sharing and coordination among industry stakeholders.
Integration of Security by Design
To mitigate cyber security risks, manufacturers are increasingly adopting a “security by design” approach. This strategy involves integrating cyber security measures at every stage of a vehicle’s development lifecycle. From concept and design to manufacturing and maintenance, security considerations are embedded to create a holistic and robust cyber security framework.
The Comprehensive Solace Cyber Solution
As the automotive industry accelerates toward a future defined by connectivity and automation, the spectre of cyber security threats looms large. The intersection of technology and transportation has brought unprecedented conveniences and efficiencies, but it has also exposed vehicles to new forms of risk.
Organisational compute and infrastructure, such as classic on-premises server rooms, datacentres and cloud-based services are all subject to regular attack and the colocation of many services, often with network cross over between, has simply increased the scope and availability of a reachable threat surface.
By employing our Anticipate, Protect, and Respond strategy in the realm of cyber security, Solace Cyber has formulated a variety of service packages that can assist the industry in navigating this crossroad. These packages are built upon our core Real-time Risk Platform initially, scaling out to extend all the way up to our comprehensive safeguarding service suite of Solace Cyber Secure 360.
By acknowledging these challenges and collectively working towards innovative solutions we can build a safer and more secure automotive landscape for everyone.
Find out more about how Solace Cyber can support you on your cyber secure journey.
Request a free 30-minute consultation
If you’re concerned your business has fallen victim to a phishing or ransomware attack – get in touch with the incident response team today.